PhD Research Topics in Mobile Cloud Computing
MCC is a popular scientific field to share data through all kinds of portable devices . It enables the users to store and access their valuable info from a remote location. PhD research topics in Mobile Cloud Computing are our modern-cultured research plinth. We give a chance for PhD/MS pupils to shape their research career.
We will be your sunshine to make you glow in your PhD/MS career…
We experienced to handle several complex problems under MCC. Consequently, we are also ready to work on real-time applications like m-commerce, m-learning, healthcare, etc . In addition to this, our team also gives you support in manuscript writing too.
We never let you give up when we are with you…


Some Primary Factors of MCC
- Virtualizations and also Reliability
- Security and also Infinite Storage
- Extensibility and also Flexibility
- Data Backup and also Recovery
- Adaptability
Our experts are more avid to dive deeply into the below areas to find insight facts. We also develop our own ideas to get success in our research progress.
Hybrid Areas from PhD research topics in Mobile Cloud Computing
- Green Mobile Cloud
- Mobile Vehicular-Clouds
- Mobile-Fog & also Technology
- Edge-Mobile Configuration
- Mobile Cloud Networking
- 5G-Mobile Cloud Integration
- Ad Hoc Mobile Cloud Computing
- IoT Enabled Mobile Cloud
- Mobile Edge also assisted UAV
We will assign our review team in each field for the final validation of your research work. As a result, we assure you 0% copy/paste and 100% unique content . PhD research topics in mobile cloud computing have teams of experts in each phase of your study to guide you in the right way. So, you can approach us in any phase of your research.
We are the best to find your hidden success through our vision… Join us and find yours now…
Newly cultivated novel ideas from our topics in Mobile Cloud Computing are exemplified here,
The novel system for Decentralized and Revised Content-Centric Networking-Based Service Deployment and Discovery Platform in Mobile Edge Computing for IoT Devices
An effective mechanism for Data Offloading for Deadline-Varying Tasks in Mobile Edge Computing
A new progression function for Implementation of Vehicle Mobile Sales Cloud Management System Based on Intelligent Community scheme
An inventive thing for Flexible Fog Computing and Telecom Architecture for 5G Networks
The new methodology function for Energy-Optimal Scheduling of Mobile Cloud Computing Method
An innovative scheme intended for Ubiquitous Application Testing on Cloud
The novel performance for Computation offloading over a shared communication channel for mobile cloud computing
An effective function for Context-Aware File Discovery System for Distributed Mobile-Cloud Apps
An innovative mechanism for Clustering Algorithm Based on Communication Overhead and Link Stability for Cloud-assisted Mobile Adhoc Networks
The novel resource function based on Privacy Preserving Data Aggregation Scheme for Mobile Edge Computing Assisted IoT Applications
A new function based on omponent Importance Analysis of Mobile Cloud Computing System in the Presence of Common-Cause Failures
The new-fangled mechanism for Computation Offloading and Resource Allocation in Mixed Fog/Cloud Computing Systems With Min-Max Fairness Guarantee
The new process for Joint Optimization of Radio and Virtual Machine Resources With Uncertain User Demands in MCC
An effectual function for Resource Sharing of a Computing Access Point for Multi-User Mobile Cloud Offloading with Delay Constraints
An innovative performance for Promising Paradigm intended for Future Communication Systems
An efficient performance for Mobile Cloud Computing practice
The novel progression for Energy-Efficient Dynamic Computation Offloading and Cooperative Task Scheduling in Mobile Cloud Computing
An innovative mechanism for Analytics of Performance and Data Quality for Mobile Edge Cloud Applications
The novel function for Ensuring Data Integrity designed for Mobile Devices in Cloud Storage
An innovative method for Elasticity Debt Analytics Exploitation for Green Mobile Cloud Computing: An Equilibrium Model

Why Work With Us ?
Senior research member, research experience, journal member, book publisher, research ethics, business ethics, valid references, explanations, paper publication, 9 big reasons to select us.
Our Editor-in-Chief has Website Ownership who control and deliver all aspects of PhD Direction to scholars and students and also keep the look to fully manage all our clients.
Our world-class certified experts have 18+years of experience in Research & Development programs (Industrial Research) who absolutely immersed as many scholars as possible in developing strong PhD research projects.
We associated with 200+reputed SCI and SCOPUS indexed journals (SJR ranking) for getting research work to be published in standard journals (Your first-choice journal).
PhDdirection.com is world’s largest book publishing platform that predominantly work subject-wise categories for scholars/students to assist their books writing and takes out into the University Library.
Our researchers provide required research ethics such as Confidentiality & Privacy, Novelty (valuable research), Plagiarism-Free, and Timely Delivery. Our customers have freedom to examine their current specific research activities.
Our organization take into consideration of customer satisfaction, online, offline support and professional works deliver since these are the actual inspiring business factors.
Solid works delivering by young qualified global research team. "References" is the key to evaluating works easier because we carefully assess scholars findings.
Detailed Videos, Readme files, Screenshots are provided for all research projects. We provide Teamviewer support and other online channels for project explanation.
Worthy journal publication is our main thing like IEEE, ACM, Springer, IET, Elsevier, etc. We substantially reduces scholars burden in publication side. We carry scholars from initial submission to final acceptance.
Related Pages
Phd Research Topics In Mobile Computing
Phd Research Topics In Communication
Phd Consultancy Services
Phd Research Topics In Communication System
Phd Research Topics In Mobile Applications
Phd Research Topics In Computer Graphics
Phd Research Topics In Mobile Networking
Phd Research Topics In Computer Networking
Phd Consultancy Service In Tunisia
Phd Research Topics In Computer Networks
Phd Consultancy Service In Usa
Phd Research Topics In Computer Science
Phd Consultancy Service In Uk
Phd Research Topics In Communication Engineering
Phd Consultancy Service In United Arab Emirates
Our Benefits
Throughout reference, confidential agreement, research no way resale, plagiarism-free, publication guarantee, customize support, fair revisions, business professionalism, domains & tools, we generally use, wireless communication (4g lte, and 5g), ad hoc networks (vanet, manet, etc.), wireless sensor networks, software defined networks, network security, internet of things (mqtt, coap), internet of vehicles, cloud computing, fog computing, edge computing, mobile computing, mobile cloud computing, ubiquitous computing, digital image processing, medical image processing, pattern analysis and machine intelligence, geoscience and remote sensing, big data analytics, data mining, power electronics, web of things, digital forensics, natural language processing, automation systems, artificial intelligence, mininet 2.1.0, matlab (r2018b/r2019a), matlab and simulink, apache hadoop, apache spark mlib, apache mahout, apache flink, apache storm, apache cassandra, pig and hive, rapid miner, support 24/7, call us @ any time, +91 9444829042, [email protected].
Questions ?
Click here to chat with us
For enquiries call:
+1-469-442-0620

