116 CyberCrime Topics & Essay Samples
If you are writing a cybercrime essay, our team prepared this article just for you. Here, you will find 115 unique topics for any type of paper.

140 Interesting Cybercrime Research Topics To Focus On
Table of Contents
Do you have to submit a cybercrime research paper? Are you looking for the best cybercrime research topics for your law assignments? Well, to help you out, here, we have compiled a list of interesting essays and research topic ideas on cybercrimes. Continue reading this blog post and gain unique ideas for writing a cybercrime research paper or an essay.
What is a Cybercrime?
Cybercrime is a criminal activity that is committed using a computer, a network, or a networked device. In recent times, the internet plays a vital role in the daily life of an individual. Particularly, a lot of financial transactions and data sharing are happening over the internet. So, considering that many cybercrimes are being carried out by cybercriminals for generating a profit. Basically, cybercrimes are of three categories.
- Crimes in which the computer is used as a weapon. E.g., launching a denial-of-service (DoS) attack, or malware attack.
- Crimes in which a computer or networked device is a target. E.g., gaining network access.
- Crimes in which a computer is used as an accessory to a crime. E.g., data theft, cyberstalking.
Under the above-mentioned categories, different types of cybercrimes are being carried out by cybercriminals. Cybercrimes include both monetary and non-monetary offenses. Mostly, cybercrimes result in damage to an individual, a device, or a government.
List of Cybercrimes
In the entire world, plenty of cybercrimes are happening. The masterminds behind all those dangerous crimes are the hackers with strong hacking and technical knowledge. Mainly, cybercrimes are carried out at locations where there is digital data.

Here is a list of some widely carried out cybercrimes across the world.
- Cyber Bullying
- Cyber Grooming
- Child Pornography
- Cyber Stalking
- Online Job Fraud
- Online Sextortion
- SIM Swap Scam
- Credit Card/Debit Card Fraud
- Impersonation/Identity Theft
- Viruses, Trojans, and Worms
- Online Drug Trafficking
- Data Breach
- Cryptojacking
- Cyber-Squatting
- Website Defacement
In order to prevent cybercrimes and reduce the risk of cyberattacks, cyber security is practiced. Also, to handle all the cybercrimes, each country has a separate cybercrime department and they follow strict cyber laws.
Cybercrime Research Topics and Ideas
Nowadays, a lot of questions are being raised about cybercrimes. To get answers for them all, conducting research is the only option. In case, you are asked to craft a cybercrime research paper on the topic of your preference, consider any topic related to common cybercrime cases such as personal data theft, financial theft, cyber-extortion, drug trafficking, and terrorism.

Are you a law student who has a keen interest to analyze and study cybercrimes? If yes, then the list of the best cybercrime research topics recommended below will be helpful to you. Without any hesitation, explore the full list and select any topic that is comfortable for you to analyze and write about.
Best Cybercrime Research Topics
- What is the role of America in protecting corporations from cybercrime?
- Have a close look at cybercrime, cyber forensics, and digital evidence.
- Is cybercrime the top IT threat?
- Write about the necessity of cyber security in preventing cybercrimes.
- Discuss the international laws and regulations related to cybercrime.
- Explain the effects of the UAE Cybercrime policy.
- What are the toolkits used in cybercrimes?
- Discuss the cybercrimes in Singapore.
- Write about UAE cybercrime laws.
- Explain the impact of cybercrime on the global criminal justice system.
- Have a detailed look at international cyberwar.
- Talk about Cybercrimes in the US.
- Discuss identity theft and cybercrime in contemporary society.
- Explain the significance of digital education and creating awareness of cybercrime.
- What are the effects of cybercrime on the world’s major countries?
- Explain UAE cybercrime laws.
- What is the need for cyber security in preventing cybercrimes?
- Discuss the role of America in protecting corporations from cybercrime.
- Importance of raising cybercrime awareness and digital education
- Analyze some recent cases of cybercrime in the banking industry and its consequences
- Discuss the impact of IP (intellectual property) rights, cyber piracy, and cybercrime on domestic and international business with the latest examples
- Critically analyze the degree and frequency of cybercrime in the United States
- Analyse the Cybercrime Legislation Amendment Act 2012(Cth) (CLAA)
- Compare and contrast the cybercrime prevention laws in India and the United Kingdom
- Analyze the Cybersecurity Laws and Regulations Report 2023 USA
- What are the key measures to undertake by a company to protect the cloud computing environment from cybersecurity issues?
- Identify and analyze the components of broadband industry structure and cybercrime
- Discuss the relationship between cybercrime, the economy, privacy, hacking, and terrorism
Good Cybercrime Essay Topics
- What are all the effects of cybercrime on the world’s major countries?
- Discuss the cybercrimes in the healthcare industry.
- Explain the developments in hacking.
- Discuss the trends of the future of good cybercrime.
- Write about Cybercrimes in Australia.
- What are the impacts of cybercrime on the banking industry?
- Is identity theft a cybercrime?
- Should capital punishment be given for cybercrime?
- Discuss the solutions for cybercrimes in Information Technology.
- Talk about cybercrime and social media.
- Explain the cybercrime challenges in public universities.
- Have a closer look at business fraud and cybercrime.
- Write about cybercrimes in India.
- Discuss terrorist cyberattacks with an example.
- Explain the impact of cybercrime on a government.
- Discuss the five biggest cyber security trends in 2022
- Remote working risks of cybersecurity
- Importance of Password-only Authentication in restricting cybercrime
- The Rise of Ransomware: Discuss
Unique Cybercrime Research Topics
- How to explain cybercrime using criminological theories ?
- How does crypto jacking work?
- Track the evolution of online scams.
- Analyze the implications of the Cyberpunk 2077 leak.
- How do cybercrimes afflict retail shops?
- What are man-in-the-middle attacks?
- What are the various phases of a DDoS attack?
- How to mitigate a denial-of-service attack?
- Analyze the success rate of email scams.
- Describe the working of WannaCry malware.
- Describe what happens during a Brute Force attack.
- How does ransomware work?
- How to protect children from cyberbullying?
- Have a closer look at big data and increased cybercrimes.
- Compare various types of fraud methods.
- What are identity theft and cybercrime in contemporary society
- Discuss the statistics on cybercrime as well as Fraud
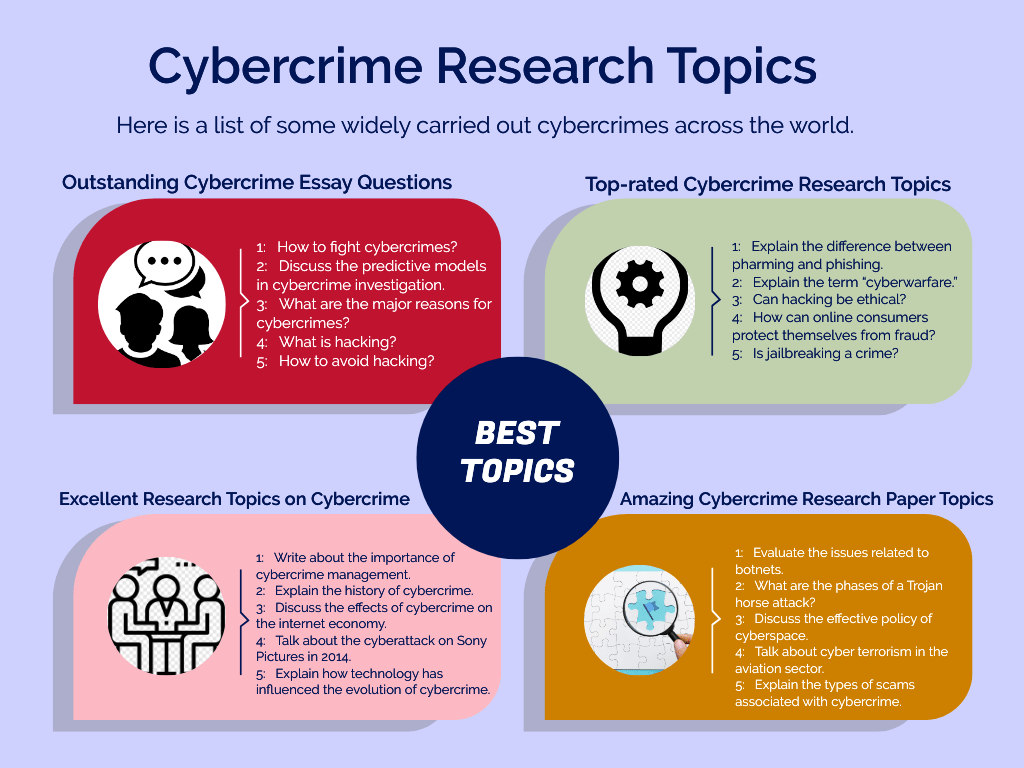
Outstanding Cybercrime Essay Questions
- How to fight cybercrimes?
- Discuss the predictive models in cybercrime investigation.
- What are the major reasons for cybercrimes?
- What is hacking?
- How to avoid hacking?
- Whose responsibility is cybercrime?
- Discuss the cost of cybercrime and digital spying.
- How does cybercrime affect domestic and foreign business?
- How to investigate cybercrime?
- Discuss the link between fraud and invisible attackers.
Top-rated Cybercrime Research Topics
- Explain the difference between pharming and phishing.
- Explain the term “cyberwarfare.”
- Can hacking be ethical?
- How can online consumers protect themselves from fraud?
- Is jailbreaking a crime?
- How can parents monitor their children’s behavior on the web?
- How to prevent cyberbullying in the online learning environment?
- Would cyber communism decrease bullying?
- Discuss the connection between political protests and hacking.
- Talk about the mental health effects of internet bullying.
- Who is responsible for online misbehavior?
- Who are white hat and black hat hackers?
- Explain the effects and solutions of catfishing.
- Should schools teach online etiquette?
- Does internet anonymity bring out the worst in people?
- How to stay safe online?
- How does a firewall help to protect the network?
- Explain how cyberbullying differs from in-person harassment.
- How to cope with online harassment?
- Write about phishing and scam on the internet.
Also read: Best Cybersecurity Research Topics for Students to Consider
Excellent Research Topics on Cybercrime
- Write about the importance of cybercrime management.
- Explain the history of cybercrime.
- Discuss the effects of cybercrime on the Internet economy.
- Talk about the cyberattack on Sony Pictures in 2014.
- Explain how technology has influenced the evolution of cybercrime.
- Discuss the social effects of cyberbullying on children.
- What are the signs of phishing attempts?
- What emergency action should an individual take after being hacked?
- Research and explain the significant cyber threats to US national security.
- Different types of cybercriminals.
- How do private sectors battle cybercrimes?
- Discuss the impacts of mobile devices on cyber security.
- Take a closer look at cyberfeminism and social media.
- Compare the functions of various antivirus programs.
- Discuss the pros and cons of various InfoSec certificates.
Amazing Cybercrime Research Paper Topics
- Evaluate the issues related to botnets.
- What are the phases of a Trojan horse attack?
- Discuss the effective policy of cyberspace.
- Talk about cyber terrorism in the aviation sector.
- Explain the types of scams associated with cybercrime.
- Discuss the potential effects the cyber currencies have on South African Businesses.
- How the automotive software of smart cars can be protected from cyberattacks?
- Discuss the effects of cyberbullying on teen suicides.
- Have a closer look at the cyber policy and strategy of the United Kingdom.
- What are the dangers of public Wi-Fi networks?
High-quality Cybercrime Research Ideas
- Describe the technology of unlocking a phone through facial recognition and the fingerprint of the owner of the phone
- Select a company from the United States and discuss their efforts and strategies to ensure cyber security
- Discuss the reasons that make every individual aware when it comes to safeguarding and protecting personal data and information from hackers
- Face recognition vs. a simple security code vs. fingerprint: Which is the safest locking option for smart devices and why?
- The increasing use of the internet consecutively increases the likelihood of adolescents and young adults engaging in cybercrime-related activities (e.g., email and internet fraud, identify fraud)
- Compare and contrast the effects of Phishing Emails, DoS (Denial of Service) Attacks, and Social Engineering
- Describe the history of cybercrime and the way cybercriminals have introduced different strategies to commit such crimes over the past decades
- Discuss the similarities and differences between distributed denial-of-service (DDoS) attacks and DoS (Denial of service) attacks
- Examination of the consequences a community or society would have to bear in case a hacker targeted the entire state
- Is purchasing from e-commerce sites such as eBay, Amazon, and Craigslist more ethical and safe compared to buying from other online marketplaces? Explain with reasons and the cyber security strategies of the aforementioned sites.
Impressive Cybercrime Research Topics
- Explain the importance of parental control mechanisms on children’s computers.
- What are effective strategies to cope with online harassment?
- Establish a link between feminism and the fight against cyberstalking.
- Analyze online gaming behavior from a psychological standpoint.
- How did industrial espionage evolve into hacking?
- Describe how an SQL injection attack unfolds.
- What are the safest ways to ensure data integrity?
- Discuss the pros and Cons of various cryptographic methods.
- How can a person reach maximum technological security?
- Explain the mechanics of password protection.
From the list of ideas suggested above, choose any topic that matches your requirements and craft a detailed cybercrime research paper with proper citations and proofs to prove your thesis statement. In case, you need an expert to offer you help with cybercrime research paper topic selection and writing, get in touch with us immediately.

Related Post

110 Hard Words to Spell for Students and Adults

Learn How to Avoid Passive Voice in 3 Simple Steps

117 Best Greek Mythology Essay Topics For Students
About author.
Jacob Smith
I am an Academic Writer and have affection to share my knowledge through posts’. I do not feel tiredness while research and analyzing the things. Sometime, I write down hundred of research topics as per the students requirements. I want to share solution oriented content to the students.
Comments are closed.
- Featured Posts
140 Unique Geology Research Topics to Focus On
200+ outstanding world history topics and ideas 2023, 190 excellent ap research topics and ideas, 150+ trending group discussion topics and ideas, 170 funny speech topics to blow the minds of audience, who invented exams learn the history of examination, how to focus on reading 15 effective tips for better concentration, what is a rhetorical analysis essay and how to write it, primary school teacher in australia- eligibility, job role, career options, and salary, 4 steps to build a flawless business letter format, get help instantly.
Raise Your Grades with Assignment Help Pro
- How it works

Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

5 Dissertation Topics on Cyber Crime
Published by Owen Ingram at January 9th, 2023 , Revised On August 15, 2023
Introduction
Any crime that is conducted using a computer and a network is known as cybercrime. Cybercrimes can target individuals in their personal capacity by targeting their property, the person himself, harming their mental health, and can even cause damage to governments.
Everyone using a computer and the internet can fall victim to cybercrime; however, understanding these crimes’ nature and how these are conducted can help people keep themselves safe and avoid falling victim.
Networks have weak spots, thus identifying those that can help you in determining possible attack points. This will eventually enable you to keep yourself safe from cybercrimes. Keeping your personal information safe at all times is critically important.
Never give out your passwords or any other personal information openly on any forum. This is one of the most effective ways of avoiding falling victim to cybercrime.
Being a pressing issue, cybercrime is continuously explored as to how it is conducted, what its types are, how it can be detected, how people can stay safe, etc. Here are five dissertation topics on cybercrime that will help gain an in-depth understanding of the issue.
These topics have been developed by PhD-qualified writers of our team , so you can trust to use these topics for drafting your dissertation.
You may also want to start your dissertation by requesting a brief research proposal from our writers on any of these topics, which includes an introduction to the topic, research question , aim and objectives , literature review along with the proposed methodology of research to be conducted. Let us know if you need any help in getting started.
Check our dissertation examples to get an idea of how to structure your dissertation .
Review the full list of dissertation topics for 2022 here.
5 Dissertation Topics on Cyber Crime 2022
Topic 1: is cybercrime a threat to banking sector in developing countries a case study of banking sector in pakistan.
Research Aim: This study aims to analyze the impact of cybercrime on the banking sector in developing countries. It will identify the possible threats faced by the banking sector due to increasing cybercrimes. These threats are related to the information security of the banks in developing countries. This research will be using Pakistan as a case study to find the threats posed by cybercrime to fragile banking. And after identifying the threats, the study will try to recommend possible solutions to ensure information security.
Topic 2: Impact of Cybercrime on E-Governance. Is cybercrime affecting the Confidentiality of Government Data?
Research Aim: This research aims to find the impact of cybercrime on modern-day governance systems or e-governance. It will identify the possible hindrances caused by cybercrime in implementing effective e-governance. This research will also investigate the impact of cybercrime on the confidentiality of government data. And after investigating the impact of cybercrime on the confidentiality of government data, this research will recommend the modern-day practices used to maintain the security of the information.
Topic 3: Is Information Safe Today? A survey to find the impact of cybercrime on the information security of the businesses
Research Aim: This study aims to find the impact of cybercrime on the information security of modern-day businesses. It will be a survey-based study to find out the problems faced by modern-day businesses due to cybercrime. These problems include confidential information leakage, which can benefit the competitors in the market. And another major problem is data stealing. This study will identify all these problems. And it will also recommend modern-day solutions to increase the security of the information.
Topic 4: A Socio-Technological Examination of Cybercrime and Information Security in Nigeria
Research Aim: This current research intends to determine Nigerian society’s vulnerabilities to cybercrime and exploitation and the global information infrastructure in general. It also aims to determine the informal, social, and technical drivers of Nigerian cybercrime and cybersecurity. To examine Nigerian law enforcement agencies and cybersecurity stakeholders’ efforts to combat cybercrime and guarantee cybersecurity. This analysis provides an opportunity for legislators, policymakers, and law enforcement agencies can utilize the law to establish legally valid definitions of cybercrime and information security from sociological and technological points of view
Topic 5: Impact of Cyber laws on Information Security. A Cross-Country Analysis
Research Aim: This study aims to analyse the impact of cyber laws on information security. This study is a cross-country analysis that will find the effectiveness of cyber laws across countries. It will see how over time, the introduction of cyber laws has affected information security after the find out the relationship between cyber laws and information security. This research will identify the most effective cyber laws in the countries under study. And after identifying the best laws among the countries under study. This study will recommend the best laws from individual countries or a set of laws from different countries.
Covid-19 Cyber Crime Research Topics
Topic 1: cybercrimes and coronavirus pandemic.
Research Aim: This study will focus on the increased cybercrimes during the coronavirus pandemic and the effective ways to overcome them.
Topic 2: Cybersecurity and COVID-19
Research Aim: This study will focus on the role of cybersecurity in minimizing cybercrimes during the crisis of the pandemic.
Topic 3: Cyber threats can harm industries
Research Aim: This study will address the growing cyber threats during COVID-19, where remote work has been adopted to combat the pandemic. It’ll highlight the threats, their harmful effect, and their solution.
Cyber Crime Research Topics 2021
Topic 1: importance of password security.
Research Aim: This research aims to identify the importance of Password security in safe computing.
Topic 2: Phishing scams
Research Aim: This research aims to highlight phishing scams issues and suggest various tips to avoid such scams.
Topic 3: Mobile protection
Research Aim: This research aims to highlight mobile security threats and suggest possible ways to protect mobile phones from hackers.
Topic 4: How to ensure safe computing?
Research Aim: This research will focus on types of hackings, scams and suggests possible ways to ensure safe computing
Topic 5: Cybercrime Dissertation Topics – The Evolution of Cyber Crime and the Attacks that Led to the Formation of Cyber Crime Policies
Research Aim: This dissertation will focus on the history of how this crime came into existence. The thesis’s main focus will be on understanding cybercrime, how it is being conducted worldwide, and what has led to an increase in these types of attacks.
The thesis will also discuss the initial attacks due to which cybercrime policies came into place. All policies will be discussed as to how they help curb cybercrimes and the extent to which they have been successful in reducing them.
Finally, the thesis will suggest if any new policies must be developed. What aspects need to be focused on, are there any new areas that need attention, or do the existing policies need to be revised?
Topic 6: Cybercrime Dissertation Topics – Cyber Crime: How it Impacts Young Adults
Research Aim: Cybercrime can have a great impact on the younger generation. Young adults use the internet more than any other age group, which is why they are the first victims of cybercrime. This dissertation will explore how cybercrime affects the younger generation and how it causes problems for them.
Issues such as health, specifically mental health, will be discussed to understand the many problems caused by cybercrime. Many individuals from the younger generation have attempted suicide after falling victim to cybercrime.
This research study will discuss all such effects of cybercrime, including cyberbullying (a form of cybercrime). The study will also present ways as to how they can avoid falling victim to cybercrime.
How Can ResearchProspect Help?
ResearchProspect writers can send several custom topic ideas to your email address. Once you have chosen a topic that suits your needs and interests, you can order for our dissertation outline service which will include a brief introduction to the topic, research questions , literature review , methodology , expected results , and conclusion . The dissertation outline will enable you to review the quality of our work before placing the order for our full dissertation writing service !
Topic 7: Cybercrime Dissertation Topics – Investigating Various Approaches and Ways to Detect Cyber Crime
Research Aim: Cybercrime, one of the most secret crimes, is spread all over the world. The number of cybercrimes worldwide is on the rise. Thus, every individual using a computer and connected to a network must be aware of the different types of cybercrimes.
Before discussing the different ways to detect cybercrime, this dissertation study will briefly discuss the many cybercrime types. Essentially, the research will focus on various ways through which each form of cybercrime can be detected.
Different forms of cybercrimes can be detected differently. For instance, data theft can be determined by asking for a password or other sensitive information through a call or an email. The research will then conclude how people can identify different forms of cybercrime and not fall victim to any of them.
Topic 8: Cybercrime Dissertation Topics – Evaluating Existing Cyber Crime Policies: Do They Suffice in Today’s World?
Research Aim: Cybercrime, being a major cause of concern throughout the world, is controlled and curbed by different policies in place. These policies are designed to make sure that cybercrime is reduced and gradually eliminated from society. However, with the increased numbers, the need for a policy change or amendment seems inevitable.
This means that the existing policies need to be reworked or revised, or abandoned completely, and new policies should be formed. This dissertation will investigate both these options and emphasize whether policies should be revised or new policies should be formed.
If new policies should be formed, the research will explain how these should be shaped, and if they need to be revised, then which aspects need to be considered for amendments will be the main focus of the dissertation. A detailed analysis will be presented to make an informed decision.
Topic 9: Cybercrime Dissertation Topics – Understanding the Different Types of Cyber Crime
Research Aim: Cybercrime, undoubtedly, is one of the most deadly forms of crime. Without causing physical harm, the crime causes the victim to attempt suicide or suffer from mental diseases such as anxiety, depression, etc.
This research will focus on the different types of cybercrimes that impact people in today’s world. This research will highlight almost all cybercrime forms while emphasising the most common forms such as cyberbullying, hacking, data theft, child pornography, etc.
In-depth research will be conducted through surveys and by using numbers and percentages of cybercrime from credible resources such as government websites, etc.
This will help understand the various forms of cybercrime, how widespread the crime is, and how many people are impacted by cybercrime throughout the world.
Important Notes:
As a cybercrime student looking to get good grades, it is essential to develop new ideas and experiment with existing cybercrime theories – i.e., to add value and interest to your research topic.
The field of cybercrime is vast and interrelated to so many other academic disciplines like Facebook , Instagram , Cryptocurrency , Twitter , civil engineering , facial recognition , construction , project management , engineering management , healthcare , finance and accounting , artificial intelligence , tourism , physiotherapy , sociology , management , and project management , graphic design , and nursing . That is why it is imperative to create a project management dissertation topic that is articular, sound, and actually solves a practical problem that may be rampant in the field.
We can’t stress how important it is to develop a logical research topic based on your entire research. There are several significant downfalls to getting your topic wrong; your supervisor may not be interested in working on it, the topic has no academic creditability, the research may not make logical sense, and there is a possibility that the study is not viable.
This impacts your time and efforts in writing your dissertation as you may end up in the cycle of rejection at the initial stage of the dissertation. That is why we recommend reviewing existing research to develop a topic, taking advice from your supervisor, and even asking for help in this particular stage of your dissertation.
Keeping our advice in mind while developing a research topic will allow you to pick one of the best cyber crime dissertation topics that fulfil your requirement of writing a research paper and add to the body of knowledge.
Therefore, it is recommended that when finalizing your dissertation topic, you read recently published literature to identify gaps in the research that you may help fill.
Remember- dissertation topics need to be unique, solve an identified problem, be logical, and be practically implemented. Please look at some of our sample cybercrime dissertation topics to get an idea for your own dissertation.
How to Structure your Cyber Crime Dissertation
A well-structured dissertation can help students to achieve a high overall academic grade.
- A Title Page
- Acknowledgements
- Declaration
- Abstract: A summary of the research completed
- Table of Contents
- Introduction : This chapter includes the project rationale, research background, key research aims and objectives, and the research problems. An outline of the structure of a dissertation can also be added to this chapter.
- Literature Review : This chapter presents relevant theories and frameworks by analysing published and unpublished literature available on the chosen research topic to address research questions . The purpose is to highlight and discuss the selected research area’s relative weaknesses and strengths whilst identifying any research gaps. Break down the topic, and key terms that can positively impact your dissertation and your tutor.
- Methodology : The data collection and analysis methods and techniques employed by the researcher are presented in the Methodology chapter which usually includes research design , research philosophy, research limitations, code of conduct, ethical consideration, data collection methods, and data analysis strategy .
- Findings and Analysis : Findings of the research are analysed in detail under the Findings and Analysis chapter. All key findings/results are outlined in this chapter without interpreting the data or drawing any conclusions. It can be useful to include graphs, charts, and tables in this chapter to identify meaningful trends and relationships.
- Discussion and Conclusion : The researcher presents his interpretation of the results in this chapter, and states whether the research hypothesis has been verified or not. An essential aspect of this section of the paper is to draw a linkage between the results and evidence from the literature. Recommendations with regards to implications of the findings and directions for the future may also be provided. Finally, a summary of the overall research, along with final judgments, opinions, and comments, must be included in the form of suggestions for improvement.
- References : This should be completed following your University’s requirements
- Bibliography
- Appendices : Any additional information, diagrams, and graphs used to complete the dissertation but not part of the dissertation should be included in the Appendices chapter. Essentially, the purpose is to expand the information/data.
About ResearchProspect Ltd
ResearchProspect is the world’s best academic writing service that provides help with Dissertation Proposal Writing , PhD Proposal Writing , Dissertation Writing , Dissertation Editing, and Improvement .
Our team of writers is highly qualified. They are experts in their respective fields. They have been working in the industry for a long, thus are aware of the issues and the trends of the industry they are working in.
Free Dissertation Topic
Phone Number
Academic Level Select Academic Level Undergraduate Graduate PHD
Academic Subject
Area of Research
Frequently Asked Questions
How to find dissertation topics on cyber crime.
To find dissertation topics on cybercrime:
- Study recent cyber threats and attacks.
- Analyze legal and ethical aspects.
- Explore technological advancements.
- Investigate prevention measures.
- Consider international perspectives.
- Select a focused area of interest for in-depth research.
You May Also Like
For any company and organisation, one of the most important yet sensitive assets is its information. Therefore, it is essential to keep the data secured from getting stolen and avoid getting it used for malicious activities.
Need interesting and manageable Marketing dissertation topics or thesis? Here are the trending Operations Marketing dissertation titles so you can choose the most suitable one.
Medical law becomes increasingly important as healthcare dominates as a social issue. Graduate students must select a thesis subject as part of their programs. The subject you choose must have sufficient data to support your thesis.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
70 Intriguing Cybercrime Research Topics and Ideas
Table of Contents
An Overview of Cybercrime Research
Around the world, technology-related crimes have increased significantly, especially since the introduction of smart devices and the internet. Thus, each nation has a specific set of cyber laws to address and deter cybercrimes. On the other hand, extensive cybercrime research is also being carried out in the unexplored areas of cyber laws and technology to manage real-world scenarios. If you are a student pursuing a course in criminology, law, or cybersecurity, then you may also work on compelling cybercrime research topics and figure out a solution for unsolved cases.
Cybercrime is a vast discipline that deals with a variety of crimes committed with the help of a networked device, computer, or the internet. When it comes to cybercrime dissertation preparation, you may consider any topics ranging from cyberbullying to phishing and data breaches. Since the subject is broad, it might be challenging for you to handle the cybercrime dissertation topic selection phase. Therefore, in this blog, we have analyzed and prepared a list of unique cybercrime research ideas. Additionally, we have also discussed how to choose an ideal topic and prepare a great cybercrime dissertation.
Explore this blog and get exclusive cybercrime research paper topics.
What is Cybercrime and its Types?
Cybercrime is a serious crime conducted with a networked device or computer for any purpose by individuals with significant hacking and technological skills. Such individuals are referred to as cyber criminals. Every day, a large number of cybercrimes are reported worldwide.
The prime target of cybercriminals is a victim’s money or personal information. So, many types of cybercrimes are being committed on sites where a high volume of digital data is present and money transaction occurs. Often, cyber crimes are intended to harm an individual, a government, an organization, or a device. It covers both monetary and non-financial offenses.

Typically, cybercrimes are classified into three types
- Crimes where a computer is used as a lethal weapon. For example, launch a denial-of-service (DoS) or malware assault.
- Offenses against computers or networked devices. For example, accessing an individual or company’s network.
- Crimes that are committed using computers, smartphones, or the internet as tools. Examples: cyberstalking and data theft.
The following are some dangerous cybercrimes committed worldwide – credit/debit card fraud, sexting, spamming, espionage, child pornography, SIM swap scams, cyber grooming, and so on.
Know How to Select a Cybercrime Research Topic
To prepare a remarkable cybercrime dissertation, it is essential to pick an outstanding research topic. For instance, you may focus on unique research ideas on emerging threats, prevention, and influence of cybercrimes.
If you are clueless about how to choose a perfect cybercrime research topic, follow these steps
- Identify your interest: First, find out the area in which you are interested in conducting cybercrime research. Your research process will be enjoyable if you work on your passion.
- Collect research ideas: Next, on your field of interest, brainstorm and generate potential cybercrime research paper topics
- Narrow down the focus: Analyze all the gathered ideas and then refine the list based on your objectives. Eliminate all the topic ideas that fail to meet your specifications.
- Pick a specific topic: From the narrowed-down list, select one topic that looks perfect to you. The topic you choose should be interesting, original, and meaningful. Furthermore, it should allow you to conduct an in-depth examination before the deadline and contain the necessary resources to support your claims.
- Get feedback: Lastly, after you pick a topic, consult with subject experts and receive their feedback. This will be helpful for you to achieve your desired results.
Also Read: 70 Best Criminal Psychology Research Topics and Ideas
Learn How to Structure a Cybercrime Dissertation
After you choose an appropriate study topic, conduct a literature review and then perform a deep analysis of the data you have collected through a specific research methodology. Once you finish your investigation, structure your cybercrime dissertation by including the following sections.
- Introduction: In this section, introduce your topic, clarify your research questions, and provide an overview of the dissertation’s structure.
- Literature Review: Here, provide an overview of earlier studies and theories related to cybercrime.
- Methodology: In this part, explain your investigative methods and validate your choices.
- Results: Here, present the findings from your research.
- Discussion: In this section, explain your findings in terms of your research questions and existing literature.
- Conclusion: Here, provide a summary of your research, discuss its limitations and recommendations, and suggest areas for additional study.
- References: At the end, list all the official resources you have used.