- Cloud Computing
Top 10 Cloud Computing Research Topics of 2024
Home Blog Cloud Computing Top 10 Cloud Computing Research Topics of 2024
Cloud computing is a fast-growing area in the technical landscape due to its recent developments. If we look ahead to 2024, there are new research topics in cloud computing that are getting more traction among researchers and practitioners. Cloud computing has ranged from new evolutions on security and privacy with the use of AI & ML usage in the Cloud computing for the new cloud-based applications for specific domains or industries. In this article, we will investigate some of the top cloud computing research topics for 2024 and explore what we get most out of it for researchers or cloud practitioners. To master a cloud computing field, we need to check these Cloud Computing online courses .
Why Cloud Computing is Important for Data-driven Business?
The Cloud computing is crucial for data-driven businesses because it provides scalable and cost-effective ways to store and process huge amounts of data. Cloud-based storage and analytical platform helps business to easily access their data whenever required irrespective of where it is located physically. This helps businesses to take good decisions about their products and marketing plans.
Cloud computing could help businesses to improve their security in terms of data, Cloud providers offer various features such as data encryption and access control to their customers so that they can protect the data as well as from unauthorized access.
Few benefits of Cloud computing are listed below:
- Scalability: With Cloud computing we get scalable applications which suits for large scale production systems for Businesses which store and process large sets of data.
- Cost-effectiveness : It is evident that Cloud computing is cost effective solution compared to the traditional on-premises data storage and analytical solutions due to its scaling capacity which leads to saving more IT costs.
- Security : Cloud providers offer various security features which includes data encryption and access control, that can help businesses to protect their data from unauthorized access.
- Reliability : Cloud providers ensure high reliability to their customers based on their SLA which is useful for the data-driven business to operate 24X7.
Top 10 Cloud Computing Research Topics
1. neural network based multi-objective evolutionary algorithm for dynamic workflow scheduling in cloud computing.
Cloud computing research topics are getting wider traction in the Cloud Computing field. These topics in the paper suggest a multi-objective evolutionary algorithm (NN-MOEA) based on neural networks for dynamic workflow scheduling in cloud computing. Due to the dynamic nature of cloud resources and the numerous competing objectives that need to be optimized, scheduling workflows in cloud computing is difficult. The NN-MOEA algorithm utilizes neural networks to optimize multiple objectives, such as planning, cost, and resource utilization. This research focuses on cloud computing and its potential to enhance the efficiency and effectiveness of businesses' cloud-based workflows.
The algorithm predicts workflow completion time using a feedforward neural network based on input and output data sizes and cloud resources. It generates a balanced schedule by taking into account conflicting objectives and projected execution time. It also includes an evolutionary algorithm for future improvement.
The proposed NN-MOEA algorithm has several benefits, such as the capacity to manage dynamic changes in cloud resources and the capacity to simultaneously optimize multiple objectives. The algorithm is also capable of handling a variety of workflows and is easily expandable to include additional goals. The algorithm's use of neural networks to forecast task execution times is a crucial component because it enables the algorithm to generate better schedules and more accurate predictions.
The paper concludes by presenting a novel multi-objective evolutionary algorithm-based neural network-based approach to dynamic workflow scheduling in cloud computing. In terms of optimizing multiple objectives, such as make span and cost, and achieving a better balance between them, these cloud computing dissertation topics on the proposed NN-MOEA algorithm exhibit encouraging results.
Key insights and Research Ideas:
Investigate the use of different neural network architectures for predicting the future positions of optimal solutions. Explore the use of different multi-objective evolutionary algorithms for solving dynamic workflow scheduling problems. Develop a cloud-based workflow scheduling platform that implements the proposed algorithm and makes it available to researchers and practitioners.
2. A systematic literature review on cloud computing security: threats and mitigation strategies
This is one of cloud computing security research topics in the cloud computing paradigm. The authors then provide a systematic literature review of studies that address security threats to cloud computing and mitigation techniques and were published between 2010 and 2020. They list and classify the risks and defense mechanisms covered in the literature, as well as the frequency and distribution of these subjects over time.
The paper suggests the data breaches, Insider threats and DDoS attack are most discussed threats to the security of cloud computing. Identity and access management, encryption, and intrusion detection and prevention systems are the mitigation techniques that are most frequently discussed. Authors depict the future trends of machine learning and artificial intelligence might help cloud computing to mitigate its risks.
The paper offers a thorough overview of security risks and mitigation techniques in cloud computing, and it emphasizes the need for more research and development in this field to address the constantly changing security issues with cloud computing. This research could help businesses to reduce the amount of spam that they receive in their cloud-based email systems.
Explore the use of blockchain technology to improve the security of cloud computing systems. Investigate the use of machine learning and artificial intelligence to detect and prevent cloud computing attacks. Develop new security tools and technologies for cloud computing environments.
3. Spam Identification in Cloud Computing Based on Text Filtering System
A text filtering system is suggested in the paper "Spam Identification in Cloud Computing Based on Text Filtering System" to help identify spam emails in cloud computing environments. Spam emails are a significant issue in cloud computing because they can use up computing resources and jeopardize the system's security.
To detect spam emails, the suggested system combines text filtering methods with machine learning algorithms. The email content is first pre-processed by the system, which eliminates stop words and stems the remaining words. The preprocessed text is then subjected to several filters, including a blacklist filter and a Bayesian filter, to identify spam emails.
In order to categorize emails as spam or non-spam based on their content, the system also employs machine learning algorithms like decision trees and random forests. The authors use a dataset of emails gathered from a cloud computing environment to train and test the system. They then assess its performance using metrics like precision, recall, and F1 score.
The findings demonstrate the effectiveness of the proposed system in detecting spam emails, achieving high precision and recall rates. By contrasting their system with other spam identification systems, the authors also show how accurate and effective it is.
The method presented in the paper for locating spam emails in cloud computing environments has the potential to improve the overall security and performance of cloud computing systems. This is one of the interesting clouds computing current research topics to explore and innovate. This is one of the good Cloud computing research topics to protect the Mail threats.
Create a stronger spam filtering system that can recognize spam emails even when they are made to avoid detection by more common spam filters. examine the application of artificial intelligence and machine learning to the evaluation of spam filtering system accuracy. Create a more effective spam filtering system that can handle a lot of emails quickly and accurately.
4. Blockchain data-based cloud data integrity protection mechanism
The "Blockchain data-based cloud data integrity protection mechanism" paper suggests a method for safeguarding the integrity of cloud data and which is one of the Cloud computing research topics. In order to store and process massive amounts of data, cloud computing has grown in popularity, but issues with data security and integrity still exist. For the proposed mechanism to guarantee the availability and integrity of cloud data, data redundancy and blockchain technology are combined.
A data redundancy layer, a blockchain layer, and a verification and recovery layer make up the mechanism. For availability in the event of server failure, the data redundancy layer replicates the cloud data across multiple cloud servers. The blockchain layer stores the metadata (such as access rights) and hash values of the cloud data and access control information
Using a dataset of cloud data, the authors assess the performance of the suggested mechanism and compare it to other cloud data protection mechanisms. The findings demonstrate that the suggested mechanism offers high levels of data availability and integrity and is superior to other mechanisms in terms of processing speed and storage space.
Overall, the paper offers a promising strategy for using blockchain technology to guarantee the availability and integrity of cloud data. The suggested mechanism may assist in addressing cloud computing's security issues and enhancing the dependability of cloud data processing and storage. This research could help businesses to protect the integrity of their cloud-based data from unauthorized access and manipulation.
Create a data integrity protection system based on blockchain that is capable of detecting and preventing data tampering in cloud computing environments. For enhancing the functionality and scalability of blockchain-based data integrity protection mechanisms, look into the use of various blockchain consensus algorithms. Create a data integrity protection system based on blockchain that is compatible with current cloud computing platforms. Create a safe and private data integrity protection system based on blockchain technology.
5. A survey on internet of things and cloud computing for healthcare
This article suggests how recent tech trends like the Internet of Things (IoT) and cloud computing could transform the healthcare industry. It is one of the Cloud computing research topics. These emerging technologies open exciting possibilities by enabling remote patient monitoring, personalized care, and efficient data management. This topic is one of the IoT and cloud computing research papers which aims to share a wider range of information.
The authors categorize the research into IoT-based systems, cloud-based systems, and integrated systems using both IoT and the cloud. They discussed the pros of real-time data collection, improved care coordination, automated diagnosis and treatment.
However, the authors also acknowledge concerns around data security, privacy, and the need for standardized protocols and platforms. Widespread adoption of these technologies faces challenges in ensuring they are implemented responsibly and ethically. To begin the journey KnowledgeHut’s Cloud Computing online course s are good starter for beginners so that they can cope with Cloud computing with IOT.
Overall, the paper provides a comprehensive overview of this rapidly developing field, highlighting opportunities to revolutionize how healthcare is delivered. New devices, systems and data analytics powered by IoT, and cloud computing could enable more proactive, preventative and affordable care in the future. But careful planning and governance will be crucial to maximize the value of these technologies while mitigating risks to patient safety, trust and autonomy. This research could help businesses to explore the potential of IoT and cloud computing to improve healthcare delivery.
Examine how IoT and cloud computing are affecting patient outcomes in various healthcare settings, including hospitals, clinics, and home care. Analyze how well various IoT devices and cloud computing platforms perform in-the-moment patient data collection, archival, and analysis. assessing the security and privacy risks connected to IoT devices and cloud computing in the healthcare industry and developing mitigation strategies.
6. Targeted influence maximization based on cloud computing over big data in social networks
Big data in cloud computing research papers are having huge visibility in the industry. The paper "Targeted Influence Maximization based on Cloud Computing over Big Data in Social Networks" proposes a targeted influence maximization algorithm to identify the most influential users in a social network. Influence maximization is the process of identifying a group of users in a social network who can have a significant impact or spread information.
A targeted influence maximization algorithm is suggested in the paper "Targeted Influence maximization based on Cloud Computing over Big Data in Social Networks" to find the most influential users in a social network. The process of finding a group of users in a social network who can make a significant impact or spread information is known as influence maximization.
Four steps make up the suggested algorithm: feature extraction, classification, influence maximization, and data preprocessing. The authors gather and preprocess social network data, such as user profiles and interaction data, during the data preprocessing stage. Using machine learning methods like text mining and sentiment analysis, they extract features from the data during the feature extraction stage. Overall, the paper offers a promising strategy for maximizing targeted influence using big data and Cloud computing research topics to look into. The suggested algorithm could assist companies and organizations in pinpointing their marketing or communication strategies to reach the most influential members of a social network.
Key insights and Research Ideas:
Develop a cloud-based targeted influence maximization algorithm that can effectively identify and influence a small number of users in a social network to achieve a desired outcome. Investigate the use of different cloud computing platforms to improve the performance and scalability of cloud-based targeted influence maximization algorithms. Develop a cloud-based targeted influence maximization algorithm that is compatible with existing social network platforms. Design a cloud-based targeted influence maximization algorithm that is secure and privacy-preserving.
7. Security and privacy protection in cloud computing: Discussions and challenges
Cloud computing current research topics are getting traction, this is of such topic which provides an overview of the challenges and discussions surrounding security and privacy protection in cloud computing. The authors highlight the importance of protecting sensitive data in the cloud, with the potential risks and threats to data privacy and security. The article explores various security and privacy issues that arise in cloud computing, including data breaches, insider threats, and regulatory compliance.
The article explores challenges associated with implementing these security measures and highlights the need for effective risk management strategies. Azure Solution Architect Certification course is suitable for a person who needs to work on Azure cloud as an architect who will do system design with keep security in mind.
Final take away of cloud computing thesis paper by an author points out by discussing some of the emerging trends in cloud security and privacy, including the use of artificial intelligence and machine learning to enhance security, and the emergence of new regulatory frameworks designed to protect data in the cloud and is one of the Cloud computing research topics to keep an eye in the security domain.
Develop a more comprehensive security and privacy framework for cloud computing. Explore the options with machine learning and artificial intelligence to enhance the security and privacy of cloud computing. Develop more robust security and privacy mechanisms for cloud computing. Design security and privacy policies for cloud computing that are fair and transparent. Educate cloud users about security and privacy risks and best practices.
8. Intelligent task prediction and computation offloading based on mobile-edge cloud computing
This Cloud Computing thesis paper "Intelligent Task Prediction and Computation Offloading Based on Mobile-Edge Cloud Computing" proposes a task prediction and computation offloading mechanism to improve the performance of mobile applications under the umbrella of cloud computing research ideas.
An algorithm for offloading computations and a task prediction model makes up the two main parts of the suggested mechanism. Based on the mobile application's usage patterns, the task prediction model employs machine learning techniques to forecast its upcoming tasks. This prediction is to decide whether to execute a specific task locally on the mobile device or offload the computation of it to the cloud.
Using a dataset of mobile application usage patterns, the authors assess the performance of the suggested mechanism and compare it to other computation offloading mechanisms. The findings demonstrate that the suggested mechanism performs better in terms of energy usage, response time, and network usage.
The authors also go over the difficulties in putting the suggested mechanism into practice, including the need for real-time task prediction and the trade-off between offloading computation and network usage. Additionally, they outline future research directions for mobile-edge cloud computing applications, including the use of edge caching and the integration of blockchain technology for security and privacy.
Overall, the paper offers a promising strategy for enhancing mobile application performance through mobile-edge cloud computing. The suggested mechanism might improve the user experience for mobile users while lowering the energy consumption and response time of mobile applications. These Cloud computing dissertation topic leads to many innovation ideas.
Develop an accurate task prediction model considering mobile device and cloud dynamics. Explore machine learning and AI for efficient computation offloading. Create a robust framework for diverse tasks and scenarios. Design a secure, privacy-preserving computation offloading mechanism. Assess computation offloading effectiveness in real-world mobile apps.
9. Cloud Computing and Security: The Security Mechanism and Pillars of ERPs on Cloud Technology
Enterprise resource planning (ERP) systems are one of the Cloud computing research topics in particular face security challenges with cloud computing, and the paper "Cloud Computing and Security: The Security Mechanism and Pillars of ERPs on Cloud Technology" discusses these challenges and suggests a security mechanism and pillars for protecting ERP systems on cloud technology.
The authors begin by going over the benefits of ERP systems and cloud computing as well as the security issues with cloud computing, like data breaches and insider threats. They then go on to present a security framework for cloud-based ERP systems that is built around four pillars: access control, data encryption, data backup and recovery, and security monitoring. The access control pillar restricts user access, while the data encryption pillar secures sensitive data. Data backup and recovery involve backing up lost or failed data. Security monitoring continuously monitors the ERP system for threats. The authors also discuss interoperability challenges and the need for standardization in securing ERP systems on the cloud. They propose future research directions, such as applying machine learning and artificial intelligence to security analytics.
Overall, the paper outlines a thorough strategy for safeguarding ERP systems using cloud computing and emphasizes the significance of addressing security issues related to this technology. Organizations can protect their ERP systems and make sure the Security as well as privacy of their data by implementing these security pillars and mechanisms.
Investigate the application of blockchain technology to enhance the security of cloud-based ERP systems. Look into the use of machine learning and artificial intelligence to identify and stop security threats in cloud-based ERP systems. Create fresh security measures that are intended only for cloud-based ERP systems. By more effectively managing access control and data encryption, cloud-based ERP systems can be made more secure. Inform ERP users about the security dangers that come with cloud-based ERP systems and how to avoid them.
10. Optimized data storage algorithm of IoT based on cloud computing in distributed system
The article proposes an optimized data storage algorithm for Internet of Things (IoT) devices which runs on cloud computing in a distributed system. In IoT apps, which normally generate huge amounts of data by various devices, the algorithm tries to increase the data storage and faster retrials of the same.
The algorithm proposed includes three main components: Data Processing, Data Storage, and Data Retrieval. The Data Processing module preprocesses IoT device data by filtering or compressing it. The Data Storage module distributes the preprocessed data across cloud servers using partitioning and stores it in a distributed database. The Data Retrieval module efficiently retrieves stored data in response to user queries, minimizing data transmission and enhancing query efficiency. The authors evaluated the algorithm's performance using an IoT dataset and compared it to other storage and retrieval algorithms. Results show that the proposed algorithm surpasses others in terms of storage effectiveness, query response time, and network usage.
They suggest future directions such as leveraging edge computing and blockchain technology for optimizing data storage and retrieval in IoT applications. In conclusion, the paper introduces a promising method to improve data archival and retrieval in distributed cloud based IoT applications, enhancing the effectiveness and scalability of IoT applications.
Create a data storage algorithm capable of storing and managing large amounts of IoT data efficiently. Examine the use of cloud computing to improve the performance and scalability of data storage algorithms for IoT. Create a secure and privacy-preserving data storage algorithm. Assess the performance and effectiveness of data storage algorithms for IoT in real-world applications.
How to Write a Perfect Research Paper?
- Choose a topic: Select the topic which is interesting to you so that you can share things with the viewer seamlessly with good content.
- Do your research: Read books, articles, and websites on your topic. Take notes and gather evidence to support your arguments.
- Write an outline: This will help you organize your thoughts and make sure your paper flows smoothly.
- Start your paper: Start with an introduction that grabs the reader's attention. Then, state your thesis statement and support it with evidence from your research. Finally, write a conclusion that summarizes your main points.
- Edit and proofread your paper. Make sure you check the grammatical errors and spelling mistakes.
Cloud computing is a rapidly evolving area with more interesting research topics being getting traction by researchers and practitioners. Cloud providers have their research to make sure their customer data is secured and take care of their security which includes encryption algorithms, improved access control and mitigating DDoS – Deniel of Service attack etc.,
With the improvements in AI & ML, a few features developed to improve the performance, efficiency, and security of cloud computing systems. Some of the research topics in this area include developing new algorithms for resource allocation, optimizing cloud workflows, and detecting and mitigating cyberattacks.
Cloud computing is being used in industries such as healthcare, finance, and manufacturing. Some of the research topics in this area include developing new cloud-based medical imaging applications, building cloud-based financial trading platforms, and designing cloud-based manufacturing systems.
Frequently Asked Questions (FAQs)
Data security and privacy problems, vendor lock-in, complex cloud management, a lack of standardization, and the risk of service provider disruptions are all current issues in cloud computing. Because data is housed on third-party servers, data security and privacy are key considerations. Vendor lock-in makes transferring providers harder and increases reliance on a single one. Managing many cloud services complicates things. Lack of standardization causes interoperability problems and restricts workload mobility between providers.
Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) are the cloud computing scenarios where industries focusing right now.
The six major components of cloud infrastructure are compute, storage, networking, security, management and monitoring, and database. These components enable cloud-based processing and execution, data storage and retrieval, communication between components, security measures, management and monitoring of the infrastructure, and database services.

Vinoth Kumar P
Vinoth Kumar P is a Cloud DevOps Engineer at Amadeus Labs. He has over 7 years of experience in the IT industry, and is specialized in DevOps, GitOps, DevSecOps, MLOps, Chaos Engineering, Cloud and Cloud Native landscapes. He has published articles and blogs on recent tech trends and best practices on GitHub, Medium, and LinkedIn, and has delivered a DevSecOps 101 talk to Developers community , GitOps with Argo CD Webinar for DevOps Community. He has helped multiple enterprises with their cloud migration, cloud native design, CICD pipeline setup, and containerization journey.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cloud Computing Batches & Dates
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List

Privacy and data protection in mobile cloud computing: A systematic mapping study
Hussain mutlaq alnajrani.
1 Faculty of Computing Science and Information Technology, University of Malaya, Kuala Lumpur, Malaysia
2 Faculty of Computer Science and Information Technology, Albaha University, Albaha, Saudi Arabia
Azah Anir Norman
Babiker hussien ahmed, associated data.
All relevant data are within the manuscript.
As a result of a shift in the world of technology, the combination of ubiquitous mobile networks and cloud computing produced the mobile cloud computing (MCC) domain. As a consequence of a major concern of cloud users, privacy and data protection are getting substantial attention in the field. Currently, a considerable number of papers have been published on MCC with a growing interest in privacy and data protection. Along with this advance in MCC, however, no specific investigation highlights the results of the existing studies in privacy and data protection. In addition, there are no particular exploration highlights trends and open issues in the domain. Accordingly, the objective of this paper is to highlight the results of existing primary studies published in privacy and data protection in MCC to identify current trends and open issues. In this investigation, a systematic mapping study was conducted with a set of six research questions. A total of 1711 studies published from 2009 to 2019 were obtained. Following a filtering process, a collection of 74 primary studies were selected. As a result, the present data privacy threats, attacks, and solutions were identified. Also, the ongoing trends of data privacy exercise were observed. Moreover, the most utilized measures, research type, and contribution type facets were emphasized. Additionally, the current open research issues in privacy and data protection in MCC were highlighted. Furthermore, the results demonstrate the current state-of-the-art of privacy and data protection in MCC, and the conclusion will help to identify research trends and open issues in MCC for researchers and offer useful information in MCC for practitioners.
1. Introduction
In recent years, mobile cloud computing (MCC) is playing a crucial role in connectivity and accessibility to services and applications [ 1 ]. MCC is a major area of interest evolving out of mobile devices and cloud computing [ 1 – 3 ]. It is an approach that aims to enable mobile terminals to access robust and reliable cloud-based computing that facilitates the optimal utilization of resources.
As an effect of a major concern of cloud users, the issue of privacy and data protection has received considerable attention in the field. A number of researchers have reported that privacy in the definition adopted by the organization for Economic Cooperation and Development [ 4 ] is “any information relating to a recognized or identifiable individual (data subject).” In fact, the concept of privacy has a different perspective, depending on countries, cultures, or jurisdictions.
Recently, researchers have shown an increased interest in MCC. Currently, a considerable number of papers have been published on MCC with a growing interest in privacy and data protection. Along with this advance in MCC, the results of the existing studies in privacy and data protection are not highlighted. Also, no particular research demonstrates the ongoing trends, measures to assess current solutions, and open research issues, including future research directions for privacy and data protection in MCC.
In this study, a systematic mapping study (SMS) was conducted to analyses the existing research literature that addresses privacy and data protection in MCC [ 3 ]. In fact, SMS is a clear and precise method of identifying, evaluating, and explaining all obtainable research relevant to a specific research question, thematic area, or phenomenon of importance [ 3 ]. Furthermore, the purpose of SMS is to present an adjustable, impartial, and reliable assessment of a particular research topic [ 3 ].
The study presented in this paper aims to highlight the results of existing primary studies published in privacy and data protection in MCC to identify current trends and open issues in the domain. In this examination, a systematic mapping study (SMS) was conducted with a set of six research questions. A total of 1711 studies published from 2009 to 2019 were obtained. Following a filtering process, a collection of 74 primary studies were selected. As a result, the contribution of this study is declared as follows:
- Demonstrate existing threats and attacks on data privacy and solutions to serve personal data.
- Outline metrics and measures that are used to assess the current solutions for privacy in MCC.
- Illustrate the current state-of-the-art of data privacy exercises utilized in MCC and highlight the types of research and contribution areas that are used in mobile cloud computing.
- Highlight open research issues of privacy and data protection in MCC.
This article is constructed as follows: Section 2 presents background and motivation for the study. Section 3 presents the related work. Section 4 describes the research method. Section 5 presents conducting the study. Section 6 shows and discusses the results. Section 7 illustrates the key findings. Section 8 clarifies the thread to the validity. Section 9 presents the conclusion of this study.
2. Background and motivation
This section presents a general background of mobile cloud computing, privacy and data protection, and the needs for a systemic mapping study.
2.1. Mobile cloud computing
Today, mobile devices such as smartphones provide users with greater connectivity and accessibility to services and applications [ 1 ]. Even though mobile technology continues to expand, modern mobile terminals suffer limitations associated with poor computational resources, low memory size, and small disk capacity [ 1 ]. Cloud computing provides a robust approach to the delivery of services by incorporating existing computing technologies. In cloud computing, three service delivery models appear to account for most deployments: Infrastructure-as-a-service (IaaS), Software-as-a-Service (SaaS), and Platform-as-a-Service (PaaS) [ 5 ].
The concept of Mobile Cloud Computing (MCC) has emerged out of mobile technology and cloud computing [ 1 – 3 ]. It is an approach that aims to enable mobile terminals to access robust and reliable cloud-based computing that facilitates the optimal utilization of resources. Moreover, MCC presents opportunities for improving the portability and scalability of services [ 1 ].
2.2. Privacy and data protection
Several researchers have reported that privacy in the definition adopted by the organization for Economic Cooperation and Development [ 4 ] is “any information relating to a recognized or identifiable individual (data subject).” In fact, the concept of privacy is vast and has a different perspective depending on countries, cultures, or jurisdictions.
To be more precise, privacy is not just about hiding information, but it is a legitimate control over personal data since no one may get personal information without the consent of the owner unless there are laws that allow access to such information [ 6 ], for example, income information that the tax authorities can get from employers [ 6 ].
The issue of privacy in MCC is getting nowadays more attention; however, numerous existing privacy laws and regulations are needed to impose the standards for the collection, maintenance, use, and disclosure of personal information that must be satisfied even by cloud providers [ 7 ]. In addition, a number of studies reported that there is always increasing the privacy risk in hosting your data in someone else’s hands [ 7 ].
2.3. The need for a systematic mapping study
Currently, a considerable number of papers have been published on MCC with a growing interest in privacy and data protection. Along with this advance in MCC, our research group has found the following:
- The results of the existing studies in privacy and data protection were not highlighted.
- The ongoing trends in privacy and data protection were not determined.
- The metrics used to assess current solutions were not aggregated.
- The research type facets and the contribution type facets used in MCC were not aggregated.
- The current open research issues with future research directions were not demonstrated.
The aim of this investigation is to highlight the results of the existing studies in privacy and data protection in MCC through a systematic mapping study (SMS). The purpose of a systematic mapping study is to present an adjustable, impartial, and reliable assessment of a particular research topic [ 3 ]. Also, SMS is used to highlight the current state-of-the-art and to determine the trends of the research domain.
3. Related works
In recent years, a number of reviews and surveys have been published to analyze MCC in secondary studies [ 8 – 11 ] and are considered as related to this study. David et al. [ 8 ] focused on the various encryption techniques (and their variants) that are presently being utilized, and on possible future works that could improve privacy-oriented encryption techniques and security. Moreover, the authors tried to provide the audience with a conception about the difficulty of the algorithm being utilized in each of the studied encryption techniques. However, they did not cover other solutions or discuss current attacks and threats related to MCC.
Also, Kulkarni et al. [ 9 ] concentrated on the existing frameworks of MCC, although they did not mention other solutions. In addition, Bhatia and Verma [ 10 ] presented a state-of-the-art organization of cryptographic techniques and data security schemes in an innovative delimitation on chronological order. However, the survey only focused on threats and attacks related to the mobile cloud. Moreover, Rahimi et al. [ 11 ], investigated various security frameworks for the MCC environment, whereby most of them offload processor-heavy jobs to the cloud. The study [ 11 ] suggested some of the challenges that service providers need to address to achieve security and privacy in the MCC environment [ 11 ]. Finally, even though several reviews and surveys have been reported, two limitations remain:
- There is a need for a more systematic way of summarizing the current knowledge in MCC. It is known that the popularity of these studies is as informal literature surveys, which do not include specific research questions, search process, or defined data analysis processor data extractions.
- A few secondary studies focused on privacy and data protection in MCC, while applications based on these platforms continue to multiply.
4. Research method
A systematic mapping study (SMS) is a secondary study that provides a structure of the type of research papers and aggregates the results that have been declared in the domain. Also, SMS is a method for categorizing the published studies, often gives a visual summary, and map the results to highlight the current state-of-the-art and to determine the trends [ 12 ].
In this paper, we have derived the formal guidelines of SMS from Petersen et al. [ 12 ]. As in the directive of SMS [ 12 ], SMS is performed in five steps where the outcome from each step provides the input for the next step. Fig 1 shows the SMS method, as demonstrated in Petersen et al. [ 12 ]. As shown in Fig 1 , SMS is implemented as follows [ 12 ]:

- Step 1 : Define research questions and objectives to provide a general scope for the study.
- Step 2 : Define the search strategy to find the published studies from the available digital libraries.
- Step 3 : Screening process using inclusion and exclusion criteria to choose the relevant studies.
- Step 4 : Keywording to enable classification and data extraction.
- Step 5: Data extraction and mapping process.
4.1. Research aim questions and objectives
The study aims to highlight the results of existing primary studies published in privacy and data protection in MCC to identify current trends and open issues in the domain. Table 1 shows our research questions and the objective of each research question.
4.2. Search strategy
As in the SMS guideline [ 13 ], the primary studies are identified by using a search string [ 13 ] derived from the research questions. An excellent way to create the search string is to structure them in terms of population, intervention, comparison, and outcome (PICO) [ 13 ]. Based on our research questions in Table 1 , PICO is implemented as follows:
- Population : Published studies.
- Intervention : Privacy, data protection, mobile cloud computing, and MCC.
- Comparison : Not applicable.
- Outcome : Published studies in privacy and data protection in mobile cloud computing.
Based on PICO, we constructed our search string as presented in Fig 2 . In this SMS, the search string in Fig 2 is handled to search for studies in the available digital libraries.