List of the Best Cybercrime Research Topics and Ideas
For writing a cybercrime research paper, you can select any topics related to cybercrime cases such as personal data financial theft, cyber-extortion, terrorism, and drug trafficking. In case, you run short of ideas, explore the list below. In the list, you will get exclusive research topic ideas on cybercrime and its associated areas.
Unique Cybercrime Research Topics
When it comes to writing a cybercrime thesis, avoid picking the most frequently discussed topics. Instead, take into account any original ideas on cybercrime that provide new information. Find here, some unique cybercrime research paper topics to get started.
1. Brute Force Attack: Conduct a Deep Analysis
This essay aims to explain what happens during a Brute Force attack. Focus on its causes and consequences.
2. Cyber Attack on Sony Pictures: Explore the Case
This paper analyzes the cyber attack on Sony Pictures in 2014. Also, it presents a detailed evaluation of how and why the attack has happened.
3. Gary McKinnon’s Hacking Event: Explain
In this research paper, explain Gary McKinnon’s Hacking Event. Describe the features and other specialties of the event.
4. How to Execute Phishing: Describe the Ways
This paper aims to present a detailed explanation of the different ways to execute phishing.
5. Legal Issues with Cybercrime Investigations: Explain
The objective of this essay is to explain the legal issues that are associated with cybercrime investigations.
6. Spread of Cybercrime: Contributions of Social Media
The primary goal of this paper is to explain how social media has contributed to the spread of cybercrime. Also, analyze the drawbacks of it.
7. Solutions for Cybercrimes in Information Technology
This paper explores and identifies the solutions available for cybercrimes in Information Technology.
Simple Cybercrime Research Topics for Students
In general, it might be more challenging to work on complex research topics. So, to effortlessly handle your tasks, you can work on simple cybercrime research questions. The following are some simple research ideas on cybercrime.
- What are the toolkits used in cybercrimes?
- Explain UAE cybercrime laws.
- What are the effects of the UAE Cybercrime policy?
- Explain the effect of cybercrime on the global criminal justice system.
- Write about the cybercrimes in Singapore.
- Analyze cybercrime, cyber forensics, and digital evidence.
- What is the need for cyber security in preventing cybercrimes?
- Discuss the role of America in protecting corporations from cybercrime.
- Explain the international laws and regulations related to cybercrime.
- Is cybercrime the top IT threat?
- Have a closer look at cybercrimes in the US.
- Explain the benefits of digital education and creating awareness of cybercrime.
- Write about international cyber war.
- Discuss the effects of cybercrime on the world’s major countries.
- Explain identity theft and cybercrime in modern society.
Great Cybercrime Research Topics for College Students
If you wish to compose a top-score fetching cybercrime research paper, then give preference to great topics that are not explored much. The following are a few outstanding cybercrime topics to research and write about.
- Discuss the importance of password-only authentication in restricting cybercrime.
- Conduct a cross-country analysis of the influence of cyber laws on data security.
- Describe the various phases of a DDoS attack.
- Research and write about email scams.
- Explain man-in-the-middle attacks.
- How does WannaCry malware work?
- Explain crypto jacking.
- Research the implications of the Cyberpunk 2077 leak.
- What are the ways to explain cybercrime using criminological theories?
- Write about cybercrime auto fraud
- How do cybercrimes afflict retail shops?
- Explore the evolution of online scams.
- Write about the computer viruses involved in cybercrime.
- How much did digital spying cost?
- Discuss the effective ways to protect children from cyberbullying.
Fascinating Cybercrime Dissertation Ideas
Are you seeking the best research topics for creating a cybercrime dissertation? If yes, then access the collection of ideas below. All the ideas will help you to craft a detailed dissertation with proper evidence and examples.
- Explain how the increase in digital currencies affects the rate of cybercrime actions.
- Discuss cybersecurity measures against phishing attacks.
- Explore the psychology of cybercriminals.
- Analyze the impact of cybercrime on small and medium enterprises.
- Explain the role of AI in cybercrime detection and prevention.
- Focus on the legal and ethical challenges of cyber espionage.
- Take a look at international cooperation in combating cybercrimes.
- Explore the cybercrimes in the financial sector.
- Examine the different stages of ransomware attacks and their countermeasures.
- Research and write about the Dark Web.
- What are the cybercrimes involved in the healthcare industry?
- Analyze the RA 10175 cybercrime law critically
- Discuss the technological advancements in cybercrime
Informative Cybercrime Research Topics
The research paper that you create should widen your knowledge as well as your readers. So, it is always good to work on research ideas that provide new information. The following are some informative research ideas on cybercrime.
- Compare and contrast cyber security laws of the United States and Australia
- How to prevent cyberbullying in the online learning environment?
- What is the connection between political protests and hacking?
- How can parents monitor their children’s behavior on the web?
- Explain the dangers of public Wi-Fi networks.
- Explain how to cope with online harassment.
- Explain the term “cyberwarfare.”
- How can online consumers protect themselves from fraud?
- Compare pharming and phishing.
- Explain the phases of a Trojan horse attack.
Top-rated Research Ideas About Cybercrime
Instead of preparing research papers on old topics, give importance to the latest and trending cybercrime research ideas. For your convenience, here, we have shared a list of some top study topics on cybercrime.
- Explain the pros and cons of various infosec certificates.
- Compare the functions of various antivirus programs.
- Explain the effect of mobile devices on cyber security.
- Write about the advanced wireless hacking techniques.
- Explain the effective policy of cyberspace.
- Research the issues related to botnets.
- Write about the digital forensic examination of counterfeit documents.
- Discuss cyberterrorism in the aviation sector.
- How the automotive software of smart cars can be protected from cyberattacks?
- Explain the effects and solutions of catfishing.
The Bottom Line
From the list of ideas suggested above, pick any topic that excites you and begin preparing your cybercrime dissertation. When you work on cybercrime research topics, make sure to conduct an in-depth examination of the topic and address all the key points with valid supporting evidence. Remember, the dissertation that you create should be informative, and authentic. Most importantly, you will achieve the expected outcomes only if you submit a plagiarism-free cybercrime research paper according to university guidelines. So, act accordingly and make your work stand unique in the crowd.
Related Post

85 Fantastic Thesis Topics on Various Subjects

170 Best Business Law Paper Topics To Examine

160 Unique Philosophy Research Topics and Ideas
About author.
Jacob Smith
Jacob Smith guides students with writing research paper topics and theses at greatassignmenthelp.com. Read about the author from this page
https://www.greatassignmenthelp.com/
Comments are closed.
- Featured Posts
Top 100 Java Project Ideas for Beginners and Experts
200 impressive business essay topics, 175 unique bioethics topics to consider for academic paper, apa vs. mla: know the major differences between the citation styles, 88 intriguing victimology topics for academic writing, defining malleability as a personality trait essay, why teachers should encourage students to write assignments, 10 best paying jobs in basic industries, unbiased analysis: is homework slavery, struggling with assignments.
Expert Help for Your Academic Success
105 Cybercrime Essay Topics
🏆 best essay topics on cybercrime, ✍️ cybercrime essay topics for college, 🎓 most interesting cybercrime research titles, 💡 simple cybercrime essay ideas, ❓ cybercrime research questions.
- The Hacking of Yahoo in 2013 and 2014
- Significance of Computer Forensics to Law Enforcement
- Cybercrime and Its Impact on Society
- Ethics of Hacking and Cracking
- Cyber Security: The Nature and Scope of Cybercrime
- Computer Forensics Laboratory’ Legal Requirements
- The Cybercrime Effect on Public Administration
- Cybercrime From the Religious Viewpoint The paper focuses on identifying the points at which the religious worldview would be the most fitting for the cybercrime problem examination.
- Trends in Cybercrime and Society The internet has played a pivotal role in boosting science, business, and education. Nevertheless, the internet is an additional tool for committing many crimes.
- Cyber Crime : Issues and Threats Cyber crime involves the stealing or manipulation of information effectively distorting its values across global networks.
- Sexting and Related Cybercrime Legislation Sexting represents a relatively law phenomenon on the law, with specific legislation dealing with sexting and minors not being present in a majority of US states.
- Computer Forensics and Investigations A computer forensics examiner may be called to provide evidence and advice in a court of law. Before logs disappear, digital forensics investigators are required to capture them.
- Digital Forensic Examination of Counterfeit Documents A citizen has contacted the police regarding the selling of counterfeit public documents. The investigator contacted the computer forensic laboratory to examine the evidence.
- Computer Forensics for Solving Cyber Crimes This paper presents research about the deployment of computer forensics in solving cybercrime. The paper brings out a number of cases concerning crimes in the cyberspace.
- The Development of New Technologies: Wireless Hacking Techniques With the rapid development of new technologies, the safety of personal data is expected to increase. The purpose of this paper is to discuss some wireless hacking techniques.
- Gathering, Analyzing, and Presenting Digital Evidence: Computer Forensic Investigators This paper aims at accomplishing four tasks, which are to providing HCC Partners in Life with computer forensic services that would support a case in a court of law.
- St. Louis County’s Cybercrime Task Force Plan The current paper presents a plan for the development of a cybercrime task force for St. Louis County to assign priorities for the task force.
- Computer Forensics Investigation Plan The US Constitution prohibits employers from conducting searches on employees. However, the protection does not apply to private organizations.
- Cybercrime Legislation in the UAE, US and India The paper will narrow down to present similarities and differences between the cybercrime laws in UAE and the United States, and between the cybercrime laws in the UAE and India.
- The Phone Hacking Scandal Among the major news event in the recent few days was the phone hacking scandal that was linked to the News of the World; a tabloid newspaper in the United Kingdom (UK).
- Digital Forensics in Law Enforcement The paper shows that digital forensics in law enforcement is useful in collecting extra proof after an occurrence to support charges against a suspect.
- Network Security and Cyber Crime, Super-Highway Metaphor Some of the major practices that can be done in ensuring maximum data security and integrity is through making all the servers only accessible by the administrators of networks.
- Cybercrime: Categories and Challenges This essay introduces the concept of cybercrime, informs the reader of its categories, and mentions several challenges that cybercrime presents.
- Cybercrime and the Culture of Fear Sexual exploitation and other offenses against children remain tragic—in spite of their frequency—and those numbers have been diminishing since the advent of the internet.
- The Justifiability of Hacking and the Government’s Role This paper discusses privacy in the age of technologies, government hacking, the human right to privacy, and the need for government surveillance.
- IT Security: Hacking and Its Components The aim of this paper is to analyze hacking and its components, such as ethical hacking, and to manage cyber security, on the example of the University’s data break-in.
- Social Issues Surrounding Cybercrime Among many social problems that have already been discussed, the issue of rising cybercrime has been on my mind the most.
- Cybercrime and Ransomware: Literature Analysis Criminal justice and the processes that it involves is one of the most multi-layered, controversial, and ever topical areas of legal procedures in general.
- Researching of Cybersecurity and Cybercrime The paper will discuss the technology transfer processes followed by the funding sources for technologies in the cybersecurity field
- Cyber Law and Digital Forensic Science The advantage and disadvantage of external media at the same time is that information is easy to hide, steal, or destroy since it is located on a small object.
- Digital Forensics and Deoxyribonucleic Acid The practice of digital forensics involves analysis of data collected computing devices from a particular crime scene.
- Computer Forensics and Investigations: Basic Procedures In this paper, the author is going to show the basic procedures that ought to be undertaken while performing a digital forensic examination.
- Computer Forensics in the FCC vs. Jack Brown Case In the case of the FCC vs. Jack Brown, this will involve accessing the information that has been stored in different file formats.
- The Council of Europe Convention on Cybercrime of 2001 The Council of Europe Convention on Cybercrime was created to deal with what is well-thought-out to be a unique attribute of cybercrime.
- Cybercrime Legislation in the UAE, the US and the EU Cyber and computer crime definitions were developed after the enhancement of technology, and they improved after years of making proposals.
- Black Hat vs White Hat Hacking This paper explores hacking from the perspective of ethics. In this paper, white hat and black hat hackers are the ethical players and their actions will be tested for ethicality.
- The Greater Threat of Cybercrime Versus Cyberattack
- Cyber Bullying: Old Problem in New-Age Packaging – Cybercrime
- Capital Punishment for Cybercrime: The Case in Nigeria
- Bargaining Interpersonal Organization Accounts as a Form of Cybercrime
- Canada and China: Cybercrime and Cryptocurrency
- Corruption, Fraud, and Cybercrime as Dehumanizing Phenomena
- Cybercrime and Its Impact on International Business
- Explaining Cybercrime Using Criminological Theories
- Cybercrime: Fraud and Powerful Invisible Attacker
- Growth, Development, and Policing of Cybercrime in the 21st Century
- Cybercrime Has Become One of the Most Threatening Issues
- How Social Media Has Contributed to the Spread of Cybercrime
- Cybercrime: Identity Theft and New Criminal Opportunities
- The Crime Scene Characteristics for Cybercrime and the Process of Investigating It
- Cybercrime: Preventing the Horrific Crimes on the Internet
- The Protection From Cyberattacks and Cybercrime in Bangladesh
- Does the Pandemic Explain Recent Spikes in Cyber Crime?
- Cybercrime Prevention Measures: How to Avoid Hacking
- The Role of Digital Forensics in Solving Cybercrimes
- Cybercrime: The Latest Ways of Stealing Identity and Money
- Potential Impact of Cyber Crime on the Economy
- Cybercrime and Cyberpiracy Impact on Domestic and Foreign Business
- Cybercrime in the Banking Sector and Its Impact on the Banking Industry
- Development of the Prevention of Cyber Crime in Malaysia
- Good Cybercrime: Trends and Future
- The Solutions for Cybercrimes in Information Technology
- Cybercrimes, Their Types, and Measures That We Take to Keep Us Safe From the Happenings
- Peculiarities of Cybercrime and Security
- How Technology Has Influenced the Evolution of Cybercrime
- The Impact of Cybercrime on the Global Criminal Justice System
- Cybercrime and Society: Identity Theft
- Closing the Space Between Cybercrime and Cybersecurity
- A Fast-Growing Area of Cybercrime
- Cybercrimes: An Unprecedented Threat to Society
- Key Steps to Managing a Cybercrime Scene
- Rights to Anonymity in Cybercrime
- What Is the Role of America in Protecting Corporations From Cybercrime?
- Cybercrime and Its Effects on the World’s Major Countries
- Exploring Cybercrime: Realities and Challenges
- Cybercrime Trends: How to Protect Your Business
- The Rise of Cybercrime in the United States
- How the Russia-Ukraine Conflict Is Impacting Cybercrime
- Cybercrime: A Complete Guide to All Things Criminal on the Web
- Top 5 Cybercrimes and Prevention Tips
- How Does Cybercrime Impact Small Businesses?
- What Are the Different Types of Cybercrimes and Cybercriminals?
- Can We Tackle the Ever-Evolving Threat of Cybercrime?
- What Is the Difference Between Crime and Cybercrime?
- Is Cybercrime Civil or Criminal?
- Why Is Cybercrime Considered a Crime?
- When Did Cybercrime Become a Crime?
- How Can Cybercrimes Be Prevented?
- What Was the First Cybercrime?
- How Does Cybercrime Affect Human Rights?
- Who Is Responsible for Cybercrime?
- What Was the Biggest Cybercrime Ever?
- How Does Cybercrime Affect the Victim?
- What Are the Effects of Cybercrime on Society?
- Which Country Is Top in Cybercrime?
- Does Cybercrime Affect Social Media?
- Where Was the First Cybercrime?
- What Are the Major Categories of Cybercrimes?
- How Does Cybercrime Impact the Economy?
- Which City Is Famous for Cybercrime?
- Who Are the Victims of Cybercrime and Why?
- Are There Defining Characteristics of a Cybercrime?
- What Theory Best Explains Cybercrime?
- Is There a Difference Between Computer Crimes and Cybercrimes?
- What Is the Overlap Between Criminal Justice and Cybercrime?
Cite this post
- Chicago (N-B)
- Chicago (A-D)
StudyCorgi. (2022, June 5). 105 Cybercrime Essay Topics. https://studycorgi.com/ideas/cybercrime-essay-topics/
"105 Cybercrime Essay Topics." StudyCorgi , 5 June 2022, studycorgi.com/ideas/cybercrime-essay-topics/.
StudyCorgi . (2022) '105 Cybercrime Essay Topics'. 5 June.
1. StudyCorgi . "105 Cybercrime Essay Topics." June 5, 2022. https://studycorgi.com/ideas/cybercrime-essay-topics/.
Bibliography
StudyCorgi . "105 Cybercrime Essay Topics." June 5, 2022. https://studycorgi.com/ideas/cybercrime-essay-topics/.
StudyCorgi . 2022. "105 Cybercrime Essay Topics." June 5, 2022. https://studycorgi.com/ideas/cybercrime-essay-topics/.
These essay examples and topics on Cybercrime were carefully selected by the StudyCorgi editorial team. They meet our highest standards in terms of grammar, punctuation, style, and fact accuracy. Please ensure you properly reference the materials if you’re using them to write your assignment.
This essay topic collection was updated on December 27, 2023 .
For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics in 2024
Home Blog Security 60+ Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance

D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
- Cyber security and the law
- The future of cyber security
5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorisation Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
Home — Essay Samples — Law, Crime & Punishment — Crime — Cyber Crimes
Essays on Cyber Crimes
When it comes to writing an essay on cyber crimes, choosing the right topic is crucial. With the increasing prevalence of cyber crimes in today’s digital age, it is important to shed light on various aspects of this issue through well-researched and thought-provoking essays. By selecting the right topic, you can ensure that your essay captures the attention of your readers and provides valuable insights into the world of cyber crimes.
Choosing the right cyber crimes essay topic is important for several reasons. Firstly, it allows you to delve into a specific aspect of cyber crimes, providing in-depth analysis and understanding. Secondly, a well-chosen topic can help you demonstrate your knowledge and expertise in the field of cyber crimes. Lastly, by selecting an engaging and relevant topic, you can capture the interest of your readers and make a meaningful impact with your essay.
When it comes to choosing a cyber crimes essay topic, it is important to consider your interests, the relevance of the topic, and the availability of credible sources for research. Consider topics that are current and have a significant impact on society. Additionally, ensure that the topic is specific enough to allow for in-depth analysis, yet broad enough to provide various angles for exploration.
Recommended Cyber Crimes Essay Topics
If you are looking for essay topics related to cyber crimes, you have come to the right place. Below is a list of recommended cyber crimes essay topics, categorized for ease of selection. These topics cover a wide range of issues related to cyber crimes and provide ample opportunities for in-depth research and analysis.
Privacy and Data Protection
- The impact of data breaches on consumer privacy
- Legal and ethical considerations in data privacy
- The role of social media in compromising personal privacy
Cybersecurity and Hacking
- The evolution of hacking techniques and their impact on cybersecurity
- The role of artificial intelligence in cyber warfare
- The implications of ransomware attacks on businesses and individuals
Cyberbullying and Online Harassment
- The psychological impact of cyberbullying on adolescents
- Legal measures to combat online harassment and cyberbullying
- The role of social media platforms in addressing cyberbullying
Financial Fraud and Identity Theft
- The impact of identity theft on individuals and businesses
- The role of cryptocurrency in facilitating financial fraud
- Preventive measures for combating credit card fraud in the digital age
Cyber Warfare and State-Sponsored Attacks
- The implications of state-sponsored cyber attacks on international relations
- The role of cyber warfare in modern warfare strategies
- The legal and ethical considerations of cyber warfare
With these recommended essay topics, you can explore various aspects of cyber crimes and make a meaningful contribution to the discourse on this important issue. By selecting a topic that resonates with your interests and allows for in-depth research, you can create an impactful essay that sheds light on the complexities of cyber crimes in today’s digital landscape.
Cyber Crimes
The problem of cyber crimes, made-to-order essay as fast as you need it.
Each essay is customized to cater to your unique preferences
+ experts online
Cyber Terrorism as a Major Security Challenge
Cyber crimes and cyber security in modern world, cybercrime: theories and managing, the information age and cyber crimes, let us write you an essay from scratch.
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Online Threats: Geotagging, Email and Phishing
The cydercrime: hacking and cyberstalking, cyber crime: the meaning, types, and ways to avoid, review of types and categories of cyber crimes, get a personalized essay in under 3 hours.
Expert-written essays crafted with your exact needs in mind
Cybercrime in Banking Industry and Its Impacts on Banking Industry
Phishing attacks in social media, cybercrimes & ways to prevent them, privacy and cyber harassment, effects of cyber crime on social media, churchill and cyber attacks in russia, the role of digital forensic in solving cyber-crimes, cybercrime and society: identity theft, the potential impact of cyber crime on the economy, the detailing of cyberstalking, cyber warfare and espionage: country stance and solutions, cyber crime and internet privacy, what kind of ethical issues related to it we are facing today, overview of the common internet threats, the most damaging hackers' attacks in history, international cybercrime law: past, present, future perspectives, the differences and similarities between the real world and cyber space criminology, the reasons why we need cyber law, lack of protection as the main factor of identity theft, human rights on the digital era, relevant topics.
- Child Abuse
- Drunk Driving
- Serial Killer
- School Shooting
- Animal Cruelty
- Broken Windows Theory
- Gang Violence
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Bibliography
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
Cybersecurity Dissertation Topics
Cybersecurity is an incredibly interesting topic area to complete your dissertation in, with it becoming increasingly prominent as technology is so heavily integrated into our daily lifestyles. Cybersecurity is always around us, from simple security systems that protect our mobile devices to complex strategies to secure personal data for big corporations. This helps to provide an array of different opportunities for completing an engaging and innovative cyber security dissertation. Some of the most important topic areas that exist within the field of cybersecurity include cybersecurity and cryptocurrencies, cybersecurity’s impact on business and economics, the role of cybersecurity in world affairs, cybersecurity and cybercrime, and how cybersecurity connects with big data and the Internet of Things (IoT).
Cryptocurrencies
Business & economics, world affairs, big data & iot.
Cryptocurrencies are very much the trendy topic in the world of cyber right now, with there being numerous studies exploring various aspects of cryptocurrencies and blockchain technology. However, few of these aims to contextualise the link between these technologies and cybersecurity, both for how blockchain technology can enhance cybersecurity, and what cybersecurity strategies can be used to protect cryptocurrencies. The following topic titles provide engaging research reviews into these key areas.
- A historical overview on the development of cyber security to enhance cryptographic security of blockchain technologies.
- A critical analysis of cyber-attacks and cryptocurrencies.
- How can blockchain applications be used to support cyber security strategies to reduce the global threat of cybercrime?
- How can cryptocurrencies be regulated in the European Union: What is the mediating role of cyber security?
- Can blockchain technologies be used to front the new domain of cyber forensics?
- An analysis of the future of cryptocurrencies and the mediating influence this may have on the state of cyber security strategies.
Organisations are having to invest more and more of their financial resources into cybersecurity to protect both their systems and their customers’ data. This lends itself to many new study areas that aim to explore how cybersecurity can be managed in the organisational setting, and what the potential return on investment for these strategies is.
- An analysis of the mediating role of risk management on the implementation of a comprehensive cybersecurity strategy.
- The use of Virtual Private Networks to enable remote working: A review of critical cyber security implications for developing successful VPN systems.
- A critical analysis of the role of cybersecurity throughout the supply chain for enhancing supply chain performance and collaboration.
- What cyber security measures can Small and Medium Sized Enterprises use to enhance their data protection protocols and build customer confidence?
- A review of effective cyber security strategies for mitigating cybercrime risk to business operations and continuity.
- What costing and investment models can be applied to effectively analyse whether the implementation of cyber security measures provides a positive return on investment?
It is evident that cybersecurity forms a significant role in day-to-day lives, with this instantly highlighting the significance of it in world affairs. From managing Covid-19 vaccination plans to GDPR, it is vital to understand the mechanisms in which cybersecurity is used to supplement ongoing world affairs and global projects.
- The impact of Covid-19 on cybersecurity in an organisational context due to increased levels of remote working.
- How should global legislation be created to help improve cybersecurity and reduce growing levels of cybercrime across the developed world?
- Have the recently enacted General Data Protection Regulations had a significant improvement on the protection of personal data and helped to reduce cybercrime or identity theft?
- Cyber security in the developing world: A critical analysis of opportunities and current barriers to implementation.
- How can cyber security be used to enhance data protection through vaccination distribution programs to tackle the spread of Covid-19?
- Cyber security and International Relations: How do the USA, China, and Russia manage cyber security when interacting with one another?
One of the most commonly aligned topics with cybersecurity is cybercrime, with this becoming an even greater threat as more people work from home and live their lives through technology. However, just as technology evolves so does the nature of cybercrime, with this always presenting the opportunity to research new and innovative ways in which cybercrime can be halted with innovative cyber security strategies.
- The influence of cybersecurity of the elimination of cybercrimes: A case study of the Equifax cyber-attack.
- A historical review of cybercrimes between 1980 and 2020: A critical analysis on the evolution of cybercrime and what future threats may be.
- Novice strategies to protect against cybercrime: An analysis of how cybersecurity can be used by low-level knowledge computer users.
- The influence of cyber forensics in combating cybercrime and as a fundamental strategy within the scope of a cybersecurity system.
- What are the positive and negative impacts on the use of simulated phishing scams to build awareness of corporate cybercrime?
- New methods of cybercrime: How can cybersecurity strategies be used to protect mobile devices from the threat of cybercrime?
Finally, big data and IoT form an imperative role in both organisational and social lives, with cybersecurity being fundamental to protect these systems. As both of these concepts are relatively new, there is a broad scope to potentially evaluate and conduct a research study on.
- Determining effective cybersecurity strategies to support an integrated IoT system.
- How to utilise cybersecurity when managing big data: A critical analysis of the use of detection algorithms.
- An analysis of the mediating role of artificial intelligence in the development of comprehensive and autonomous cybersecurity systems.
- What is the influence of machine learning on the creation of effective cybersecurity systems: A critical analysis of the banking industry?
- A critical evaluation of the importance of integrating cyber security systems into big data analytics.
- An evaluation on the use of cyber security across multiple Internet of Things devices: What are best practice techniques?
You may also like