4.3. Inclusion-exclusion criteria
Based on SMS guidelines [ 13 ], applying inclusion and exclusion criteria is crucial to filter the results [ 13 ]. Inclusion and exclusion criteria aim to obtain relevant primary studies to answer the defined research questions [ 13 ]. Table 2 illustrates our inclusion and exclusion criteria.
4.4 Keywording and classification for data extraction
For the SMS data extraction and classification, the SMS method [ 14 ] declared the following:
- ➢ Ensure that the desired results were covered in the SMS [ 14 ].
- ➢ Aid in introducing a set of categories that represent the underlying population for the study [ 14 ].
- ➢ Develop a high-level understanding of the nature and contribution of the selected primary studies [ 13 ].
- ➢ First, read the abstracts and searched for keywords [ 14 ].
- ➢ Second, identify the context related to the objective of the study and the scheme will be updated [ 14 ].
- Scheme: When having the classification scheme in place, the relevant articles are sorted into the scheme, i.e., the actual data extraction takes place [ 13 ].
As presented in Fig 3 , the classification scheme is implemented as follows:

- Keywording: is the process of reading the abstract and searching for keywords to identify the context related to the objective of the SMS [ 14 ].
- Sort Article into scheme: is the process of sorting the scheme after adding an article into scheme [ 14 ].
- Update scheme: is the process of modifying the scheme after adding a primary study context to the scheme [ 14 ].
4.5 Data extraction and mapping process
As demonstrated in the SMS method [ 13 ], in this study, we use a data extraction form to gather the SMS data. In addition, when having the classification scheme in place, the actual data extraction of the relevant articles in this study is sorted into the scheme as follows:
- Excel tables were utilized to document the data extraction process [ 13 ].
- The frequencies of publications in each category were analyzed from the final table [ 13 ].
To investigate the trends, as in the SMS method [ 13 ], we focused on the frequencies of publications for each category to identify which categories have been emphasized in past research and thus to identify gaps and possibilities for future research. Also, different ways of presenting and analyzing the results were utilized as follows:
- The summary of the statistics is illustrated in the form of tables, showing the frequencies of publications in each category [ 13 ].
- A bubble plot is illustrated to report the frequencies [ 13 ]. Bubble plot is basically two x-y scatterplots with bubbles in category intersections. The size of a bubble is proportional to the number of articles that are in the pair of categories corresponding to the bubble coordinates [ 13 ].
5. Conducting SMS
In this section, we present the systematic mapping study that we have conducted using the SMS method presented in Section 4.
5.1. Selecting and filtering relevant studies
In this study, we applied PRISMA (Preferred Reporting Items for Systematic Reviews and Meta-Analyses) guidelines [ 15 ] as an evidence-based for reporting the outcome of the search results to clarify the eligible, included or excluded primary studies in this investigation. Fig 4 demonstrates the resulting articles from each database and the screened primary studies for this study using the PRISMA guideline.

As Fig 4 , in this investigation, five digital databases we selected to search for relevant studies, including IEEE Xplore, Science Direct, Springer Link, ACM Digital Library, and Scopus. Then, we utilized our search string, as presented in Fig 2 , to search for studies in the selected databases. As a result, 1711 studies were obtained and screened as follows:
- By article type: only the studies presented in conferences, magazines, and journals venues initially selected.
- By subject: only the studies related to privacy, data protection, mobile cloud computing, and MCC initially nominated.
- By title: only the studies related to mobile cloud computing initially nominated.
Finally, after screening by year, article type, subject, and title, a total of 215 studies were initially selected and presented in Table 3 .
In filtering the retrieved studies, a total of 87 studies were excluded based on our inclusion and exclusion criteria ( Table 2 ). Also, 39 duplicated studies were eliminated. In addition, we read a sum of 89 studies in a comprehensive analysis. The comprehensive analysis is a process of reading the whole primary study and decide to include or exclude it after a complete investigation on the actual contribution on exactly and only on the privacy and data protection in mobile cloud computing. Finally, a total of 74 primary studies were selected for SMS. Table 4 shows the results of filtering the retrieved studies.
5.3. Analysis and classification
In this study, we carried out a classification scheme through keywording as declared in Section 4.4. First, we read the abstracts of the 74 selected primary studies and searched for keywords. In addition, we read the introduction and conclusion sections of each of the selected primary studies to produce the classification scheme. As an outcome, Fig 5 shows our classification scheme.

As presented in Fig 5 , seven main aspects were defined as follows:
- Data privacy exercises: It denotes the methods of controlling and implementing privacy solutions in mobile cloud computing [ 16 ]. Also, it concerns the demonstration of practice policies of data access using different mechanisms [ 17 ] that governed by the policies of MCC service providers, state regulations and roles.
- ➢ Threat: Potential for infringement of security, which exists when there is a situation, capacity, activity, or occasion that could violate security and cause harm. That is, a risk is a possible peril that may misuse a vulnerability [ 18 ].
- ➢ Attack : A violation of system security that derives from an intelligent threat. This intelligent work is a purposed attempt (especially in the concept of a technique or method) to avoid the security policy of a system and security services [ 18 ].
- Privacy Solutions : These are computational methods serving issues related to authentication, authorization, encryption, access control, and trust.
- Metrics : Privacy metrics are the privacy parameters that are required in measuring the level of privacy in MCC or the privacy service provided by a given solution to MCC [ 19 ].
- Research type : We adopted an existing classification (Wieringa, Maiden, Mead, & Rolland, 2006), which is divided into six classifications: Validation Research, Solution Proposal, Evaluation Research, Philosophical Paper, Opinion Paper, and Experience Paper [ 20 ]. S1 Appendix of Appendix A shows the types of research with the definitions [ 20 ] used in our mapping study.
- Contribution type : For the contribution type facets, we have used the categories from Petersen et al., (2008): Model, Formal Study, Method, System, and Experience [ 20 ]. S1 Appendix of Appendix B shows the definitions of the contribution type facets used in our mapping study.
- Open research issues : is a new challenge noted by the researchers in the existing studies in the area.
6. Results and discussion
In this section, we present and discuss the answers to the research questions of this study.
6.1. RQ1: What are the current data privacy exercises in MCC?
In this study, we have identified eight data privacy exercises; these eight exercises have been highlighted in the selected primary studies for implementing privacy solutions in MCC. Table 5 illustrates the identified data privacy exercises in the selected primary studies.
In addition, more details are necessary to understand those exercises presented in Table 5 ; those data privacy exercises are defined as follows:
- Setup: is concerning the adaptation of the initial public parameters of system, account, and algorithm for privacy and data protection in MCC [ 26 , 27 ].
- Cryptography: is defined as the method of preserving information by using codes, such that it can only be read and interpreted by those for whom the information is targeted [ 18 ].
- Authentication: it denotes the assurance that the communicating entity is the one that it claims to be [ 18 ].
- Accounts creation: It represents the registration of a mobile device or user to a cloud server is an onetime process wherein the user information (ID, password) are Setup, and some encrypted files are exchanged [ 70 ].
- Verification: is utilized to illustrate the information that corroborates the binding between the entity and the identifier [ 18 ].
- Access control: is the prevention of unauthorized use of a resource [ 18 ].
- Steganography: is used for hiding plaintext messages by concealing the existence of the message [ 18 ].
- Reputation: is one of the components of trustworthiness measures. The reputation establishes based on the recommendations from the MCC users [ 78 ].
Fig 6 shows the percentage of studies related to data privacy exercises based on the number of studies. As presented in Fig 6 , the results show that the selected primary studies focused on setup, cryptography, authentication, account creation, and verification in 25%, 22%, 21%, 14%, and 11% of studies, respectively. On the other hand, access control, steganography, and reputation have scored the lowest percentage with less than 5% each.

Moreover, Fig 7 is a bubble plot of data privacy exercises in the selected primary studies; the X-axis represents the years, and the Y-axis represents the data privacy exercises. As illustrated in Fig 7 , the number of research rises towards the setup, cryptography, authentication, and accounts creation. Conversely, the number of research decreased towards verification, access control, steganography, and reputation.

6.2. RQ 2: What are the existing data privacy threats and attacks in MCC?
In this investigation, we have identified 17 data privacy threats and attacks in MCC. Table 6 shows the identified threats and attacks in the selected primary studies.
Fig 8 displays the percentage of primary studies related to threats and attacks based on the number of studies. As demonstrated in Fig 8 , the most common threats and attacks are unauthorized threats and attacks including users, persons, and access with 18% (34), data privacy with 15% (29), leakage of user privacy 13% (24), data misuse (21) and untrusted service provider (21) represented 11% each. On the other hand, disclosing information or data (11) represented 6%, man-in-the-middle attacks (9) represented 5%, and the rest of the threats got 21%, respectively.

Furthermore, Fig 9 is a bubble plot of threats and attacks, the X-axis represents the years, and the Y-axis represents the threats and attacks. The results show that unauthorized, data privacy, leakage of user privacy, and phishing attacks are relatively dominant in the field. In contrast, eavesdropping attacks, internal attacks, improper security policies and practices in some locations, internal multi-layer attacks, inference attacks on user privacy, and data breach threats are losing momentum.

6.3. RQ3: What are the privacy solutions proposed to serve personal data protection in MCC?
As shown in Table 7 , four solutions used to preserve the privacy in MCC in the selected primary studies. The solutions include encryption, authentication, access control, and trust.
Fig 10 displays the percentage of studies related to privacy solutions based on the number of studies. The outcome shows that the research focused on encryption, authentication, and access control solutions in 50%, 28%, and 19% of studies, respectively. We observed that researchers have started to propose trust as a solution in this domain since we found two studies presented the trust solutions.

Moreover, Fig 11 is a bubble plot of privacy solutions with the X-axis representing the years and the Y-axis representing data privacy solutions. The result in Fig 11 determines that the amount of research is increasing towards the encryption and the authentication data privacy solutions. On the other hand, research into trust data privacy solutions is abating.

6.4. RQ4: What are the metrics and measures that are used to assess the current solutions of privacy and data protection in MCC?
As shown in Table 8 , we divided the answer into two parts as follows:
- The first part of Table 8 presents the resources usage metrics, where we found that the highest utilized metric is time consumption, which is represented in 32 studies, followed by communication overhead in 26 studies. The results display that energy consumption, memory consumption on mobile devices, and turnaround-time resources usage metrics received the least attention in the selected primary studies.
- The second part of Table 8 shows the contained solution robustness metrics. The results show two studies for each of the effective recommendation rate, accuracy, authentication request, and authentication response. Also, the results show one study for each of the data randomization, a malicious node detection and management performance (MDP), the addition of new users, operations required, authorities, and privacy and reliability factors.
As illustrated in Fig 12 , the time consumption is the most used metric resulted in 43%. Followed by communication overhead metrics with 35%. Finally, energy consumption, memory consumption, and turnaround time are presented in 15%, 4%, and 3%, respectively.

As expounded in Fig 13 , the effective recommendation rate, accuracy, authentication response, and authentication request are the most used metrics with 15%, 15%, 14%, and 14%, respectively. One the other hand, the result shows that most of the solution robustness metrics were employed in less than 8% of the selected primary studies.

For recognizing metrics and measures trends in MCC, we present the trends in a bubble plot in Fig 14 , the X-axis represents the years, and the Y-axis represents metrics and measures. The outcome indicates that the amount of research in the selected primary studies is increasing towards time consumption, overhead communication, and energy consumption metrics. On the other hand, the number of studies in memory consumption and turnaround time is receiving less attention.

6.5. RQ 5: What research type facets and contribution type facets are used in MCC?
To answer the first part of this question, we studied the proportion of papers by research type, as shown in Table 9 and Fig 15 . Our studies found the solution proposals are the most published studies with 31 papers (42%), followed by the evaluation research with 23 papers (31%). In contrast, there are 11 philosophical papers (14%), five validation research (6%), and four opinion papers (5%).

To answer the second part of the question, we studied the proportion of papers by research type, as shown in Table 9 and Fig 16 . Our studies found the most popular contribution type is the model with 33 papers (45%), followed by the method with 22 papers (30%). In contrast, there are only ten system contributions (13%), and nine Formal studies (12%).

To discover the research type facets in MCC trends, we illustrate the trends in a bubble plot ( Fig 17 ), the X-axis represents the years, and the Y-axis represents the research type. As demonstrated in Fig 17 , the amount of research in the selected primary studies is increasing towards the solution proposal and the evaluation research. On the other hand, the number of validation research and opinion paper research type facets are decreasing.

To discover the contribution type facets in MCC, we illustrate the trends in a bubble plot ( Fig 18 ), the X-axis represents the years, and the Y-axis represents the contribution type. The outcome shows that the models and the methods are relatively dominant in the field, and the systems and the formal studies are losing momentum in the domain.

6.6. RQ 6: What are the currently open research issues of privacy and data protection in MCC?
In this study, we have identified nine main open research issues with 23 examples of future research directions suggested by the authors in privacy and data protection in MCC. Table 10 shows the identified open research issues in the selected primary studies.
Furthermore, Fig 19 displays the open research issues in privacy and data protection based on the number of studies. As illustrated in Fig 19 , security, authentication, privacy, and encryption were getting momentum in 31%, 13%, 13%, and 13%, respectively. On the other hand, energy consumption, trust, various attacks, architectures, and testing addressed in less than 10% of the selected primary studies for each of them.