- USF Research
- USF Libraries
Digital Commons @ USF > College of Behavioral and Community Sciences > Criminology > Theses and Dissertations
Criminology Theses and Dissertations
Theses/dissertations from 2023 2023.
Efficacy of Online Social Movements for Sparking Change: The Case of the Missing Murdered and Indigenous Women Movement (#MMIW) , Kacy A. Bleeker
An Examination of Racial Disparities in Arrest Across Florida Counties, 1998-2018: A Test of the Racial Threat and Political Representation Hypotheses , Xavier D. Burch
The Invisible Victims of Commercial Sexual Exploitation: Boys and Their Barriers to Access to Services , Amanda L. Connella
Damned & Damned: Examining Vexatious Litigation and the Vexatious Litigant Statute in Florida Courts , Sarah L. Harper
The Contributions of Mental Health Issues, Traumatic Brain Injury, and Adverse Childhood Experiences to Recidivism Among Rural Jail Incarcerees , Lauren N. Miley
Assessing the Relationship Between True Crime Documentary and Podcast Consumption, Fear of Crime, and Protective Behaviors , Lauren A. Tremblay
Police Officers’ Perceptions of Gunshot Detection Technology , Courtney L. Weber
Theses/Dissertations from 2022 2022
A Macro Social Examination of the Relationship Between Disabilities and Crime Using Neighborhood and County Level Data , Natasha A. Baloch
Racial Differences in Perceptions of Sanction Severity , Sarah L. Franklin
Juvenile Homicide Offenders: A Life-Course Perspective , Norair Khachatryan
Exploring the Effectiveness of a Life-Skills Program in a Florida Prison Through a Social Bond and General Strain Theory Perspective , Danielle M. Thomas
Theses/Dissertations from 2021 2021
Clean Water for All: Examining Safe Drinking Water Act Violations of Water Systems and Community Characteristics , Junghwan Bae
Morality and Offender Decision-Making: Testing the Empirical Relationship and Examining Methodological Implications , Jacquelyn Burckley
The Ring of Gyges 2.0: How Anonymity Providing Behaviors Affect Willingness to Participate in Online Deviance , Cassandra E. Dodge
A Macro Analysis of Illegal Hunting and Fishing Across Texas Counties: Using an Economic Structural Approach , Leo J. Genco Jr.
Self-Protection in Cyberspace: Assessing the Processual Relationship Between Thoughtfully Reflective Decision Making, Protection Motivation Theory, Cyber Hygiene, and Victimization , C. Jordan Howell
Racial Threat Theory: A Test of the Economic Threat Hypothesis , Carl L. Reeds
Online Perceptions of Panamanian Prisons and Incarcerated persons: An analysis of YouTube user comments , Mahaleth J. Sotelo
Theses/Dissertations from 2020 2020
Toxic Colonialism and Green Victimization of Native Americans: An Examination of the Genocidal Impacts of Uranium Mining , Averi R. Fegadel
Cross-National Incarceration Rates as Behavior of Law , Christopher J. Marier
The Effects of Perceived Motivations and Mental Distress on the Likelihood of Reporting and Engaging in Self-Protective Measures Among Victims of Stalking , Daniela Oramas Mora
Mental Health and In-Prison Experiences: Examining Socioeconomic and Sex Differences in the Effect of Mental Illness on Institutional Misconduct and Disciplinary Segregation , Rachel E. Severson
Theses/Dissertations from 2019 2019
Dating Application Facilitated Victimization: An Examination of Lifestyle-Routine Activities, Self-Control, and Self-Efficacy , Vanessa Centelles
Social Constructionism and Cultivation Theory in Development of the Juvenile “Super-Predator” , Elizabeth R. Jackson-Cruz
Bystander Intervention, Victimization, and Routine Activities Theory: An Examination of Feminist Routine Activities Theory in Cyber Space , Jennifer A. Leili
Sexual Assault and Robbery Disclosure: An Examination of Black’s Theory of the Behavior of Law , Caitlyn N. Muniz
Mass Shootings and Gun Sales: A Study on the Influence of Red and Blue Power , Maria Jose Rozo Osuna
A Multi-dimensional Macrolevel Study of Drug Enforcement Strategies, Heroin Prices, and Heroin Consumption Rates , Alexander G. Toth
Theses/Dissertations from 2018 2018
The Impact of a Religious/Spiritual Turning Point on Desistance: A Lifecourse Assessment of Racial/Ethnic Differences , Rhissa Briones Robinson
Political Decisions on Police Expenditures: Examining the Potential Relationship Between Political Structure, Police Expenditures and the Volume of Crime Across US States , Xavier D. Burch
Identifying the Personal and Perceived Organizational Characteristics Associated with Job Satisfaction Among Juvenile Probation Staff , Julie M. Krupa
The Role of Organizational Justice in Predicting Attitudes Toward Body-Worn Cameras in Police Officers , Nathaniel L. Lawshe
Yet Another Ferguson Effect: An Exploratory Content Analysis of News Stories on Police Brutality and Deadly Force Before and After the Killing of Michael Brown , Carl Root
The Role of Race/Ethnicity and Risk Assessment on Juvenile Case Outcomes , Tayler N. Shreve
Theses/Dissertations from 2017 2017
Intimate Partner Violence and the Capacity and Desire for Self-Control , Krista Taralynne Brewer
School Shootings in the United States from 1997 to 2012: A Content Analysis of Media Coverage , Victoria N. Iannuzzi
Chronic Runaway Youth: A Gender-Based Analysis , Michelle N. Jeanis
A Test of Wikström’s Situational Action Theory Using Self-Report Data on Intimate Partner Violence , Lauren Nicole Miley
An Exploratory Study of Macro-Social Correlates of Online Property Crime , Hyojong Song
Female Incarceration and Prison Social Order: An Examination of Gender Differences in Prison Misconduct and In-Prison Punishments , Elisa L. Toman
Adverse Childhood Experiences and Their Role as Mitigators for Youthful and Non-Youthful Offenders in Capital Sentencing Cases , Jessica R. Trapassi
Theses/Dissertations from 2016 2016
Disinhibition, Violence Exposure, and Delinquency: A Test of How Self-Control Affects the Impact of Exposure to Violence , Wyatt Brown
The Guilty But Mentally Ill Verdict: Assessing the Impact of Informing Jurors of Verdict Consequences , Erin Elizabeth Cotrone
The Relationship between Psychopathic Personality Traits and Lying , Jason A. Dobrow
Delving into the Heart of Victimization Risk: Examining the Interactive Relationship between Demographic Factors and Context , Amy Sheena Eggers
A Power Conflict Approach to Animal Cruelty: Examining How Economic Power Influences the Creation of Animal Cruelty Laws , Leonard J. Genco
The Role of Gender in Self-Control and Intimate Partner Violence , Laura Marie Gulledge
The Restrictive Deterrent Effect of Warning Banners in a Compromised Computer System , Christian Jordan-Michael Howell
Tactics of Sexual Control and Negative Health Outcomes , Anna Elizabeth Kleppe
The Applicability of Criminology to Terrorism Studies: An Exploratory Study of ISIS Supporters in the United States , Amanda Marie Sharp Parker
The Path to Violent Behavior: The Harmful Aftermath of Childhood Trauma , Nicholas Michael Perez
The Effects of Racial Bias on Perceptions of Intimate Partner Violence Scenarios , Batya Yisraela Rubenstein
Theses/Dissertations from 2015 2015
Reel or Reality? The Portrayal of Prostitution in Major Motion Pictures , Raleigh Blasdell
Psychopathy and Perception of Vulnerability , Barbara Joyce Dinkins
Effect of Empathy on Death Penalty Support in Relation to the Racial Divide and Gender Gap , Brian Godcharles
Exploring the Interactive Effects of Social Learning Theory and Psychopathy on Serious Juvenile Delinquency , Brandy Barenna Henderson
Tampa Electric Company's Big Bend Utility Plant in Hillsborough County, Florida: A Case Study , Lynne M. Hodalski-Champagne
Thirty Year Follow-Up of Juvenile Homicide Offenders , Norair Khachatryan
Organized Crime in Insurance Fraud: An Empirical Analysis of Staged Automobile Accident Rings , Chris Longino
The Role of Social Support in the Disclosure and Recovery Process of Rape Victims , Jessica Nicole Mitchell
Evaluating the Social Control of Banking Crimes: An Examination of Anti-Money Laundering Deficiencies and Industry Success , Erin M. Mulligan
Elite Deviance, Organized Crime, and Homicide: A Cross-National Quantitative Analysis , Carol L.s. Trent
An Evaluation of the Utah First District Mental Health Court: Gauging the Efficacy of Diverting Offenders Suffering With Serious Mental Illness , Stephen Guy VanGeem
Rape, Race, and Capital Punishment in North Carolina: A Qualitative Approach to Examining an Enduring Cultural Legacy , Douglas Wholl
Theses/Dissertations from 2014 2014
The Tattoo: A Mark of Subversion, Deviance, or Mainstream Self-Expression? , Jocelyn Camacho
Juvenile and Adult Involvement in Double Parricide and Familicide in the U.S.: An Empirical Analysis of 20 Years of Data , Averi Rebekah Fegadel
Predicting Successful Drug Court Graduation: Exploring Demographic and Psychosocial Factors among Medication-Assisted Drug Court Treatment Clients , Autumn Michelle Frei
Experimentally Evaluating Statistical Patterns of Offending Typology For Burglary: A Replication Study , Lance Edwin Gilmore
Developmental Trajectories of Physical Aggression and Nonaggressive Rule-Breaking among At-risk Males and Females during Late Childhood and Early Adolescence , Eugena Givens
Predicting Fear of Crime using a Multilevel and Multi-Model Approach: A Study in Hillsborough County , Jonathan Maskaly
Public Knowledge and Sentiments about Elite Deviance , Cedric Michel
The Influence of Community Context on Social Control: A Multi-Level Examination of the Relationship between Race/Ethnicity, Drug Offending, and Juvenile Court Outcomes , Jennifer Peck
Theses/Dissertations from 2013 2013
Assessing the Relationship Between Hotspots of Lead and Hotspots of Crime , Kimberly L. Barrett
A Life-Course Approach to Sexual Offending: Examining the Continuity of Juvenile Sexual Offending into Adulthood and Subsequent Patterns of Recidivism , Maude Beaudry-Cyr
Examining the link between self-control and misconduct in a multi-agency sample of police supervisors: A test of two theories , Christopher Matthew Donner
The Impact of Hyperfemininity on Explicit and Implicit Blame Assignment and Police Reporting of Alcohol Facilitated Rape in a Sample of College Women , Sarah Ehlke
Rurality and Intimate Partner Homicide: Exploring the Relationship between Place, Social Structure, and Femicide in North Carolina , Amelia Kirkland
Self-Control, Attitudinal Beliefs, and White-Collar Crime Intentions , Melissa Anne Lugo
Zero Tolerance for Marginal Populations: Examining Neoliberal Social Controls in American Schools , Brian Gregory Sellers
State-Corporate Crime in the Democratic Republic of Congo , Veronica Jane Winters
Theses/Dissertations from 2012 2012
The Walls Are Closing In: Comparing Property Crime Victimization Risk In Gated And Non-Gated Communities , Nicholas Branic
What Propels Sexual Homicide Offenders? Testing an Integrated Theory of Social Learning and Routine Activities Theories , Heng Choon Chan
A Deadly Way of Doing Business: A Case Study of Corporate Crime in the Coal Mining Industry , Charles Nickolas Stickeler
Deconstructing the "Power and Control Motive": Developing and Assessing the Measurability of Internal Power , Shelly Marie Wagers
Theses/Dissertations from 2011 2011
Assessing racial differences in offending trajectories: A life-course view of the race-crime relationship , Michael S. Caudy
Mental Health Courts Effectiveness in Reducing Recidivism and Improving Clinical Outcomes: A Meta-Analysis , Brittany Cross
General Strain Theory and Juvenile Delinquency: A Cross-Cultural Study , Wen-Hsu Lin
General Strain Theory, Race, and Delinquency , Jennifer Peck
Developmental Trajectories of Self-Control: Assessing the Stability Hypothesis , James Vance Ray
Explaining the "Female Victim Effect" in Capital Sentencing Decisions: A Case for Sex-Specific Models of Capital Sentencing Research , Tara N. Richards
A Multilevel Model of Police Corruption: Anomie, Decoupling, and Moral Disengagement , Ruth Zschoche
Theses/Dissertations from 2010 2010
The Emotional Guardianship of Foreign-Born and Native-Born Hispanic Youth and Its Effect on Violent Victimization , Amy Sheena Eggers
The Influence of Narcissism and Self-Control on Reactive Aggression , Melissa L. Harrison
Is There an "Innocent Female Victim" Effect in Capital Punishment Sentencing? , Amelia Lane Kirkland
An Analysis of the Influence of Sampling Methods on Estimation of Drug Use Prevalence and Patterns Among Arrestees in the United States: Implications for Research and Policy , Janine Kremling
A Pathway to Child Sex Trafficking in Prostitution: The Impact of Strain and Risk-Inflating Responses , Joan A. Reid
Victimization Among Individuals With Low Self-Control: Effects on Fear Versus Perceived Risk of Crime , Casey Williams
Theses/Dissertations from 2009 2009
Domestic Violence Within Law Enforcement Families: The Link Between Traditional Police Subculture and Domestic Violence Among Police , Lindsey Blumenstein
Rape Attitudes and Beliefs: A Replication Study , Rhissa Emily Briones
Reel Images: Representations of Adult Male Prisons by the Film Industry , Melissa E. Fenwick
Advanced Search
- Email Notifications and RSS
- All Collections
- USF Faculty Publications
- Open Access Journals
- Conferences and Events
- Theses and Dissertations
- Textbooks Collection
Useful Links
- Rights Information
- SelectedWorks
- Submit Research
Home | About | Help | My Account | Accessibility Statement | Language and Diversity Statements
Privacy Copyright
Cyber Crime Essay for Students and Children
500+ words essay on cyber crime.
Cyber Crime Essay – Everybody thinks that only stealing someone’s private data is Cyber Crime. But in defining terms we can say that ‘Cyber Crime refers to the use of an electronic device (computer, laptop, etc.) for stealing someone’s data or trying to harm them using a computer.
Besides, it is an illegal activity that involves a series of issues ranging from theft to using your system or IP address as a tool for committing a crime.

Types of Cyber Crime
Speaking in a broadway we can say that Cyber Crime are categorized into four major types. These are Financial, Privacy, Hacking, and Cyber Terrorism.
The financial crime they steal the money of user or account holders. Likewise, they also stole data of companies which can lead to financial crimes. Also, transactions are heavily risked because of them. Every year hackers stole lakhs and crores of rupees of businessmen and government.
Privacy crime includes stealing your private data which you do not want to share with the world. Moreover, due to it, the people suffer a lot and some even commit suicide because of their data’s misuse.
In, hacking they intentional deface a website to cause damage or loss to the public or owner. Apart from that, they destroy or make changes in the existing websites to diminish its value.
Modern-day terrorism has grown way beyond what it was 10-20 years ago. But cyber terrorism is not just related to terrorists or terrorist organizations. But to threat some person or property to the level of creating fear is also Cyber Terrorism.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Crime in India
Web world or cyberspace is a massive community of millions and billions of users and websites. Also, people access it for different uses like shopping, movies, music, video games, transactions, and e-commerce, etc.

In this Age of Technology and easy access to the internet, anyone can easily reach it. Because of this fast pace growth from the previous decade. Besides, the internet has opened a world of information on which anyone can connect.
Due to, this the rate of crime especially the rate of Cyber Crime has increased much fold. Moreover, the rate of circulation of data is also increased much fold due to the higher speed of internet. Above all, due to all these issues, the Cybersecurity has become a major concern for society.
Laws related to Cyber Crimes
To stop the spread of Cyber Crime and to safeguard the interest of people the government has made several laws related to Cyber Crimes. Also, these laws serve as protection against Cyber Crime. Apart from that, the government has also introduced cyber cells in police stations to counter the problem of Cyber Crime as fast as they can.
Ways of stopping Cyber Crime
Cyber Crime is not something which we cannot deal with our self. Likewise, with little use of our common sense and logic, we can stop Cyber Crimes from happening.
To conclude, we can say that Cyber Crime is a dangerous offense to someone’s privacy or any material. Also, we can avoid Cyber Crime by following some basic logical things and using our common sense. Above all, Cyber Crime is a violation of not only law but of human rights too.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [{ “@type”: “Question”, “name”: “What is the main cause of Cyber Crime?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “The greed for quick money and the desire to get famous quickly are the two main reasons of Cyber Crime. Also, most of the targets of Cyber Crime banks, businessman, financial firms, etc.” } }, { “@type”: “Question”, “name”: “What is the punishment of Cyber Crime in India?”, “acceptedAnswer”: { “@type”: “Answer”, “text”:”If the person is found guilty then there are several punishments based on the level of crime. A simple crime can cost you a fine while a bigger crime can lead you to jail.”} }] }
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

- My Shodhganga
- Receive email updates
- Edit Profile
Shodhganga : a reservoir of Indian theses @ INFLIBNET
- Shodhganga@INFLIBNET
- Aligarh Muslim University
- Department of Law
Items in Shodhganga are licensed under Creative Commons Licence Attribution-NonCommercial-ShareAlike 4.0 International (CC BY-NC-SA 4.0).