7. Key findings
In this study, a systematic mapping study was conducted with a set of six research questions. A total of 1711 studies published from 2009 to 2019 were obtained. Following a filtering process, a set of 74 primary studies were selected. In this section, we summaries the key findings of this study as follows:
- The current data privacy exercise in MCC : This study shows that the exercises of cryptography, authentication, account creation, and verification were getting significant attention in 93% of the selected primary studies. In contrast, access control, steganography, and reputation with less attention in less than 8% of the selected primary studies. Also, our results show that the amount of research is increasing in the setup, cryptography, authentication, and accounts creation. Conversely, the outcome shows that the research in verification, access control, steganography, and reputation are losing momentum.
- The data privacy threats and attacks in MCC : The results of this SMS show that the issues of unauthorized, data privacy, leakage of user privacy, data misuse, and untrusted service provider were receiving the most consideration in 68% of the selected primary studies. On the other hand, internal attacks, improper security policies and practices in some locations, internal multi-layer attacks, inference attacks on user privacy, and data breach threats were received less consideration with fewer than 6% of the selected primary studies. Also, our results show that unauthorized, data privacy, leakage of user privacy, and phishing attacks are relatively dominant. Conversely, the outcome indicates that the research in eavesdropping attacks, internal attacks, improper security policies and practices in some locations, internal multi-layer attacks, inference attacks on user privacy, and data breach threats have the lowest studies in the domain.
- The privacy solutions proposed to serve personal data protection in MCC : The results of this SMS show that the encryption, authentication, and access control of the solutions in MCC were getting the highest attention in 97% of the selected primary studies. Trust solutions had the lowest concern in the field with less than 4%. Furthermore, the amount of research is increasing in encryption and the authentication of data privacy solutions in MCC. Contrary to expectations, the outcome shows that the research in the trust solutions in MCC is less likely than expected with only 3% of the selected primary studies.
- ➢ It is interesting to note that this study identified five resources usage metrics and ten solution robustness metrics. In resource usage metrics, around 78% of primary studies assess the time consumption and the communication overhead. In solution robustness metrics, an effective recommendation rate and accuracy were gotten 30% of primary studies.
- ➢ In resource usage metrics, the amount of research is increasing in time consumption and communication overhead metrics and measures. In contrast, energy consumption, memory consumption, and turnaround time are utilized in less than 23% of the selected papers. Furthermore, less than 4% of the primary studies used turnaround time metrics, which indicated that the turnaround time measures are less popular in the domain.
- ➢ In solution robustness metrics, the recognized data randomization, a malicious node detection and the management performance, the addition of new users, operations required, authorities, privacy and reliability factors, authentication requests, and authentication, were gotten less than 8% of the selected papers. On the other hand, the amount of research is increasing in accuracy and effective recommendation of metrics and measures in MCC. Conversely, the outcome shows that the research on privacy and reliability is not dominant in the area.
- The research type facets in MCC: The results show that the solution proposals and evaluation research got considerable attention in 73% of the selected primary studies. The validation research and the opinion papers with the lowest examinations with less than 13% of the selected primary studies. The amount of research is increasing in the solution proposal and evaluation research type. Conversely, the outcome shows that the research in the validation research and opinion paper is losing momentum.
- The Contribution type facets in MCC: The results of this SMS show that the models and the methods got the highest attention in 75% of the selected primary studies. Also, systems and formal studies had gotten the lowest studies in the field with less than 26% of the selected primary studies. In addition, our results show that the amount of research is increasing in the models and the methods of the contribution type facets. Surprisingly, the research in the systems and formal studies are decreased in the selected primary studies.
- Open research issues: In this study, we identified the new challenges in privacy and data protection in MCC, which were noted by the researchers in the selected primary studies. As presented in the previous SMS [ 95 ], the issues that emerged ten years ago are still considered open issues [ 95 ]. Our exploration shows that there are open research issues in encryption, authentication, security, trust, signature-based privacy, architectures, various attacks, testing, and energy consumption. In this SMS, as illustrated in Table 10 , 23 examples of future research directions suggested by the authors are useful for research activities in the future.
8. Threats to validity
The process of SMS is not infallible as with any secondary research method. There are many risks to consider for ensuring the validity of this SMS study. In this part, we describe and relieve the risks to the validity of this study to mitigate the potential risks. The risks include the search criteria, digital databases, and inclusion and exclusion criteria [ 96 ].
8.1. Search criteria
In this examination, the highest attention paid for choosing the most useful search strings. In particular, the construction of the search string is a threat to the validity of this study [ 96 ]. To mitigate this threat, our search string is derived based on PICO criteria [ 13 ]. PICO criteria are popular and widely used in the SMS, and this would enable us to retrieve the wanted studies in the search result and mitigate the threat.
8.2. Digital databases
For this study, the selection of databases, including IEEE Xplore, Science Direct, Springer Link, ACM Digital Library, and Scopus is a threat to the validity of the study since related studies would not be included in those databases. To mitigate this threat, as presented in Kitchenham et al. [ 97 ], and pointed out by Dyba et al. [ 98 ], the selection of IEEE, ACM, and any two databases are enough to save time and effort for general rather than searching multiple publishers’ digital databases [ 97 , 98 ]. Accordingly, in this examination, we selected five databases, including IEEE and ACM, which will mitigate the threat.
8.3. Inclusion and exclusion criteria
In this exploration, the rules and conditions of our inclusion and exclusion criteria are defined to be ranged with the scope of the study. The criteria stemmed from discussions within the research team. However, producing rules to recognize the initial literature to review; means that there is a threat that relevant research may be ignored if it employs various terms to that of the criteria. However, primary search terms of the study’s, namely Privacy, data protection in mobile cloud computing (MCC), are traditional, well-defined and accepted terms, which should decrease the number of ignored studies. Moreover, as the study is focused on identifying the main research in privacy and data protection in the mobile cloud computing, there is not as much of a concern with capturing research that is loosely related to the domain.
9. Conclusion
Mobile cloud computing (MCC) is a significant area of research emerging out of mobile devices and cloud computing [ 3 ]. In recent years, a significant number of studies have been published with a growing interest in privacy and data protection. Along with this advance in MCC, however, no specific research identified the current trends and open issues in privacy and data protection in MCC. This study highlighted current trends and open issues in privacy and data protection in MCC using the results of existing primary studies published from 2009 to 2019.
In this study, a systematic mapping study (SMS) was conducted with a set of six research questions. A total of 1711 studies published from 2009 to 2019 were obtained. Following a filtering process, a set of 74 primary studies were selected. As a result, the existing threats and attacks on data privacy and solutions to serve personal data were demonstrated. Also, the metrics and measures that are used to assess the current solutions for privacy in mobile cloud computing were aggregated. In addition, the current state-of-the-art of data privacy exercises used in the domain was identified. Moreover, the research type’s facets and the contribution type facets that are used in MCC were highlighted. Furthermore, the open research issues of privacy and data protection in MCC were demonstrated.
This result of this study shows that, for the current data privacy exercise in MCC, the number of investigations is increasing regarding the setup, cryptography, authentication, and accounts creation of data privacy exercise. Also, for data privacy threats and attacks in MCC, the results of this study show the need for research in eavesdropping attacks, internal attacks, improper security policies and practices in some locations, internal multi-layer attacks, inference attacks on user privacy, and data breach threats. In addition, our exploration shows that there are open research issues in encryption, authentication, security, trust, privacy, architectures, various attacks, energy consumption, and testing. Overall, this SMS highlighted the current state-of-the-art, and demonstrated open research issues which in turn allows us to understand the required research into privacy and data protection in MCC.
Finally, this study provides for researchers and practitioners the current state of research in the privacy and data protection in MCC, to help in implementing privacy and data protection in their applications or their investigations. In future work, we plan to conduct a survey to assess possible solutions for preserving privacy and protection in MCC.
Supporting information
S1 appendix, s1 checklist, funding statement.
The author(s) received no specific funding for this work.
Data Availability

- {{ service.text }}
Mobile Cloud Computing PhD Assistance and Guidance
Mobile Cloud Computing is a popular research field which is hybrid of two fields. PhD assistance and guidance in this research field is given by our team for any work. This blog is to define you with some useful information in this field.
Our technical team is available 24/7 for research assistance
Send your techinical enquiries directly to our technical team via mail - [email protected] or you can send it to support team via WhatsApp
The blog of Mobile Cloud Computing PhD Assistance and Guidance starts with the explanation of mobile cloud computing and then gives a bulletin list of features in Mobile Cloud Computing. Then the main topics in this field is also given which will be useful for you and now we take you to this blog from here.
Mobile Cloud Computing
Mobile Cloud Computing is an integration system that joins cloud computing with mobile computing. The mobile users could access cloud for data processing and data storage. Smart mobile phone devices connect with a wireless service provider using wireless technology as WiFi, LTE and others. Then it links to the cloud service provider, in this way the mobile device creates a link with the cloud service provider. Here are the main features in this mobile cloud computing as below.
Features of Mobile Cloud Computing
- Enhancement in reliability while sharing data.
- Improves with application interfaces.
- Employs remote connectivity with the devices.
- Provisioning of high Quality of Service.
- Build faster responses for the submitted user requests.
Based on these features in mobile cloud computing there are many applications that use this research field. This field of MCC composes of two types as general-purpose computing and application-specific computing. The main concept of this field is to support mobile sensing, gaming, social networking and so on. Here are the main research topics in the field of mobile cloud computing.
Top 6 Topics in Mobile Cloud Computing
- Workload Sharing
- Resource Sharing and Allocation
- Cost Optimization and Dynamic Pricing
- Cooperative Task Scheduling
- Authentication and Trust Model
- Data Encryption and Decryption
The integration of mobile and cloud computing supports all the above list of topics. We have experts in this field to give PhD assistance and guidance from the start of your PhD till the completion of it.
We will be at the moment when you need help. You can get assistance from us for all PhD works as proposal writing, implementation, paper writing and thesis writing too. Just ping us through mail and be relaxed about your PhD. We make sure that, we also be confidential with your concept and personal information.
Did you find it helpful ?
Leave a reply.

Free Base papers and Topics for your Research
PhD services using Research Domain with important areas
Cloud Computing with Blockchain technology for Security in PhD

Image Processing Integrates with Blockchain Technology for Security

Security by Blockchain and Proof of Blocks for PhD Thesis Writing
PHD RESEARCH TOPIC IN MOBILE CLOUD COMPUTING
PHD RESEARCH TOPIC IN MOBILE CLOUD COMPUTING has many recent application in major fields. Mobile cloud computing is an integration of two leading domains namely cloud computing and Mobile computing. Mobile cloud computing is a recent trend which allows the data storage and also processing at the centralized computing platform present also in the cloud.
Cloud-Computing
This can access also by Mobile users using wireless technology. Cloud computing provides infrastructure support, software and also many other resources at low cost and also on demand fashion to the mobile users. It also makes it more energy and cost efficient solution . Today the major concern of mobile users is also Power consumption which can also solve using this platform.
Major PHD RESEARCH TOPIC IN MOBILE CLOUD COMPUTING includes Mobile power conservation, also Mobile security issues, Mobile virtualization and quality of Service. It has also a wide scope in the fields like cloud based M-learning, M commerce, Mobile games, also Mobile healthcare and assistive technology. It has made the mobile technology more advanced as all the major works are also possible through Mobile gadgets.
In the field of healthcare, patient can also communicate to the doctor from anywhere throughout the world. It has also made the life of people more sophisticated which is the reason behind its fast development. It will also have a constant growth and for those who are also trying to pursue Phd in Mobile computing can also refer PhD research cloud computing given below
RESEARCH ISSUES IN MOBILE-CLOUD-COMPUTING:
Mobile Communication Congestion Issues Context-Awareness Trust, security and also privacy Energy Efficient Transmission Live VM-Migration also in Issues Cloud Service Pricing Computation Offloading Task-Oriented also in Mobile Services Mobile Data also as a Service Mobile-Computing also as a Service Mobile Multimedia also as a Service Elasticity and also Scalability Network Access also Management Quality of Service Service Convergence Cloud Integration Mobile Learning Mobile-Healthcare Mobile Gaming Mobile-Commerce
softwares & Tools ——————————
1)AWS Mobile Hub 2)Agile tools 3)Cloud9 4)Codeanywhere 5)Icenium 6)Codebox 7)Kony Studio’s
Softwares & Tools Description ————————————————–
AWS Mobile Hub–> builds mobile apps also on AWS,AWS Mobile
Agile tools –> facilitate experimentation and also adaptation nature of mobile apps.
Cloud9–>cloud-based IDE which supports development also in 23 different programming languages, including HTML, CSS, PHP, Python, also Ruby etc
Codeanywhere–>runs also on all major web browsers.
Icenium–> cross-platform cloud-based IDE also used to develop mobile applications also for Android and iOS devices using HTML5, CSS and JavaScript.
Codebox–>Creates a Mobile Development Box also in 30 seconds.
Kony Studio’s–> used to create no-compromise native, web, and also hybrid apps for phones, tablets, desktops etc.
Related Search Terms
MOBILE CLOUD COMPUTING research issues, MOBILE CLOUD COMPUTING research topics, phd projects in MOBILE CLOUD COMPUTING, Research issues in MOBILE CLOUD COMPUTING
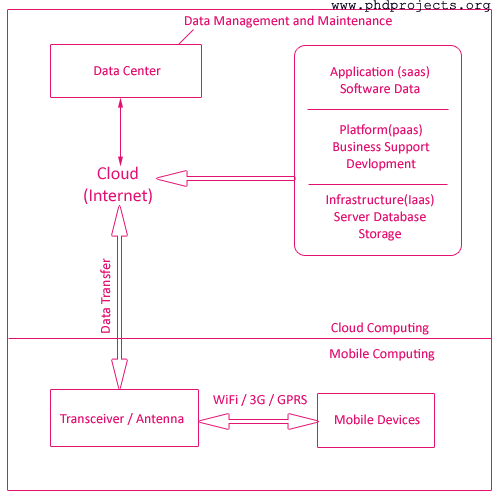
The Cloud Computing market its an all-time high with the current market size at USD 371.4 billion and is expected to grow up to USD 832.1 billion by 2025! It’s quickly evolving and gradually realizing its business value along with attracting more and more researchers, scholars, computer scientists, and practitioners. Cloud computing is not a single topic but a composition of various techniques which together constitute the cloud. Below are 10 the most demanded research topics in the field of cloud computing:
1. Big Data
Big data refers to the large amounts of data produced by various programs in a very short duration of time. It is quite cumbersome to store such huge and voluminous amounts of data in company-run data centers. Also, gaining insights from this data becomes a tedious task and takes a lot of time to run and provide results, therefore cloud is the best option. All the data can be pushed onto the cloud without the need for physical storage devices that are to be managed and secured. Also, some popular public clouds provide comprehensive big data platforms to turn data into actionable insights.
DevOps is an amalgamation of two terms, Development and Operations. It has led to Continuous Delivery, Integration, and Deployment and therefore reducing boundaries between the development team and the operations team. Heavy applications and software need elaborate and complex tech stacks that demand extensive labor to develop and configure which can easily be eliminated by cloud computing. It offers a wide range of tools and technologies to build, test, and deploy applications with a few minutes and a single click. They can be customized as per the client requirements and can be discarded when not in use hence making the process seamless and cost-efficient for development teams.
3. Cloud Cryptography
Data in the cloud is needed to be protected and secured from foreign attacks and breaches. To accomplish this, cryptography in the cloud is a widely used technique to secure data present in the cloud. It allows users and clients to easily and reliably access the shared cloud services since all the data is secured using either the encryption techniques or by using the concept of the private key. It can make the plain text unreadable and limits the view of the data being transferred. Best cloud cryptographic security techniques are the ones that do not compromise the speed of data transfer and provide security without delaying the exchange of sensitive data.
4. Cloud Load Balancing
It refers to splitting and distributing the incoming load to the server from various sources. It permits companies and organizations to govern and supervise workload demands or application demands by redistributing, reallocating, and administering resources between different computers, networks, or servers. Cloud load balancing encompasses holding the circulation of traffic and demands that exist over the Internet. This reduces the problem of sudden outages, results in an improvement in overall performance, has rare chances of server crashes, and also provides an advanced level of security. Cloud-based servers farms can accomplish more precise scalability and accessibility using the server load balancing mechanism. Due to this, the workload demands can be easily distributed and controlled.
5. Mobile Cloud Computing
It is a mixture of cloud computing, mobile computing, and wireless network to provide services such as seamless and abundant computational resources to mobile users, network operators, and cloud computing professionals. The handheld device is the console and all the processing and data storage takes place outside the physical mobile device. Some advantages of using mobile cloud computing are that there is no need for costly hardware, battery life is longer, extended data storage capacity and processing power improved synchronization of data and high availability due to “store in one place, accessible from anywhere”. The integration and security aspects are taken care of by the backend that enables support to an abundance of access methods.
6. Green Cloud Computing
The major challenge in the cloud is the utilization of energy-efficient and hence develop economically friendly cloud computing solutions. Data centers that include servers, cables, air conditioners, networks, etc. in large numbers consume a lot of power and release enormous quantities of Carbon Dioxide in the atmosphere. Green Cloud Computing focuses on making virtual data centers and servers to be more environmentally friendly and energy-efficient. Cloud resources often consume so much power and energy leading to a shortage of energy and affecting the global climate. Green cloud computing provides solutions to make such resources more energy efficient and to reduce operational costs. This pivots on power management, virtualization of servers and data centers, recycling vast e-waste, and environmental sustainability.
7. Edge Computing
It is the advancement and a much more efficient form of Cloud computing with the idea that the data is processed nearer to the source. Edge Computing states that all of the computation will be carried out at the edge of the network itself rather than on a centrally managed platform or the data warehouses. Edge computing distributes various data processing techniques and mechanisms across different positions. This makes the data deliverable to the nearest node and the processing at the edge. This also increases the security of the data since it is closer to the source and eliminates late response time and latency without affecting productivity.
8. Containerization
Containerization in cloud computing is a procedure to obtain operating system virtualization. The user can work with a program and its dependencies utilizing remote resource procedures. The container in cloud computing is used to construct blocks, which aid in producing operational effectiveness, version control, developer productivity, and environmental stability. The infrastructure is upgraded since it provides additional control over the granular activities over the resources. The usage of containers in online services assists storage with cloud computing data security, elasticity, and availability. Containers provide certain advantages such as a steady runtime environment, the ability to run virtually anywhere, and the low overhead compared to virtual machines.
9. Cloud Deployment Model
There are four main cloud deployment models namely public cloud, private cloud, hybrid cloud, and community cloud. Each deployment model is defined as per the location of the infrastructure. The public cloud allows systems and services to be easily accessible to the general public. Public cloud could also be less reliable since it is open to everyone e.g. Email. A private cloud allows systems and services to be accessible inside an organization with no access to outsiders. It offers better security due to its access restrictions. Hybrid cloud is a mixture of private and public clouds with the critical activities being performed using private cloud and non-critical activities being performed using the public cloud. Community cloud allows system and services to be accessible by a group of an organization.
10. Cloud Security
Since the number of companies and organizations using cloud computing is increasing at a rapid rate, the security of the cloud is a major concern. Cloud computing security detects and addresses every physical and logical security issue that comes across all the varied service models of code, platform, and infrastructure. It collectively addresses these services, however, these services are delivered in units, that is, the public, private, or hybrid delivery model. Security in the cloud protects the data from any leakage or outflow, theft, calamity, and removal. With the help of tokenization, Virtual Private Networks, and firewalls data can be secured.
Please Login to comment...
Similar reads.

- Cloud-Computing
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

Latest Research Topics on Cloud Computing (2022 Updated)
Cloud computing is now a vital online technology that is used worldwide. The market size of cloud computing is expected to reach $832.1 billion by 2025 . Its demand will always increase in the future, and there are many major reasons behind it. It has acquired popularity because it is less expensive for companies rather than setting up their on-site server implementations.
In this article, we’ve covered the top 14 in-demand research topics on cloud computing that you need to know.
📌 These cloud Computing research topics are:
- Green cloud computing
- Edge computing
- Cloud cryptography
- Load balancing
- Cloud analytics
- Cloud scalability
- Mobile cloud computing
- Cloud deployment model
- Cloud security
- Cloud computing platforms
- Cloud service model
- Containerization
Top 14 Cloud Computing Research Topics For 2022
1. green cloud computing.
Due to rapid growth and demand for cloud, the energy consumption in data centers is increasing. Green Cloud Computing is used to minimize energy consumption and helps to achieve efficient processing and reduce the generation of E-waste.
It is also called GREEN IT. The goal is to go paperless and decrease the carbon footprint in the environment due to remote working.
Power management, virtualization, sustainability, and environmental recycling will all be handled by green cloud computing.
2. Edge Computing
A rapidly growing field where the data is processed at the network’s edge instead of being processed in a data warehouse is known as edge computing. The real-time computing capacity is driving the development of edge-computing platforms. The data is processed from the device itself to the point of origin without relying on a central location which also helps to increase the system’s security. It gives certain benefits such as cost-effectiveness, powerful performance, and new functionality which wasn’t previously available.
Some innovations are made with the help of cloud computing by increasing the ability of network edge capabilities and expanding wireless connections.
3. Cloud Cryptography
Cloud Cryptography is a strong layer of protection through codes that helps to give security to the cloud storage and breach of the data. It saves sensitive data content without delaying the transmission of information. It can turn plain text into unreadable code with the help of computers and algorithms and restrict the view of data being delivered.
The clients can use the cryptographic keys only to access this data. The user’s information is kept private, which results in fewer chances of cybercrime from the hackers.
4. Load Balancing
The workload distribution over the server for soft computing is called load balancing. It helps distribute resources over multiple PCs, networks, and servers and allows businesses to manage workloads and application needs. Due to the rapid increase in traffic over the Internet, the server gets overloaded—two ways to solve the problem of overload of the servers: single-server and multiple-server solutions.
Keeping the system stable, boosting the system’s efficiency, and avoiding system failures are some reasons to use load balancing. It can be balanced by using software-based and hardware-based load balancers.
5. Cloud Analytics
Cloud analytics is a set of societal and analytical tools that analyze data on a private or public cloud to reduce data storage costs and management. It is specially designed to help clients get information from massive data. It is widely used in industrial applications such as genomics research, oil and gas exploration, business intelligence, security, and the Internet of Things (IoT).
It can help any industry improve its organizational performance and drive new value from its data. It is delivered through various models: public, private, hybrid, and community models.
6. Cloud Scalability
Cloud scalability refers to the capacity to scale up or down IT resources as per the need for change in computing. Scalability is usually used to fulfill the static needs where the workload is handled linearly when resource deployment is persistent.
The types of scalability are vertical, horizontal, and diagonal. Horizontal scaling is regarded as a long-term advantage; on the other hand, vertical scaling is considered a short-term advantage. The benefits of cloud scalability are reliability, cost-effectiveness, ease, and speed. It is critical to understand how much those changes will cost and how they will benefit the company.
It can be applied to Disk I/O, Memory, Network I/O, and CPU.
7. Mobile Cloud Computing
Mobile cloud computing helps to deliver applications to mobile devices through cloud computing. It allows different devices with different operating systems to have operating systems, computing tasks, and data storage. Mobile cloud helps speed and flexibility, resource sharing, and integrated data. Mobile Cloud Computing advantages are:
- Increased battery life
- Improvement in reliability and scalability
- Simple Integration
- Low cost and data storage capacity
- Processing power improvement
The only drawback is that the bandwidth and variability are limited. It has been chosen due to productivity and demand, increasing connectivity.
8. Big Data
Big data is a technology generated by large network-based systems with massive amounts of data produced by different sources. The data get classified through structured (organized data) and unstructured (unorganized data), and semi-structured forms. The data are analyzed through algorithms which may vary depending upon the data means. Its characteristics are Volume, Variety, Velocity, and Variability.
Organizations can make better decisions with the help of external intelligence, which includes improvements in customer service, evaluation of consumer feedback, and identification of any risks to the product/services.
9. Cloud Deployment Model
The way people use the cloud has evolved based on ownership, scalability, access, and the cloud’s nature and purpose. A cloud deployment model identifies a particular sort of cloud environment that determines the cloud infrastructure’s appearance.
Cloud computing deployment models are classified according to their geographical location. Deployment methods are available in public, private, hybrid, community, and multi-cloud models.
It depends on the firms to choose as per their requirements as each model has its unique value and contribution.
10. Cloud Security
Cloud security brings the revolution to the current business model through shifts in information technology. With the rapid increase in the number of cloud computing, the organization needs the security of the cloud, which has become a significant concern.
Cloud Security protects the data from any leakage or outflow, with the removal of theft and catastrophe. The cloud has public, private, and hybrid clouds for security purposes.
Cloud security is needed to secure clients’ data, such as secret design documents and financial records. Its benefits are lower costs, reduced ongoing operational and administrative expenses, increased data reliability and availability, and reduced administration.
11. Cloud Computing Platforms
In an Internet-based data center, a server’s operating system and hardware are referred to as a cloud platform. Cloud platforms work when a firm rents to access computer services, such as servers, databases, storage, analytics, networking, software, and intelligence. So the companies don’t have to set up their data centers or computing infrastructure; they need to pay for what they use. It is a very vast platform where we can do many types of research.
12. Cloud Service Model
The use of networks hosted on the Internet to store from remote servers used in managing and processing data, rather than from a local server or a personal computer. It has three models namely Infrastructure-as-a-Service (IaaS), Software-as-a-Service (SaaS),and Platform-as-a-Service (PaaS).Each type of cloud computing service provides different control, flexibility, and management levels to choose the right services for your requirements.
The ability to deliver applications and services increases an organization’s ability to evolve and improve products faster. This model helps the firms have their benefits more quickly and better than traditional software. In the DevOps approach, development and operations teams are integrated into a single unit, enabling them to develop diverse skills that aren’t limited to a particular task. The benefits of DevOps are rapidity, increase in frequency, reliability, scale, improved collaboration, and security.
It provides a wide range of tools and technologies to meet clients’ needs.
14. Containerization
Containerization is a popular software development technique that is rapidly evolving and can be used in addition to virtualization. It includes packaging software code and all of its components so that it may run consistently and uniformly across any infrastructure. The developers and operational teams see its benefit as it helps create and locate applications quickly and more securely. It benefits developers and development groups as it provides flexibility/ portability, the ability to move swiftly and efficiently, speed, fault isolation, efficiency, easily manageable, and security.
Final Words
Hence, all the above are new technologies of cloud computing developed to benefit users worldwide. But there are some challenges that need to be overcome. People nowadays have become skeptical about whether their data is private, secure, or not. This research can make this security more advanced and help to provide innovations in cloud computing.
We hope this article helps you to know some best research topics on cloud computing and how they’re changing the world.
10Pie Editorial Team is a team of certified technical content writers and editors with experience in the technology field combined with expert insights . Learn more about our editorial process to ensure the quality and accuracy of the content published on our website.