University of Bridgeport News

Master’s in Criminal Justice Thesis Track vs. Internship Track
Candidates looking for a challenging, rewarding, and high-earning position in the criminal justice field usually find themselves pondering whether to return to school via a Criminal Justice Master’s degree program. In researching the decision, many candidates stumble upon the decision of choosing between a thesis track and an internship track of study.
Below, we’ll discuss the different types of Master’s in Criminal Justice degrees, including the Master’s in Criminal Justice thesis track program and the Master’s in Criminal Justice internship program, to help you determine which would be best for your career.
What is a Master’s in Criminal Justice?
A Criminal Justice Master’s degree, like the Master’s in Criminal Justice and Human Security program at University of Bridgeport, is designed to give students knowledge and expertise in the worldwide political, cultural, and socioeconomic conditions contributing to crime and its attenuation. These programs also focus on the cultural, ethnic, religious, and ideological differences commonly found at the crossroads of criminal acts, violence, and terror.
Program prerequisites for Master’s in Criminal Justice degrees vary depending on the college or university. At University of Bridgeport, for example, students must:
- Have a bachelor’s degree from an accredited university or recognized international institution
- Have a cumulative undergraduate GPA of 3.0 or higher
- Have two years of college-level language study or fluency in a second language (Students who have not completed this requirement but feel that they have language competency to this level may take an oral and written exam confirming such competency, or they may complete the language requirement at University of Bridgeport or another regionally accredited institution of higher education before the conclusion of the degree program.)
- Submit an application
- Submit a personal statement (250-500 words) detailing why they are seeking this degree, how you expect to apply your degree to your professional career after graduation, and why you desire to pursue your degree through University of Bridgeport
- Submit a resume
- Submit their official transcript for the last degree earned
- Submit two letters of recommendation commenting on your work ethic, communication skills, and ability to complete a graduate degree program.
Master’s in Criminal Justice Thesis track
Criminal Justice Master’s degree programs often offer students the opportunity to choose between a Master’s in Criminal Justice Thesis track program or a Master’s in Criminal Justice Internship program.
Both of these tracks include eighteen semester hours of core courses and eighteen semester hours of electives . These courses often cover in-depth topics, including:
- Cyberterrorism
- Domestic, international, and comparative criminal law
- Human security
- Transnational crime
Furthermore, the Master’s in Criminal Justice Thesis track, as the name suggests, requires students to dedicate multiple semesters to focus on research and data collection.
Upon completion of their research, each student is then required to write a large-formatted paper sharing their methods, data, and discovery to be published.
At University of Bridgeport, students in the Master’s in Criminal Justice Thesis track take the following courses:
- Criminal Justice Research Methods
- Human Security and Approaches to Justice
- Law Enforcement Management
- U.S. Law and Criminal Justice
Master’s in Criminal Justice Internship track
The Master’s in Criminal Justice Internship track is another popular and common option for students, especially those who want to gain hands-on experience or do not have the time or desire to conduct multi-semester research.
While students in non-thesis degree programs may be required to write papers or complete large projects, there are no expectations that these papers will be published.
Internship track programs, like the one at University of Bridgeport, allow students to intern during their final semesters of the program, giving them hands-on skills and experience to use in their future careers.
At University of Bridgeport, students in the Master’s in Criminal Justice Internship track take the same courses as students in the thesis track, but instead of a thesis, they take:
- CJHS 591 – Internship
- CJHS 598 – Tutorial
Thesis track vs. internship track: Which one is right for me?
Deciding whether to enroll in a Master’s in Criminal Justice thesis track degree versus a Master’s in Criminal Justice Internship track degree ultimately depends on a student’s needs, interests, and goals.
Both types of Master’s in Criminal Justice degrees can lead to exciting, fulfilling, and rewarding careers as:
- Correctional caseworker
- Criminologist
- Cybersecurity investigator
- Drug Enforcement Administration (DEA) Agents
- Federal Bureau of Investigation (FBI) Agent
- Federal Marshall
- Forensic psychologists
- Intelligence analyst
- Police supervisors and detective supervisors
If you want to pursue a research-heavy field, submit your writing to academic journals, or obtain a Ph.D., a Master’s in Criminal Justice Thesis track program would be the best fit. But if you do not enjoy writing and thrive on project-based, real-world assignments, a Master’s in Criminal Justice Internship Program is a great choice.
Earn your Criminal Justice Master’s degree at University of Bridgeport
No matter if you choose the thesis track vs internship track, University of Bridgeport’s Criminal Justice and Human Security Master’s degree program makes sure graduates are well-prepared and ready to work in the area of criminal justice, international security, defense, intelligence, and transnational crime prevention or deterrence anywhere in the world.
Financial aid is available , and our comprehensive support services are here to help you get through college and into a great career.
Apply today or contact us for more information . The completed application and all supporting documents for our Master of Arts (M.A.) in Criminal Justice and Human Security degree must be received by July 15th for the fall semester and December 1st for the spring semester.
We can’t wait for you to join the Purple Knight family!
Go to series
Tinder swindler: how 'romance fraud' became a multi-billion dollar cybercrime.
Scroll down for full podcast transcript - click the ‘Show more’ arrow
The Netflix documentary 'The Tinder Swindler' is a mind-boggling case of so-called 'romance fraud' in which a charming, handsome - and apparently very rich - man meets women on a dating app - gets them to fall in love with him - and then cons them out of lots of money.
Cecilie Fjellhøy is the Norwegian woman at the centre of the documentary whose life was torn apart by the actions of a conman. A survivor of romance fraud on a grand scale, she now advocates for the rights of, and support for, others who find themselves in similar grim circumstances.
We also hear from Sean Doyle, who works at the World Economic Forum’s Centre for Cybersecurity, on just how widespread romance fraud really is, why it’s a multinational, multi-billion form of cyber crime, and what is being done to combat it.
Centre for Cybersecurity: wef.ch/cybersecurity
Cybercrime Atlas: https://initiatives.weforum.org/cybercrime-atlas/
Cecilie Fjellhøy 's organisation LoveSaid: https://www.lovesaid.org/
The Tinder Swindler documentary:
Related podcasts:
Global Risks Report: the big issues facing leaders at Davos 2024
Ransomware and ransom-war: why we all need to be ready for cyber attacks
Check out all our podcasts on wef.ch/podcasts :
YouTube: - https://www.youtube.com/@wef/podcasts
Radio Davos - subscribe : https://pod.link/1504682164
Meet the Leader - subscribe : https://pod.link/1534915560
Agenda Dialogues - subscribe : https://pod.link/1574956552
Join the World Economic Forum Podcast Club : https://www.facebook.com/groups/wefpodcastclub
This transcript has been generated using speech recognition software and may contain errors. Please check its accuracy against the audio.
Cecilie Fjellhøy, co-founder, LoveSaid: I met him in person. Looked like his pictures. Really charming. Really opening up to me, like. So we had a coffee. He was talking about his job. He was the CEO of a big diamond company. On the first day I met him, we travelled on this private jet. I fell quickly and I fell hard.
Robin Pomeroy, host, Radio Davos : Welcome to Radio Davos, the podcast from the World Economic Forum that looks at the biggest challenges and how we might solve them. This week: the Tinder Swindler - you may have seen the unbelievable Netflix documentary about how this woman’s dream first date spiralled into a nightmare.
Cecilie Fjellhøy: They came to my work, two special security agents and told me that they had a long investigation on him. They asked for if I had a picture of him. When I showed them the picture they just looked at each other and they nodded. My life was just falling apart.
Robin Pomeroy: Far from a being a one-off case fueling the public’s appetite for bizarre true crime stories, ‘romance fraud’ is actually a global multi-billion dollar industry - part of the booming criminal business known as cyber crime
Sean Doyle, Centre for Cybersecurity, World Economic Forum : It's a very good example of cybercrime. It's playing on a very basic human need. The need to be loved has been around as long as people have been here. What's different? Why is romance fraud changed? Cyber-enabled fraud allows us to do these things at scale.
Subscribe to Radio Davos wherever you get your podcasts, or visit wef.ch/podcasts where you will also find our sister programmes, Meet the Leader and Agenda Dialogues.
I’m Robin Pomeroy at the World Economic Forum, and with this look at romance fraud, cybercrime and the real life case of the Tinder Swindler.
Cecilie Fjellhøy: Everyone thinks that this is old women, vulnerable, sitting at home knitting type of crime. But it's not.
Robin Pomeroy: Do you enjoy true crime documentaries? Maybe you caught this one on Netflix…
Tinder Swindler trailer: You can find a bit of everything on Tinder but one little swipe can change your life.
Robin Pomeroy: The Tinder Swindler is a mind-boggling case of romance fraud in which a charming, handsome - and apparently very rich - man meets women on a dating app - gets them to fall in love with him - and then cons them out of a lot of money.
Tinder Swindler trailer: $20,000; 40,000; $140,000. His life depended on me. That's when police tell me the man I love was never real.
Robin Pomeroy: An extraordinary confidence trick that leaves the anxious viewer very relieved that this is not their own story.
But it is the story of this week’s guest. Cecilie Fjellhøy is the Norwegian woman at the centre of the documentary whose life was torn apart by the actions of a conman. A survivor of romance fraud on a grand scale, she now advocates for the rights of, and support for, others who find themselves in similar grim circumstances.
And we’ll also hear from Sean Doyle who works at the World Economic Forum’s Centre for Cybersecurity on just how widespread romance fraud really is, why it’s a multinational, multi-billion form of cyber crime, and what is being done to combat it.
But first, Cecilie Fjellhøy, interviewed here by my colleague Anna Bruce-Lockhart.
Anna Bruce-Lockhart: You were defrauded out of over £200,000 by a man who went to just the most unbelievable lengths to disguise himself and fool you into trusting him. Can you tell us a little bit about that? I know you've told the story a million times before, but just for the background to the rest of the conversation we're going to have.
Cecilie Fjellhoy: Yeah. I met man first on Tinder back in 2018, and we matched up, and I was the first one who wrote a message to him because I could see that he was travelling a lot around. He had a look that I liked, and the next morning we we met for a coffee in London.
I met him in person. Looked like his pictures. Really charming. Really opening up to me, like. So we had a coffee. He was talking about his job. He was the CEO of a big diamond company, was travelling around, you know, wining and dining clients, signing contracts. So that was kind of his job.
We really connected. He was telling me about his daughter, and at the end of the coffee, he was like, I really want this to continue. I want to see you more. And I was like. Yeah, me too. It is shame, you know? He said, do you want to join us? Like, do you want to join us today? We're going to Bulgaria for a business trip, but I would love for you to join us.
And fortunately at the time, I had just moved to London. I was finishing up a Masters thesis, so I was just working part time. So I was going to work on my Masters thesis that day, so I actually had the opportunity to go with them. So I said yes. And then when we got out from the cafe, I was introduced to this entire team of people working for him who had been like waiting for him. So I met his business partner, private assistant, and met his bodyguard and several drivers, and I met his daughter and the baby's mother.
So you can imagine it was proper, overwhelming feeling of seeing how an entire different life was. And it was wonderful.
Like, so that's when the private jet trip happened. So on the first day I met him, we travelled on this private jet and I fell quickly and I fell hard and we talked every day, FaceTime. He was always available, always caring. Everyone I talked to said that Simon is amazing. He is so caring, is funny, and he was really funny with you.
And I was in that state that I wanted almost to protect him because he had so many people around him, kind of like, you know, if you're a rich guy you have a lot of vultures around. And I was like, walking would just be in my apartment in London and make tacos. And I was trying to kind of get him to relax more.
But is the reason why he had a bodyguard. So he said to me that he had gotten some threats from his competitors because he was doing so well in the business, but everything was going to be fine. But he was the reason why he had the bodyguard, Peter. And after a while I'm getting small drips, you know, he couldn't come to London anymore. And then he was showing me pictures of funeral flowers he had gotten on his door and he was showing me CCTV of a break-in of his apartment in his home country. And I was like, wow. Like, this is, are you safe? Like, I was sending him several messages. So it was like I was really feeling for him cause I was like, what is this life?
Things we're not getting better things. We're only we're getting worse. And around Valentine, I had given him a very nice presents, a very personal one, like ten wonderful things about you that I'd written myself, and I given him a book about how it is to be in a relationship with a Norwegian, and it was like several things.
And very quickly after that he said that he had a security team, that had told him now that he couldn't use his cards anymore because his competitors were tracking where he was in the world by the spend on his card, and that could be detrimental for him. It was like there were death threats that he had on him, so it was providing him a lot of difficulties.
At this point in time then he asked for a favour. The favour wasn't money, you know, it was security. So he's asking me, do you have a credit card that I could just use your name to travel safely under so he could travel safely and be Cecilie Fjellhøy and not Simon Levivev?
And at this point in time, I have to say the request felt so small compared to what he had given me. You know, both experiences, emotional support for me. I was like, this man is so caring. What kind of person would I be now if I would then say, no, you can't even borrow my credit card. With the notion that this was a very difficult situation for him.
So unfortunately, I took up a credit card. I travelled to Amsterdam to see him, and he started using it very quickly and was racking up it very quickly. So I had to then talk to the bank because they were blocking the card, lying to them where I was in the world. If he was in Cape Town and it was blocked, I had to call pretend. 'Hi, I'm in Cape Town. I'm trying to spend $550. Can you open it?'
It was terrible. The amount of pressure when I was working full time. Every time the card was blocked meant that he might be in difficulties and in danger. And that was another ball game for me. And of course, things didn't get better.
It only got worse. When I was visiting him they created immersive theatres around me, where I was with him one day during Easter and we were going to be together for Easter. We're going to travel away. And I was like, finally, you know, you really need to, you know, you're in such difficulties. You really need to get away. But then Peter calls: 'Simon. They found you. They found you. You have to leave now. I have a plane ready for you. I don't know where you're going, but you need to leave now.'
And Simon was, 'I can't like. I've just come here with Cecilia.' But in the end, he left me and we had to, you know, turn off the lights in the apartment, look through to see if we saw the enemies. I was scared, had lock the front door. It was terrible. And you're feeling it yourself.
Further on, he made me have to remove my last name on my Instagram because they were going after me, and changed my profile picture, and it was just insanity.
And then they got attacked in Copenhagen as well, where I got woken up at 2 a.m. where his bodyguard had been attacked, and they just had to flee and he had to go into hospital. And I remember his words so clearly, like, 'we are in a war right now.' We and using the we. But it's not just him, it's us together. It's so powerful.
And that's what I saw. Like mixing the love that I had for him and the care and being scared. You have a very strong cocktail there to get people to do what you want. And he got me to do insane stuff. You know, I took out £25,000 in cash and travelled with that. Who is that? You know, that was not me.
So after a while, you know, I was fearful for him. So I started taking up high consumer debt loans in Norway because he was racking up the bills and it was insanity. So in the end, I'd taken up nine loans and over £200,000 in just 54 days, 54 days.
So that is kind of the story of it, like quickly. But the insanity around the pressure, you never know when a phone call is going to come. You never know when an SMS is going to come in where he's in trouble, or a message where he just says he loves you and misses you and you're like, oh, like, this is like, so he was my one constant. That was him. I was more fearful of what would meet me on the outside when I realised what was happening to me than when I wasn't with him. Because as long as I had contact with them, as long as he was with him, and he was promising me that everything was going to be okay. That was more powerful than take that into what is actually going on here. This is not a healthy, good relationship. This is pressure beyond belief.
Anna Bruce-Lockhart: When did Simon's lies start to unravel? And what happened when you confronted him?
Cecilie Fjellhoy: I think I realised mentally in the end, because he had been travelling around for this big deal, he was going to buy a hotel here in London. And in the end he was going to come to London and either cry on my shoulder or pop the champagne.
And I remember that night when I went to bed and he was going to have this final meeting that was going to decide it all. And the next morning I woke up and I just got a message, 'I lost'. And I was shaking.
Because remember the weeks before, I'd gotten a check that I couldn't cash. I was checking my bank account every single day and no transfers were coming in. Is creeping up on you. That's something it's, you know, and call it the waiting room or sitting in the waiting room, just like in, like what is going to happen. And it's just more comfortable just being there because at least that's what we know than opening that door and going to the doctors and get the news. I think that's how I view it as an analogy, because I think that is so true.
You know, it's almost like domestic abuse victims, they stay and it's the same thing. We stay because this is what we know of. So I think in the end then, I woke up and saw the message and I started like shaking. I went to work, but my body was physically telling me I was almost throwing up. I was physically shaking at work. I was sitting there like, work has been escape, at least that's where I can just think about work. I couldn't even do that anymore.
Even then, I used two days before I did anything. I kept it up with him, and that's when I sent a message to the bank that I had the original credit card for and said I need help that I finally realised something is off there. And that's when they came to my work with two special security agents and told me that they had a long investigation on him. They asked for if I had a picture of him, I showed them the picture. And I remember when I showed the picture and they just looked at each other and they nodded. My life was just falling apart.
And then they were showing me names of people that I had bought flight tickets for. And it was just, you know, knowing what you had been part of, but seeing as well like that they were saying that we're going to go after him and this is his job. Think about it, that you're good at your job. This is his job 24-7. You should not feel bad about what happened to you. He's a professional.
And that was kind of, I was lucky in the sense that that day, that was the kind of words I was getting instead of getting what I got later, that, oh, it's your fault what happened to you. When we have a perpetrator and a clearly big criminal here, like. And I got to know later on that he had already been in jail in Finland for the same thing, different name, but the same things. And he shouldn't even have been in Europe.
It's sad because you thought that you would be protected, but this has really shown me that we need to be much more vigilant, that we are not being protected as much as as you were thinking.
I was kind of having a naive view that if you had been sentenced and you're not allowed to be in Europe, you're not allowed to be in Europe, you know? But he was travelling a lot and some victims of might be vulnerable, have, might be in other situations. I've had just good relationships. All the men that I've been in, relationships have been the best. I hadn't been cheated on. I had never had anyone lying to me. You know, I've always been very fortunate. So I think as well I was a good candidate for Simon to know, okay, this girl, she will fall quickly and she will fall and she will trust to the nth degree, which I did.
Anna Bruce-Lockhart: So you had the security agents who are quite nice to you on the day, but then also you had follow up with the banks and the legal system where you didn't have such a good experience.
Cecilie Fjellhoy: I think that's the hardest part of being a fraud victim is what comes afterwards.
So I had to file it in two countries because most of my debt was in Norway. So I went first to Norway to report it and that was the most horrendous experience. I had to bring my mom there because I was so down mentally to maybe 1.5 hour, and then they dropped it after three weeks.
Even though he had been in Norway, there was stuff that they could have helped out with. And then I reported it in London. He sent me some death threats after I started kind of snooping around. Because you did. Because you met so many people. I met friends, women in Netherlands as well. I was like, who were they? You know, were they in on it? So when he got news of that, he was not really happy.
I think when I then went to London, this is six years ago, the police did not understand what romance fraud was, what I had endured personally. You know, you look at it as, 'Oh, you lost some money. Tough luck'. And since I had sent in some fake documents to the banks that I didn't know what was fake at the time, they decided to make me a suspect. Almost a year later, I had to go into questioning as a suspect, which was horrendous, if you can imagine how that was.
And then later on, over a year later, they dropped my case against Simon, but dropped their case against me as well. So it took two years. If you can imagine, I would have to say two years where I was not viewed as a victim from professional sense. I have gotten an apology from the police in London for now because I made an official complaint. So they said that this would not have happened now. Six years ago, things were very different. But I said, I just want just to learn from this, that this is not how you treat a fraud victim.
Yes, it's a complicated case, but you can still have empathy along the way. And it was very clearly lack of empathy towards me and what I was enduring. Because while I was as well a suspect with the police, I was taken to court by four banks in Norway because I couldn't pay the loans I had taken up. So in the summer of 2019, I was got slapped with a lawsuit. And in Norway you don't get any free legal help. So I had sold my apartment, so I had to use that money to, so I got legal help, but that was as well used against me at court.
So I had to go through two rounds where I was called naive, gullible, just wanted a rich boyfriend. But as well, when it came to the uptake of the loans, I was cunning as well. Which is like how they were portraying me was just really, really like total dismantling of my character. And I felt like you're forgetting that we have a clear perpetrator here still going around defrauding people, but here we are pointing the finger at me, and I think that's what they want. I'm always saying by blaming victims of fraud, do we fall for the con ourselves? And I say yes. Because I'm a living proof that by them pointing the finger at me, you've done exactly what Simon Leviev wanted you to do. The reason why you use my name is the reason why he wanted me to speak to the banks. Is nothing in his name. Everything is in my name.
40% of all crime is fraud. But only 1% of police resources is allocated to fight it. When you think about the intricacy of romance fraud, then how little is being used to tackle it? And I'm thinking about international collaboration here as well. With our case, it was nothing. Nothing. But we see that they can do it. They do it in drugs. They do it in human trafficking. And I think with my case, it was proven that the minute he jumped from country to country, from jurisdiction to jurisdiction, no one could catch him. It was almost like it's impossible to collaborate.
But I think, again, it's the lack of resourcing here, lack of education. Police aren't equipped to deal with this, or how it's been viewed as purely financial. It's not a financial act, it's a human act.
Anna Bruce-Lockhart: It feels to me that there's a bit of a gender angle here, like it's so difficult to prosecute rape and domestic violence and things like that, and this feels like part of that. It feels like such a huge struggle for women to be heard.
Cecilie Fjellhoy: How people are viewing this crime is just so wrong because it's not a women crime. This is not a gendered crime. We have stats from Lloyd's last year that reported to them was 53% men. But because women are the ones speaking up, in different ways, the reports are skewed. Everything is skewed. Everyone thinks that this is old women, vulnerable, sitting at home knitting type of crime. But it's not. Everyone is the victim of this because all of us want love and we are vulnerable when we're seeking love. But I think there's a lot of men suffering in silence.
And I've been at even cybercrime events where people are laughing at it. It was an ethical hacker that had done a speaking, and at the end of it, he came up with a joke. Because a lot of times romance fraud is the joke of the town, you know, like, ha ha, how stupid are they? And he said if he was going to get money the quickest was to pretend to be a young, beautiful woman on Tinder and get an old guy. And people in the audience were laughing because a lot of times it's always an evil woman at the back end. For him, it was an evil woman. And then when we got defrauded by men, we're still evil women and we're gold diggers. It's still that narrative, kind of, that, especially from a young woman's perspective, that is super gendered. I totally agree with you.
And one of the reason why this crime isn't being taken us seriously, you know, that shame and that stigma that men would have, coming forward, at least for us women, we would have kind of more of the support from our friends, from, you know, a loving perspective, because I have that so much. Happier doing this for women is amazing. Yes, I'm doing it from a women perspective that I've been treated horribly in the sense that you're a woman and you're being very judged based on how you look or you know, just for being a woman.
But this crime is not gendered. Everyone can be a victim of this. And I think that is what I am really passionate about.
Anna Bruce-Lockhart: I want to get on to LoveSaid , this lovely NGO of yours. And what was a moment when you're like, yes, I'm going to do this. And what was the enabling factor?
Cecilie Fjellhoy: So I started off talking to tons of other NGOs looking at what they were struggling with, got a lot of information.
So after 'The Tinder Swindler' blew up back in 2022, I did a webinar and then I met this amazing woman called Anna Rowe, and she has several social media called Catch The Catfish. And I was like, this woman is incredible. Her thoughts, you know, ambitions, what she was doing, is so aligned with what I want to do. Like she's helping victims on a daily basis, and her ambition of what she wanted in the future was to make it bigger, help even more people, be a support centre, but change things as well.
We have a lot of support, okay, we're here for the victims, but we want fewer victims or we want more victims to be taken care of properly. So I was like, I want it to be a think tank as well that will actually do more of the research that we need.
There are no numbers, for example, on suicides, on foreclosures, on sick leave. What is this costing society? We don't have any numbers, so it's super difficult to talk about something or get anyone to take action. Get politicians to take action, social media companies to take action.
So that is what that was. So we instantly connected and we were thinking, okay, let's create something that will make an impact. And that's when LoveSaid was born, a year ago. And we've been working throughout the last year, business plans, doing several talks around the UK where we have been talking to banks, police forces, which has been amazing, to see that they're changing, that they see victims as resources, that we have something to come with. LoveSaid can provide the training on how to speak to fraud victims, how to treat them. But I think what will be, you know, the heart and soul of the organisation is the support centre, that people know that they will come to us with no judgement.
Justice will look different for everyone. Some people will have their cases dismissed, but at least they have the mental health support that we will provide that they can get back on their feet, they can get their lives back. It's money, you know, and we can heal as people. And we have so many people coming to us that we're helping already saying, it's just so nice knowing that that you're here, that you're responding. And then police forces as well. It would be so nice for us to know that you're there, that we could send people to you, that we know that they will kind of be there for us. And that is specifically for romance fraud.
Anna Bruce-Lockhart: Can you tell me a little bit more about what you offer to a victim?
Cecilie Fjellhoy: When they come to us, it's always one on one, first of all, because we are working on making a digital step by step guide so they will get help in their situation. But right now they send in a message to us. We come back to them. We ask, you know, where in the world what kind of fraud did they take up loans? And then it's both kind of safeguarding them. A lot of times these people find them again and they might try to recover their money and might get scammed again.
So it's both the practical help on actually how to report it, because a lot of the times that is not as easy. When people are in trauma, they don't know what to say, they don't know what is important, what is not important. Reporting to banks is to educate them with, as I said, with the research that has already been done and what happened to them so they can get healing from that.
We have a peer support group every month now, so the victims can meet each other, that we are guiding them through different things. And in the future, we would love to have different experts coming in and talking about, you know, money, financial. So it's actually just helping them through their journey.
We maybe helped like 6,000 in total, like one on one throughout the years. We help family and friends as well. We have sometimes them coming to us.
You see a lot of it actually. Family who are seeing either their mom, dad, sister, who are in difficulties that they're being scammed. They refuse to believe. Because if you go to a fraud victim, you know the stigma around that, 'you're stupid if you get defrauded'. If you've been defrauded, your guard is up. If we take them on a journey, the five wise, I call it, if you can explain it in five ways, it's not a good idea, because if you stop being able to explain it on the third one, it's a bad idea. If you don't know enough about your partner or why he needs the money, that you can't explain it. Bad idea.
So you're taking the victim on the journey themselves because ask themselves, they themselves need to realise it. So it's kind of just giving them the tools, and sometimes it's just like putting that little doubt in their mind. And in the end they might come back a week later, two weeks later. This is a long game.
This is why banks sometimes are not the best people to approach someone that they think is being defrauded, because they don't have the time. Remember when the first bank blocked my card? They said, we know you're not the one using your card. And I knew I've done something wrong by giving him my card, you know, you're not supposed to do that. So I was so scared because it was so accusatory and so like, I felt that I was going to be in trouble. That is not how you do it.
If you knew that I wasn't using my card, most likely I was being defrauded, why didn't you contact police? It was a lot of money. Was £68,000 in three weeks. Why don't you reach out to me again? Kind of in a more like, is everything okay with you? Are you going through stress? There's several things you could do.
So I think LoveSaid is kind of like an extended arm of this. And we really want to be, in addition, you know, to what the banks are already doing. They're doing a lot of great work, but they don't have the time.
Robin Pomeroy : Cecilie Fjellhoy was talking to Anna Bruce Lockhart.
Wouldn't it be nice to think that romance fraud is rare - that it couldn't happen to you or your loved ones? Unfortunately that is not the case, as you'll hear now from Sean Doyle, an expert on cybercrime at the World Economic Forum.
Sean Doyle: Sean Doyle. I'm lead for the Cybercrime Atlas at the World Economic Forum.
Robin Pomeroy: So, Sean, Cecile's story is a fascinating one, quite disturbing in many ways. But is it really cybercrime? How does it relate to the work you do at the World Economic Forum?
Sean Doyle: So it's a very good example of cybercrime.
It's playing on a very basic human need, for the need to be loved has been around as long as people have been here, and the habits that people have of trying to trick each other has been going for just as long.
I think what's different and why is romance fraud changed is that cyber enabled fraud allows us to do these things at scale.
Cecile is one example of a very, very large group of victims. This really is a very old form of fraud. What's changed is that the internet allows us to do this at scale and across countries.
So very often these scammers are not sitting in the same country as the victim. That allows them to go after multiple victims at the same time.
Now, to give you an idea of just how profitable this is for organised criminal gangs, they've started seeking out cyber experts by tricking them into coming to a good job, let's say moving from Brazil to Vietnam with an option to work in IT, and then enslaving them to work in cyber fraud farms. So this is very much something that's enabled by the internet.
And when we think about cyber security, I think that you've got to think, why do we have cyber security? It's in order to protect us from cyber criminals. And in this sense, what we're seeing with these romance frauds, it's it's a good example of the type of behaviour we see by cyber criminals in relation to frauds they undertake against companies, in the manner in which they identify and then take money away from victims.
So yes, this is very much a cyber enabled fraud.
Robin Pomeroy: Cecilie makes the point that probably there's lots of this stuff that's under-reported, probably because people are ashamed or embarrassed. It's so personal isn't it? I mean, it's amazing her story, which might be extraordinary because it involves private jets and apparently a cast of characters that she met in real life. There's probably a lot of more low-level, perhaps, stuff that doesn't involve a private jet and a cast of characters, but as you say, maybe an actual human being who is not who they say they are, who is employed by a criminal gang.
Do we really know how widespread this kind of criminal industry is?
Sean Doyle: Look, I can say this much. It is enormous and it is global.
The Global Scam Alliance has put out an estimate of, I think, $1 trillion in profits. We come back to recent incidents we've had of 220,000 plus people being recorded as being trafficked to work in cyber fraud farms. We can really say that that is probably the tip of the iceberg. We've seen a large number of arrests in countries like the Philippines, Thailand, India and across Europe, where criminals who are not previously into cybercrime are getting involved in this simply because of the amount of money they can get out of it and the reach they have through the internet to get a very large number of victims.
Robin Pomeroy: It's kind of a low risk, high return business model, maybe?
Sean Doyle: At the moment.
Now, I would say there is some good news, particularly since December of last year, over the last 5 or 6 months, we've seen that law enforcement are getting better at working within country, cooperating with law enforcement in other countries, which is absolutely necessary if the victim is sitting in Norway or the UK, as Cecilie was, but the criminal might be in a completely different part of the world. But they're also getting much better at taking advantage of the expertise in the private sector.
So, to give a recent example, in the UK, what's called a cybercrime as a service group was taken down, a group that was simply providing like the equivalent of software services that you get for a corporation but aimed at criminals. It's called LabHost , was taken down. They had about 70,000 victims, and it took collaboration between 37 different sets of law enforcement in different countries to take them down.
But actually the leads that that led them to, the information that led the police to this group, came from a private sector alliance called the Cyber Defence Alliance , which is, I think, funded by financial services in the UK, and aimed at exactly identifying who the criminals are that are going after victims, the infrastructure they're using, the IT they're using, and identifying ways of breaking that up.
Robin Pomeroy: Yes. So I was going to ask you what should we do across the horizon of the stakeholders here, companies which would be banks, and we heard from Cecilie about how the banks are investigating, authorities, police authorities, policy makers and even individuals. I mean, are there some, are there recommendations that the World Economic Forum is making?
Sean Doyle: So starting with individuals, it is just to be very aware that this is always a possibility, that if you meet someone on the internet, even if you're talking to them for a very, very long time, and they will trust, we do have to be careful about who they are. So what I would say is, if somebody is offering you an investment opportunity or for some reason demanding cash and saying they really need us, really think twice unless you've met them in person and are very certain of who they are.
What governments can do is think about building capacity to identify, stop and prosecute these kind of cyber-enabled frauds, which is easier said than done. That means looking at how they fund their police in their home country, but also how they interact with law enforcement across other countries. So whether bilaterally or via an international group like Interpol. So thinking about capacity building.
But then an awful lot of the skills for identifying cyber crime sit in the private sector. The ability to identify and deal with the infrastructure being used by criminals. Their IT infrastructure sits with the private sector.
So it's very important to identify ways of allowing government agencies to collaborate with the private sector to share information on these criminals, but also allowing private sector members to work together. Because what we've seen from the work done by the Cyber Defence Alliance, which is in the financial sector, but also by a Forum-hosted project called the Cybercrime Alliance, where we brought together cyber experts from a number of different sectors, is that when you bring experts from different areas together, they can create new forms of information on how these criminals operate, what they're using to operate, and to help us kind of map out what they're doing and understand where we can cause the most pain and disruption for them.
Robin Pomeroy: You talk about mapping out, you run this thing called the Cybercrime Atlas Initiative. Could you tell us what that is?
Sean Doyle: So the Cybercrime Atlas brings together experts from the forums, network of cybersecurity companies, IT companies, financial services, cryptocurrency, anybody who has a role in disrupting criminal activity online. We have support from about 25 companies and founded by Microsoft, PayPal, Santander and Fortinet.
But what these group are doing, we're getting investigators working just on open source research. So overcoming that barrier that companies have of sharing their own information or sharing personal information, what they are doing and saying, can they just using what's out there in the internet, build up something new and map out the activities of cybercriminals and how they go about doing their business with the aim of us being able to disrupt them more effectively.
And, you know, that's an experiment. I'm glad to say that the first part has worked out very well. We are able to create new and valuable research on these criminal groups, and it does have operational value. What we need to see in the Forum then, is how do we go about scaling this so it can have greater global impact?
Robin Pomeroy: Have you noticed any differences, any progress kind of in the real world? Cecilie's story was a few years ago. She tells us about how she felt she was being blamed. Obviously she had been lured into doing some wrong things herself, but she says she was treated very badly and she could understand why people wouldn't report this kind of stuff for a number of reasons. Do you think things have improved since then, which which was several years ago?
Sean Doyle: So we're seeing improvements in a couple of areas.
First of all, countries like the UK do have requirements that victims get some sort of restitution, some sort of their money back. That could be spread further.
One reason why people might have hesitated to go to the police before is, frankly, because the police often weren't in a position to do much. So we're finding that the capabilities and capacity of police to identify and deal with cybercrime is going up, but also their willingness to work with police agencies and other countries, and the effectiveness of that.
So we're seeing that people are more able to identify and stop cybercriminals, but also the speed of response is going up, and the police have become much better at identifying really where the most harm is being done.
So you'll see in countries like Thailand, the Philippines, India, over the last 3 or 4 months, there have been a lot of arrests of the criminals, and they've identified where victims are being trafficked to work in cyber scam farms. And they're finding ways of releasing these people who have been trafficked and really for double victimisation because they're victims of trafficking and they're being forced to commit crimes against other people.
One thing that does need more emphasis is educating the public. So that people should have more protection. They should feel that if they've done something a little bit wrong or been tricked into doing something that either makes them feel ashamed or that they're at risk, that they're given the kind of protections that allow them to go forward in confidence and report.
So that's awareness raising and not just saying we're changing things, but showing how the victims are protected when they report crimes.
Robin Pomeroy: And here's a question that probably gets asked in every single interview I've done over the last 18 months, artificial intelligence, because you talk about thousands of people being trafficked to take part in this criminal activity, which is totally surprising to me. But I guess in the future, or maybe already, you can automate. You can create personalities that seem real. Is that something you're already seeing, or is it something that could become a risk in the future?
Sean Doyle: So first of all, it's hundreds of thousands being trafficked. That's how big the problem is.
With regards to AI, look, we're seeing elements of it being used, such as voice deepfakes and video deepfakes. And they're having a measure of success.
I would say with things like generative AI, what that has done is it's made the email campaigns much cheaper to run and much more effective.
Whereas before, let's say, if you were sitting in an English speaking country, you might get a message from someone that it looks very much like broken Russian and might make you suspicious as to whether or not this was something you should click on that if you didn't. Gen AI allows for criminal groups to send out messages that are convincing in lots more languages, lots more cheaply.
But, you know, that's kind of the headline element. I would say that actually the, the uptake of AI by criminals has been incremental. We're not seeing enormous changes as of yet, but the issue is that those incremental changes over time, given a few years, could eventually have a big impact.
The positive side of the story is that cyber defenders tend to be making better use and more effective use of AI than the criminals at the moment, but that, there's an imbalance in that the what we call the cyber equity gap in the World Economic Forum's Centre for Cybersecurity, that, over time, countries that have more funding and companies that have more funding are doing better at their cyber security. But actually it's not a case of that the smaller ones are just standing still while the others take away, they're going a bit backwards. Because there's a lack of skilled professionals in cyber security. You know, in the legal world, these move towards the larger companies where they can get more money, and you'll see that the criminals are responding to that skills deficit by trafficking people and tricking them into work.
So all of those coming together, AI is not yet a game changer for criminals. It is having an impact. But, over a period of years, it could really seriously change things in criminals' favour if we are not careful.
Robin Pomeroy: Sean Doyle, of the World Economic Forum's Centre for Cybersecurity. You can find out more about the Cybercrime Atlas Initiative on our website - links in the show notes.
In this episode you also heard Cecilie Fjellhøy, from the Netflix documentary The Tinder Swinder. Her organisation is called LoveSaid.
Please subscribe to Radio Davos wherever you get your podcasts and please leave us a rating or review. And join the conversation about podcasts on the World Economic Forum Podcast club on Facebook.
This episode of Radio Davos was presented by me, Robin Pomeroy, with reporting by Anna Bruce-Lockhart and editing by Jere Johansson. Studio production was by Taz Kelleher.
We will be back next week, but for now thanks to you for listening and goodbye.
Hosted by :