10Pie is your go-to resource hub to start and grow your Tech Career.
Send us your queries at [email protected]
CAREER GUIDES
- Data Science
- Cyber Security
- Cloud Computing
- Artificial Intelligence
- Business Intelligence
- Contributors
- Tech Glossary
- Editorial Policy
- Tech Companies
- Privacy policy
📈 Tech career paths
- AI career paths
- Python career paths
- DevOps career paths
- Data engineer career paths
- Data science career paths
- Software testing career paths
- Software engineer career paths
🏆 Tech courses
- Cloud computing courses in Pune
- Data analytics courses in Hyderabad
- Data science courses in Mangalore
- Cloud computing courses in Hyderabad
- Data analytics courses in Indore
- Data analytics courses in Mumbai
- Data analytics courses in Pune
📌 Featured articles
- AI seminar topics
- Which tech career is right for me?
- Will AI replace software engineers?
- Top data annotation companies
- Cyber security career roadmap
- How Tesla uses Artificial Intelligence
- Cloud computing seminar topics
© 2023 All rights reserved. All content is copyrighted, republication is prohibited.
- Our Promise
- Our Achievements
- Our Mission
- Proposal Writing
- System Development
- Paper Writing
- Paper Publish
- Synopsis Writing
- Thesis Writing
- Assignments
- Survey Paper
- Conference Paper
- Journal Paper
- Empirical Paper
- Journal Support

Latest Cloud Computing PhD Topics
Cloud computing is a technology of buying or selling resources, applications, software, and storage services from service providers. Also, the cloud can supply the required computing service regardless of end-user system setup and locality. This article is deal with highly demanding Cloud Computing PhD Topics with its future research developments.
In the cloud storage, the automated multimedia information is stored in the centralized pools which are collectively called the “Cloud”. In general, the physical storage extends into many servers (may be located in different places) and is maintained in it. But, cloud storage, takes complete responsibility for physical to environmental management. And, the authorized user can also easily access and avail of the services anywhere and anytime.
What is the Best Cloud Storage?
- Ensure the maximum fault tolerance by data supply and redundancy
- Ultimately consistent relating to data duplications
- By means of versioned copies, assure the increased durability
- Though cloud is furnished with an inclusive set of distributed resources, it acts as either cooperative cloud or federated cloud design
The primary entities of cloud computing are classified into 3 categories which are given as follows. These entities are collectively formed together as a cloud computing architecture .
What are the Main Components of Cloud Computing?
- Back-end platforms – Storage and Servers
- Front-end platform – Mobile, Thin User, and Fat User
- Network – Intranet, Intercloud, and Internet
- Cloud-based Distribution – Service and Application
In the beginning, the resources are shared based on the physical wires. Now, it simply this process by substituting with cloud computing provisioning approach . Through this technique, we can easily share the services, platform, resources, applications, and infrastructure from any distant place through the internet.
For instance: let’s see real-time cloud storage for deployment and host purposes.
- Object Storage Software – Openstack Swift
- Distributed Storage System – VISION Cloud and OceanStore
- Object Storage Systems – Hitachi Content Platform, EMC ECS, and EMC Atmos
- Object Storage Services – Oracle Cloud Storage, MS Azure Storage, and Amazon S3
We have long-term experienced research teams who are passionate to provide a nonstop unique good impact on the Cloud Computing research field. Certainly, our contribution springs out the new side of cloud computing’s practical and hypothetical work.
- Resource-Aware Service Composition
- Semantic Knowledge Engineering Analysis
- Data Security Challenges and Solutions
- Cloud Scalability and Interoperability
- Integration of Cloud Computing with Big data
- Small and Middle-Sized Business Intelligence
- Advanced Computational and Artificial Intelligence
- Computational Learning and Thinking Analysis
- Cloud-based Soft computing Models and Applications
- Modern Cloud-based Manufacturing Applications
- Remote Industrial Control and Monitoring Systems
- Internet Production Technology and Services
- Software Engineering and Development Strategies
- Cooperative and Distributed Computing for Embedded System
In recent times, hybrid technologies are followed to enhance the scheduling process. For instance: Incorporating the heuristic algorithms with deep learning techniques will yield effective results in scheduling performance . Further, nature-inspired algorithms can also include increasing the robustness of this method. In the future, these hybridization techniques are expected to employ single or multiple objective task scheduling.
- Higher degree of flexibility/scalability which is more suits for corporate
- Comprises more options for data placement and deployment
- Minimized operational costs
- Supports data distribution
- Inclusive cloud infrastructure with minimum cost and downtime
- Modernize the company’s internal process through personalized characteristics
- For instance: life sciences, healthcare sector, financial banking, and more
- Numerous companies are currently using Private cloud systems
- Custom-made data processing approach make the business process more efficient
- Main Characteristics: Self-Service and Scalability
- It can combine two or more cloud systems into one to form the hybrid cloud technique
- For instance: Integrate third-part cloud with public cloud and private cloud
- Suits for companies preferring standalone cloud storage (database)
- Segment the single platform into multiple servers based on data nature and orientation
- Integrate the multi-clouds to improve the functionalities that avoid unnecessary data load
Further, if you want to know more about Cloud Computing PhD Topics, then communicate with us. We will provide you with end-to-end research and development support at your needy time. We are here to direct you in the right direction from the initial step of research till the PhD degree holding step. For your knowledge, we have listed the points which we follow in the research phase.
How to start the research in Cloud Computing?
- Initially, figure out your desired research topic in cloud computing.
- For that, gather the current research areas in cloud computing and find out your interested area
- Next, go through at least 120+ research papers which is related to your handpicked area
- After that, perform a thorough literature survey and create a summary of your novel topic
- Then, confirm with your dataset and methodologies to be used for solving your research problem
- Finally, prepare the research proposal and implementation plan for your topic
Next in the development phase, the first step to carry out is choosing the appropriate tools and technologies which sure to yield accurate results at the end of execution. Below, we have bulletined some widely used languages for the cloud computing field .
Programming Languages for Cloud Computing
- Yacc and Lex
- Perl and Java
- Clojure and Scala
- JavaScript and Shell script
In addition, we also have given you the deep learning approaches followed by Meta-heuristic Algorithms that boost up the performance of the Cloud computing projects . Based on our experience, we found out these entire algorithms play a key role in simplifying and enhancing cloud system operations.
Deep Learning Models for Cloud Computing Projects
The below specified Meta-heuristic Algorithms help you to improve the optimization of the proposed solutions for solving your selected research problem. And, these are classified under three categories: Evolutionary Algorithms, Physics-based Algorithms, and Swarm-based Algorithms.
Meta-heuristic Algorithms for Cloud Computing
- Evolution Approaches
- Probability Learning
- Biogeography Based Optimizer (BBO)
- Genetic Programming and Algorithm
- Black Hole (BH) Algorithm
- Light Ray Optimization Algorithm
- Central Force Optimization (CFO)
- Charged System Search (CSS)
- Curved Space Optimization (CSO)
- Gravitational Search Algorithm (GSA)
- Simulated Annealing (SA)
- Galaxy based Search Algorithm (GbSA)
- Hybrid Artificial Chemical Reaction (HACR)
- Big-Bang Big-Crunch (BB-BB) Optimization
- Mouth Brooding Fish
- Dolphin Swarm / Partner Optimization
- Dragonfly Algorithm
- Henry Gas Solubility Optimization (HGSO)
- Wasp Swarm Algorithm
- Particle Swarm Optimization (PSO)
- Grasshopper Optimization Algorithm (GOA)
- Honey Bee Optimization (HBO)
- Hetznet Cloud
Once the development process is completed, then it is essential to evaluate the overall performance of the system to prove that your proposed work is better than the existing work. We guide you to choose an interesting novel cloud computing PhD topics. So, we have given some important performance parameters that are used in cloud computing systems
Performance Metrics for Cloud Computing
- Finish Time
- Size of Key
- Response Time
- Link Encryption
- Times Response Time
- Throughput Time
- Key Encryption
- Authentication Time
- Task Completion Time
- Time of Task
- Average Run Time
- Cost of Communication
- Actual Computation Cost
- Advanced Encryption Standard
Furthermore, if you are seeking innovative Cloud Computing PhD Topics, then communicate with us. We are ready to share our newly handpicked research ideas with you.
MILESTONE 1: Research Proposal
Finalize journal (indexing).
Before sit down to research proposal writing, we need to decide exact journals. For e.g. SCI, SCI-E, ISI, SCOPUS.
Research Subject Selection
As a doctoral student, subject selection is a big problem. Phdservices.org has the team of world class experts who experience in assisting all subjects. When you decide to work in networking, we assign our experts in your specific area for assistance.
Research Topic Selection
We helping you with right and perfect topic selection, which sound interesting to the other fellows of your committee. For e.g. if your interest in networking, the research topic is VANET / MANET / any other
Literature Survey Writing
To ensure the novelty of research, we find research gaps in 50+ latest benchmark papers (IEEE, Springer, Elsevier, MDPI, Hindawi, etc.)
Case Study Writing
After literature survey, we get the main issue/problem that your research topic will aim to resolve and elegant writing support to identify relevance of the issue.
Problem Statement
Based on the research gaps finding and importance of your research, we conclude the appropriate and specific problem statement.
Writing Research Proposal
Writing a good research proposal has need of lot of time. We only span a few to cover all major aspects (reference papers collection, deficiency finding, drawing system architecture, highlights novelty)
MILESTONE 2: System Development
Fix implementation plan.
We prepare a clear project implementation plan that narrates your proposal in step-by step and it contains Software and OS specification. We recommend you very suitable tools/software that fit for your concept.
Tools/Plan Approval
We get the approval for implementation tool, software, programing language and finally implementation plan to start development process.
Pseudocode Description
Our source code is original since we write the code after pseudocodes, algorithm writing and mathematical equation derivations.
Develop Proposal Idea
We implement our novel idea in step-by-step process that given in implementation plan. We can help scholars in implementation.
Comparison/Experiments
We perform the comparison between proposed and existing schemes in both quantitative and qualitative manner since it is most crucial part of any journal paper.
Graphs, Results, Analysis Table
We evaluate and analyze the project results by plotting graphs, numerical results computation, and broader discussion of quantitative results in table.
Project Deliverables
For every project order, we deliver the following: reference papers, source codes screenshots, project video, installation and running procedures.
MILESTONE 3: Paper Writing
Choosing right format.
We intend to write a paper in customized layout. If you are interesting in any specific journal, we ready to support you. Otherwise we prepare in IEEE transaction level.
Collecting Reliable Resources
Before paper writing, we collect reliable resources such as 50+ journal papers, magazines, news, encyclopedia (books), benchmark datasets, and online resources.
Writing Rough Draft
We create an outline of a paper at first and then writing under each heading and sub-headings. It consists of novel idea and resources
Proofreading & Formatting
We must proofread and formatting a paper to fix typesetting errors, and avoiding misspelled words, misplaced punctuation marks, and so on
Native English Writing
We check the communication of a paper by rewriting with native English writers who accomplish their English literature in University of Oxford.
Scrutinizing Paper Quality
We examine the paper quality by top-experts who can easily fix the issues in journal paper writing and also confirm the level of journal paper (SCI, Scopus or Normal).
Plagiarism Checking
We at phdservices.org is 100% guarantee for original journal paper writing. We never use previously published works.
MILESTONE 4: Paper Publication
Finding apt journal.
We play crucial role in this step since this is very important for scholar’s future. Our experts will help you in choosing high Impact Factor (SJR) journals for publishing.
Lay Paper to Submit
We organize your paper for journal submission, which covers the preparation of Authors Biography, Cover Letter, Highlights of Novelty, and Suggested Reviewers.
Paper Submission
We upload paper with submit all prerequisites that are required in journal. We completely remove frustration in paper publishing.
Paper Status Tracking
We track your paper status and answering the questions raise before review process and also we giving you frequent updates for your paper received from journal.
Revising Paper Precisely
When we receive decision for revising paper, we get ready to prepare the point-point response to address all reviewers query and resubmit it to catch final acceptance.
Get Accept & e-Proofing
We receive final mail for acceptance confirmation letter and editors send e-proofing and licensing to ensure the originality.
Publishing Paper
Paper published in online and we inform you with paper title, authors information, journal name volume, issue number, page number, and DOI link
MILESTONE 5: Thesis Writing
Identifying university format.
We pay special attention for your thesis writing and our 100+ thesis writers are proficient and clear in writing thesis for all university formats.
Gathering Adequate Resources
We collect primary and adequate resources for writing well-structured thesis using published research articles, 150+ reputed reference papers, writing plan, and so on.
Writing Thesis (Preliminary)
We write thesis in chapter-by-chapter without any empirical mistakes and we completely provide plagiarism-free thesis.
Skimming & Reading
Skimming involve reading the thesis and looking abstract, conclusions, sections, & sub-sections, paragraphs, sentences & words and writing thesis chorological order of papers.
Fixing Crosscutting Issues
This step is tricky when write thesis by amateurs. Proofreading and formatting is made by our world class thesis writers who avoid verbose, and brainstorming for significant writing.
Organize Thesis Chapters
We organize thesis chapters by completing the following: elaborate chapter, structuring chapters, flow of writing, citations correction, etc.
Writing Thesis (Final Version)
We attention to details of importance of thesis contribution, well-illustrated literature review, sharp and broad results and discussion and relevant applications study.
How PhDservices.org deal with significant issues ?
1. novel ideas.
Novelty is essential for a PhD degree. Our experts are bringing quality of being novel ideas in the particular research area. It can be only determined by after thorough literature search (state-of-the-art works published in IEEE, Springer, Elsevier, ACM, ScienceDirect, Inderscience, and so on). SCI and SCOPUS journals reviewers and editors will always demand “Novelty” for each publishing work. Our experts have in-depth knowledge in all major and sub-research fields to introduce New Methods and Ideas. MAKING NOVEL IDEAS IS THE ONLY WAY OF WINNING PHD.
2. Plagiarism-Free
To improve the quality and originality of works, we are strictly avoiding plagiarism since plagiarism is not allowed and acceptable for any type journals (SCI, SCI-E, or Scopus) in editorial and reviewer point of view. We have software named as “Anti-Plagiarism Software” that examines the similarity score for documents with good accuracy. We consist of various plagiarism tools like Viper, Turnitin, Students and scholars can get your work in Zero Tolerance to Plagiarism. DONT WORRY ABOUT PHD, WE WILL TAKE CARE OF EVERYTHING.
3. Confidential Info
We intended to keep your personal and technical information in secret and it is a basic worry for all scholars.
- Technical Info: We never share your technical details to any other scholar since we know the importance of time and resources that are giving us by scholars.
- Personal Info: We restricted to access scholars personal details by our experts. Our organization leading team will have your basic and necessary info for scholars.
CONFIDENTIALITY AND PRIVACY OF INFORMATION HELD IS OF VITAL IMPORTANCE AT PHDSERVICES.ORG. WE HONEST FOR ALL CUSTOMERS.
4. Publication
Most of the PhD consultancy services will end their services in Paper Writing, but our PhDservices.org is different from others by giving guarantee for both paper writing and publication in reputed journals. With our 18+ year of experience in delivering PhD services, we meet all requirements of journals (reviewers, editors, and editor-in-chief) for rapid publications. From the beginning of paper writing, we lay our smart works. PUBLICATION IS A ROOT FOR PHD DEGREE. WE LIKE A FRUIT FOR GIVING SWEET FEELING FOR ALL SCHOLARS.
5. No Duplication
After completion of your work, it does not available in our library i.e. we erased after completion of your PhD work so we avoid of giving duplicate contents for scholars. This step makes our experts to bringing new ideas, applications, methodologies and algorithms. Our work is more standard, quality and universal. Everything we make it as a new for all scholars. INNOVATION IS THE ABILITY TO SEE THE ORIGINALITY. EXPLORATION IS OUR ENGINE THAT DRIVES INNOVATION SO LET’S ALL GO EXPLORING.
Client Reviews
I ordered a research proposal in the research area of Wireless Communications and it was as very good as I can catch it.
I had wishes to complete implementation using latest software/tools and I had no idea of where to order it. My friend suggested this place and it delivers what I expect.
It really good platform to get all PhD services and I have used it many times because of reasonable price, best customer services, and high quality.
My colleague recommended this service to me and I’m delighted their services. They guide me a lot and given worthy contents for my research paper.
I’m never disappointed at any kind of service. Till I’m work with professional writers and getting lot of opportunities.
- Christopher
Once I am entered this organization I was just felt relax because lots of my colleagues and family relations were suggested to use this service and I received best thesis writing.
I recommend phdservices.org. They have professional writers for all type of writing (proposal, paper, thesis, assignment) support at affordable price.
You guys did a great job saved more money and time. I will keep working with you and I recommend to others also.
These experts are fast, knowledgeable, and dedicated to work under a short deadline. I had get good conference paper in short span.
Guys! You are the great and real experts for paper writing since it exactly matches with my demand. I will approach again.
I am fully satisfied with thesis writing. Thank you for your faultless service and soon I come back again.
Trusted customer service that you offer for me. I don’t have any cons to say.
I was at the edge of my doctorate graduation since my thesis is totally unconnected chapters. You people did a magic and I get my complete thesis!!!
- Abdul Mohammed
Good family environment with collaboration, and lot of hardworking team who actually share their knowledge by offering PhD Services.
I enjoyed huge when working with PhD services. I was asked several questions about my system development and I had wondered of smooth, dedication and caring.
I had not provided any specific requirements for my proposal work, but you guys are very awesome because I’m received proper proposal. Thank you!
- Bhanuprasad
I was read my entire research proposal and I liked concept suits for my research issues. Thank you so much for your efforts.
- Ghulam Nabi
I am extremely happy with your project development support and source codes are easily understanding and executed.
Hi!!! You guys supported me a lot. Thank you and I am 100% satisfied with publication service.
- Abhimanyu
I had found this as a wonderful platform for scholars so I highly recommend this service to all. I ordered thesis proposal and they covered everything. Thank you so much!!!
Related Pages