Robin Pomeroy
Podcast Editor , World Economic Forum

Anna Bruce-Lockhart
Editorial Lead , World Economic Forum
More episodes :

Spatial computing: why the future of the internet is 3D

Where are the innovations that can make mining more sustainable?

Advanced Energy Solutions: scaling up the tech that can help us get to net zero

Why it's time for the 'middle powers' to step up on geopolitics
.chakra .wef-1dtnjt5{display:-webkit-box;display:-webkit-flex;display:-ms-flexbox;display:flex;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;-webkit-flex-wrap:wrap;-ms-flex-wrap:wrap;flex-wrap:wrap;} .chakra .wef-n7bacu{margin-top:16px;margin-bottom:16px;line-height:1.388;font-weight:400;} More on Cybersecurity .chakra .wef-17xejub{-webkit-flex:1;-ms-flex:1;flex:1;justify-self:stretch;-webkit-align-self:stretch;-ms-flex-item-align:stretch;align-self:stretch;} .chakra .wef-nr1rr4{display:-webkit-inline-box;display:-webkit-inline-flex;display:-ms-inline-flexbox;display:inline-flex;white-space:normal;vertical-align:middle;text-transform:uppercase;font-size:0.75rem;border-radius:0.25rem;font-weight:700;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;line-height:1.2;-webkit-letter-spacing:1.25px;-moz-letter-spacing:1.25px;-ms-letter-spacing:1.25px;letter-spacing:1.25px;background:none;padding:0px;color:#B3B3B3;-webkit-box-decoration-break:clone;box-decoration-break:clone;-webkit-box-decoration-break:clone;}@media screen and (min-width:37.5rem){.chakra .wef-nr1rr4{font-size:0.875rem;}}@media screen and (min-width:56.5rem){.chakra .wef-nr1rr4{font-size:1rem;}} See all

Global financial stability at risk due to cyber threats, IMF warns. Here's what to know
Spencer Feingold and Johnny Wood
May 15, 2024

Cybersecurity lessons from Latin America's battle against ransomware threats
Belisario Contreras
May 2, 2024

Jeetu Patel on bridging the cyber skills gap

Why cybersecurity needs diverse thinkers and a dynamic approach

Strategic Cybersecurity Talent Framework

Quantum computing could threaten cybersecurity measures. Here’s why – and how tech firms are responding
Simon Torkington
April 23, 2024
- Bibliography
- More Referencing guides Blog Automated transliteration Relevant bibliographies by topics
- Automated transliteration
- Relevant bibliographies by topics
- Referencing guides
Cookies on GOV.UK
We use some essential cookies to make this website work.
We’d like to set additional cookies to understand how you use GOV.UK, remember your settings and improve government services.
We also use cookies set by other sites to help us deliver content from their services.
You have accepted additional cookies. You can change your cookie settings at any time.
You have rejected additional cookies. You can change your cookie settings at any time.
- Cyber security
UK and allies sanction prolific cyber hacker
The UK, US and Australia have sanctioned a senior leader of cyber-crime gang LockBit.

- UK, US and Australia sanction Russian leader of cyber-crime gang LockBit
- LockBit were one of the most prolific ransomware groups in recent years, responsible for attacks on over 200 UK businesses and major public service providers
- UK and Allies crack down on malicious cyber-criminal activity emanating from Russia that seeks to undermine global integrity, prosperity and security
The UK, US and Australia have today (Tuesday 7 May) sanctioned a senior Russia-based leader of LockBit, once one of the world’s most pernicious cybercrime gangs.
Today’s sanctions target Russian national Dmitry Khoroshev who has been identified, as part of an ongoing international law enforcement investigation, as one of the leaders of LockBit, the ransomware group responsible for extorting over $1 billion from thousands of victims globally.
In February the NCA announced that it had infiltrated the group’s network and taken control of its services , compromising the entire criminal enterprise. The group has attempted to rebuild over the last 2 months, however the NCA assesses that as a result of this investigation, they are currently running at limited capacity and the global threat from LockBit has significantly reduced.
The gang was responsible for 25% of ransomware attacks globally last year, targeting thousands of victims over the years including over 200 UK businesses. LockBit orchestrated a malicious online campaign, illegally stealing and using sensitive data to extract billions of dollars from business and individuals.
Today’s measures will directly target a senior leader of the gang responsible for these atrocious attacks. Khoroshev will now be subject to a series of asset freezes and travel bans.
Sanctions Minister, Anne-Marie Trevelyan said:
Together with our allies we will continue to crack down on hostile cyber activity which is destroying livelihoods and businesses across the world. In sanctioning one of the leaders of LockBit we are taking direct action against those who continue to threaten global security, while simultaneously exposing the malicious cyber-criminal activity emanating from Russia.
National Crime Agency Director General Graeme Biggar said:
These sanctions are an important moment in our fight against cyber criminals behind the LockBit ransomware group, which is now on its knees following our disruption earlier this year. They have caused untold damage to schools, hospitals and major companies across the world, who’ve had to pick up the pieces following devastating cyber attacks. Dmitry Khoroshev thought he was beyond reproach, even offering $10 million to anyone who could reveal his identity, but these actions dispel that myth. Our investigation into LockBit and its affiliates continues and, working with our international partners, we’ll do everything we can to undermine their operations and protect the public.
Eleanor Fairford, National Cyber Security Centre (NCSC) Deputy Director for Incident Management, said:
Ransomware attacks pose a massive threat to UK businesses and their impacts can be severe and long-lasting, disrupting operations and putting potentially sensitive data at risk. It is crucial organisations ensure they have strong online defences to reduce their risk of falling victim and to protect the information they are responsible for. Prevention is the most effective mitigation, and we urge all organisations to follow the NCSC’s ransomware guidance to help protect their networks and improve their resilience to attacks. The UK has sanctioned Khoroshev as part of our wider commitment to cracking down on malicious cyber activity and working with our international partners to promote international security and stability in cyberspace.
These sanctions have been delivered jointly with Australia and the US and are the latest in our efforts to counter malicious cyber-criminal activity emanating from Russia that seek to undermine the integrity, prosperity and security of the UK and our allies.
View the full UK Sanctions List .
- the National Cyber Security Centre (NCSC) and the National Crime Agency (NCA) assess that LockBit was the leading ransomware threat to the UK and globally since the demise of the Conti ransomware strain in mid 2022. The strain first emerged at the end of 2019 and by 2022 was the most frequently used variant across the world
- LockBit caused significant disruption to many UK organisations and services, having severe short to medium term impact on prominent services within the private sector. The organised crime group responsible for LockBit, as well as the affiliates using the malware represented a significant threat to victims’ data due to their tactic of stealing data and publishing it on its darkweb data leaks site (DLS)
- according to industry sources, LockBit have leaked data from more victims on their DLS than any other ransomware group since records began, with more than 2000 victims worldwide listed
- you can report a suspected cyber crime online: where to report a cyber incident
Media enquiries
Email [email protected]
Telephone 020 7008 3100
Contact the FCDO Communication Team via email (monitored 24 hours a day) in the first instance, and we will respond as soon as possible.
Share this page
The following links open in a new tab
- Share on Facebook (opens in new tab)
- Share on Twitter (opens in new tab)
Is this page useful?
- Yes this page is useful
- No this page is not useful
Help us improve GOV.UK
Don’t include personal or financial information like your National Insurance number or credit card details.
To help us improve GOV.UK, we’d like to know more about your visit today. Please fill in this survey .
Volunteer fire department sees $220,000 raised for ambulances disappear in cyber crime

Around $220,000 was stolen from a Maryland volunteer fire department in a cyber-attack last month, according to a report put out by the Rockville station.
The money was being held for the purchase of two new ambulances the department desperately needs, the release states. It was taken by criminals impersonating a vendor working with the station to secure the new vehicles.
A bad actor intercepted the wire transfer email thread to slightly change the bank routing number to send the transfer to London.
“If you looked at it and followed the string, you’d have to look very, very closely to see that one letter was changed in the email string," Eric Bernard, the president of the Rockville Volunteer Fire Department said in an interview with WJLA.
"The email string continued for a while. We made the wire and five days went by and our vendor said 'Hey you gonna finish that wire we were on the phone (about),'” Bernard said.
Half of the money has since been recovered
Half the department's money has been recovered, according to the news release from the station.
The Montgomery County Police Department was contacted as soon as the Rockville Volunteer Fire Department caught on to what was going on. The United States Secret Service and the Federal Bureau of Investigation were brought in on the incident as well.
More than 80% of what the RVFD deals with is Emergency Medical Services, WJLA reported.
Last year the RVFD had "a total of 14,662 unit responses making Rockville Volunteers some of the most active firefighters, EMTs, and paramedics in the nation," according to the release.
"Thanks to decades of generosity from the community RVFD serves, we remain in a strong financial position to both complete this purchase and to continue operations as normal," The RVFD reported.
Those interested in helping replenish the department's funds can visit www.rvfd.org/donate . A GoFundMe is being set up and will be live soon.

IMAGES
VIDEO
COMMENTS
116 CyberCrime Topics & Essay Samples. Updated: Mar 2nd, 2024. 9 min. If you are writing a cybercrime essay, our team prepared this article just for you. Here, you will find 115 unique topics for any type of paper. We will write. a custom essay specifically for you by our professional experts. 809 writers online.
Excellent Research Topics on Cybercrime. Write about the importance of cybercrime management. Explain the history of cybercrime. Discuss the effects of cybercrime on the Internet economy. Talk about the cyberattack on Sony Pictures in 2014. Explain how technology has influenced the evolution of cybercrime.
Topic 9: Cybercrime Dissertation Topics - Understanding the Different Types of Cyber Crime. Research Aim: Cybercrime, undoubtedly, is one of the most deadly forms of crime. Without causing physical harm, the crime causes the victim to attempt suicide or suffer from mental diseases such as anxiety, depression, etc.
Unique Cybercrime Research Topics. When it comes to writing a cybercrime thesis, avoid picking the most frequently discussed topics. Instead, take into account any original ideas on cybercrime that provide new information. Find here, some unique cybercrime research paper topics to get started. 1. Brute Force Attack: Conduct a Deep Analysis
current topic chosen for the study. Table 1: ... Thesis. Full-text available. ... Cyber Crime is an important and valuable illegal activity nowadays. Initially internet and email are treated as ...
Cyber crime involves the stealing or manipulation of information effectively distorting its values across global networks. Sexting and Related Cybercrime Legislation Sexting represents a relatively law phenomenon on the law, with specific legislation dealing with sexting and minors not being present in a majority of US states.
This thesis will lay out the importance of connectivity in our society - from the individual user to national security and the military. I will examine the vulnerabilities, cite case studies, and look at the consequences the cyberattacks have or could have on society. To best frame my research, I will include recent cyber events and examine the
Dr. Tamar Berenblum is the research director of the The Federmann Cyber Security Center - Cyber Law Program, Faculty of Law, the Hebrew University of Jerusalem, Israel, and the co-chair of the European Society of Criminology (ESC) Working Group on Cybercrime. Tamar is also a Post-Doc Research Fellow at the Netherlands Institute for the Study of Crime and Law Enforcement (NSCR), Netherlands ...
tists - explore myriad topics in cybercrime and cybersecurity research, but they have traditionally focused on technical aspects of these areas (Brands & Van Doorn, 2022). ... It has expanded our knowledge of the prevalence of cyber-crime and the impacts of technology on different offending behaviors (Holt & Bossler, 2014). It has also con-
DISSERTATION EXPLORING THE CYBERCRIME CAPACITY AND CAPABILITY OF LOCAL LAW ENFORCEMENT AGENCIES IN THE UNITED STATES Submitted by Christopher Jerome Moloney ... creating new pathways and opportunities for people to commit crimes or engage in harmful behavior via the internet or digitally networked devices. Cybercrime is rapidly
Criminal Law. Cyber Security Future Research Topics. Developing more effective methods for detecting and responding to cyber attacks. Investigating the role of social media in cyber security. Examining the impact of cloud computing on cyber security. Investigating the security implications of the Internet of Things.
Effects of Cyber Crime on Social Media. 2 pages / 933 words. The issue of cyber Crime has risen rapidly as a result of increased access to computers in the recent years compared to the past. Cyber Crime refers to criminal activities, which are carried out by the use of computers or the internet.
In this thesis, I take an empirical and systematic approach towards assessing the global cyber and biological threat. The first part of the thesis focuses on cyber crime. I examine international variation in cyber crime infrastructure hosting and cyber crime exposure. I also empirically test hypotheses about factors behind such variation.
This chapter covers the definitions, types, and intrusions of e-crimes. It has also focused on the laws against e-crimes in different countries. Cybersecurity and searching methods to get secured ...
Some of the most important topic areas that exist within the field of cybersecurity include cybersecurity and cryptocurrencies, cybersecurity's impact on business and economics, the role of cybersecurity in world affairs, cybersecurity and cybercrime, and how cybersecurity connects with big data and the Internet of Things (IoT).
Cardinal Stefan Wyszynski University in Warsaw 🏛️. In connection with the development of cybercrime on the Internet, the security systems for transfer and processing of data, financial ...
Cyber Crime Is a Serious. PAGES 8 WORDS 2431. These "stepping stone" computes can be located anywhee in the physical wold because eal-space is ielevant to activity in cybespace (Benne, 379)." The use of stepping stones can make it difficult fo law enfocement to find whee an attack actually oiginated.
6 Chapter 1: Background 1.1 Introduction With the advent of new technology, new types of crime have surfaced and traditional crimes such as fraud are now being perpetrated by means of sophisticated technology.1 Traditional boundaries have fallen away and a virtual borderless world has become a platform for crime.2 From this virtual reality world derives constraints for the traditional methods ...
Theses/Dissertations from 2013. Assessing the Relationship Between Hotspots of Lead and Hotspots of Crime, Kimberly L. Barrett. A Life-Course Approach to Sexual Offending: Examining the Continuity of Juvenile Sexual Offending into Adulthood and Subsequent Patterns of Recidivism, Maude Beaudry-Cyr.
Essays Cyber Crime Essay for Students and Children. ... Get the huge list of more than 500 Essay Topics and Ideas. Cyber Crime in India. Web world or cyberspace is a massive community of millions and billions of users and websites. Also, people access it for different uses like shopping, movies, music, video games, transactions, and e-commerce ...
Cybercrime can be defined as any unlawful act promoted or facilitated by the computer, whether computer is object of a crime, a repository of evidence relating to a crime, or an instrument that used commit a crime. In plain language cybercrime means crime engaged in computer network or computer.
The Shodhganga@INFLIBNET Centre provides a platform for research students to deposit their Ph.D. theses and make it available to the entire scholarly community in open access. Shodhganga@INFLIBNET. Aligarh Muslim University. Department of Law.
These courses often cover in-depth topics, including: Cybercrime; Cyberterrorism; Domestic, international, and comparative criminal law; Human security; Transnational crime; Furthermore, the Master's in Criminal Justice Thesis track, as the name suggests, requires students to dedicate multiple semesters to focus on research and data collection.
The U.S. Federal Bureau of Investigation (FBI) reported that the United States lost a record $12.5 billion to various types of cyber crime in 2023. Law enforcement hacking is one tool increasingly used to combat transnational cyber crime. Stephanie Pell, Senior Editor at Lawfare, sat down with Gavin Wilde, Senior Fellow in the Technology and ...
The Netflix documentary 'The Tinder Swindler' is a mind-boggling case of so-called 'romance fraud' in which a charming, handsome - and apparently very rich - man meets women on a dating app - gets them to fall in love with him - and then cons them out of lots of money. Cecilie Fjellhøy is the Norwegian woman at the centre of the documentary whose life was torn apart by the actions of a conman.
ICJ 792 International Crime and Justice Thesis II ICJ 705 Human Rights and Counterterrorism ... ICJ 726 Drug Trafficking ICJ 760 Information Technology and Cybercrime SEC 760 ICJ 728 History of Genocide ... ICJ 750 Special Topics in International Crime and Justice ICJ 755 Terrorism and Transnational Crime ...
Consult the top 50 dissertations / theses for your research on the topic 'Cyber crime.' Next to every source in the list of references, there is an 'Add to bibliography' button. Press on it, and we will generate automatically the bibliographic reference to the chosen work in the citation style you need: APA, MLA, Harvard, Chicago, Vancouver, etc.
7 May 2024. UK, US and Australia sanction Russian leader of cyber-crime gang LockBit. LockBit were one of the most prolific ransomware groups in recent years, responsible for attacks on over 200 ...
Comments. Comments have to be in English, and in full sentences. They cannot be abusive or personal. Please abide by our community guidelines for posting your comments.. We have migrated to a new ...
Add Topic. Volunteer fire department sees $220,000 raised for ambulances disappear in cyber crime. ... Around $220,000 was stolen from a Maryland volunteer fire department in a cyber-attack last ...