Home / Mobile Cloud Computing Projects
Mobile Cloud Computing Projects
Mobile Cloud Computing Projects is always preparing to succeed in the student’s project. Our cloud company is the best choice to receive your final year or PhD projects. With the wide range of scope in the cloud, we will assign our mentor team to find the current topics. From that, we come to know that the mobile cloud is a recent area. It will support for a huge collection of mobile services.
5G is a key technology that will act as an enabler between mobile and cloud computing. We will 5G in many mobile cloud computing projects in different aspects. In terms of evaluation, most of the students are choosing their mobile cloud computing project topic in this field.

Our Topics of Interest – 5G Mobile Cloud Computing Projects
- Cloud/Fog in 5G Mobile Networks
- 5G V2X Communication in Cloud
- Big Data in 5G Mobile Cloud
- Security Concepts in IoT Cloud
- Mobile Cloud Native-RAN in 5G
- 5G Mobile Cloud Data Centers
- 5-G with Blockchain Technology
- 5G Mobile Edge Computing
- Smart-Building Automation
- Smart Industry Application
QoS and QoE Service Demands in 5G + Mobile Cloud
- Availability
- Packet Loss
- Heterogeneity
- Video Quality
- Error Indicator Count
- Service Provisioning
- Continuity Error
- Frame Loss Length
- Frame Loss Events
- Buffer Rate
Advanced Concepts in Mobile Cloud Computing
- Virtualization
- Hybrid Cloud Management
- Shift and Lift Cloud Apps
- HD Video Streaming
- Task Division and Allocation
- Web Analytics and Services
- QoS and QoE Improvement
- Cloud Cost Containment
- Augmented Execution for Smart Phones
Coding Supported Tools – Mobile Cloud Computing Projects
- OpenMobster
- Green Cloud
- Simulation Tools with Java
Our usually murmuring terms are quality and trust . Without these terms, we can’t train and serve you to your expectations. Similarly, we don’t set our goal to earn money. Instead, we will love to do your work with true accomplishment. Our past experience is the best lesson for us. The present skill is a gift for students, and the future is plan is to inspire them a lot. At short intervals, bring your mobile cloud computing projects .

Related Pages
Web Technology Projects
Mobile Cloud Computing Thesis
Cloud Computing Projects For Students
Project On Cloud Computing Final Year
Final Year Projects On Cloud Computing
Project On Cloud Computing Security
Cloud Computing Based Projects
Cloud Computing Mini Projects
Projects On Cloud Computing Security
Cloud Computing Projects In Java
Projects Related To Cloud Computing
Fog Computing Projects
Cloud Computing Project Titles
Cloud Computing Final Year Projects
Cloud Computing Open Source Projects
Key Services
- Literature Survey
- Research Proposal
- System Development
- AWS Integration
- Algorithm Writing
- Paper Writing
- Conference Paper
- Thesis Writing
- Dissertation Writing
- Assignments
Testimonials
I really appreciate your project development team. Since, your source codes are very easy to understand and execute it. Thank you!

You’re amazing and great working with you! I am totally satisfied with your paper writing. Keep up the best service for scholars!

Thank you so much for my project support and you guys are well done in project explanation. I get a clear vision about it.

You’ve been so helpful because my project is based on the AWS and HDFS integration. Before my commitment with you, I’ve a lot of fear, but you people rocked on my project.

Your project development is good and you made it so simple. Especially, codes are very new and running without any error.

You exactly did my project according to my demand. I tried many services, but I get the correct result from you. So surely I will keep working with you!


ICT: Cyber Security and Applications
Proceedings of ICTCS 2023, Volume 3
- Conference proceedings
- © 2024
- Amit Joshi 0 ,
- Mufti Mahmud 1 ,
- Roshan G. Ragel 2 ,
- S. Kartik 3
Global Knowledge Research Foundation, Ahmedabad, India
You can also search for this editor in PubMed Google Scholar
Nottingham Trent University, Nottingham, UK
University of peradeniya, delthota, sri lanka, department of cse, sns college of technology, coimbatore, india.
- Presents high-quality research in the field of information and communication technology
- Features the outcomes of ICTCS 2023, held in Jaipur, India
- Serves as a reference resource for researchers and practitioners in academia and industry
Part of the book series: Lecture Notes in Networks and Systems (LNNS, volume 916)
Included in the following conference series:
- ICTCS: International Conference on Information and Communication Technology for Competitive Strategies
Conference proceedings info: ICTCS 2022.
This is a preview of subscription content, log in via an institution to check access.
Access this book
- Available as EPUB and PDF
- Read on any device
- Instant download
- Own it forever
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Other ways to access
Licence this eBook for your library
Institutional subscriptions
Table of contents (40 papers)
Front matter, scalability analysis of molecular dynamics simulation using namd on ampere-based dense gpu supercomputer.
- Nisha Agrawal, Abhishek Das, Manish Modani
Digital Muhadathah : Framework Model Development for Digital Arabic Language Learning
- Aminudin Hehsan, Miftachul Huda, Mahsun Mahsun, Asrori Asrori, Muhammad Hambal Shafwan, Din Muhammad Zakariya et al.
Proficient Exam Monitoring System Using Deep Learning Techniques
- Priya N. Parkhi, Amna Patel, Dhruvraj Solanki, Himesh Ganwani, Manav Anandani
Object Detection in Rainy Images Based on Multi-stage Image Deraining Network
- V. S. Vishnu, Philomina Simon
ApnaMarket.NFT: Empowering Art and Collectibles in the NFT Marketplace
- Padma Adane, Viresh Dhawan, Harsh Singh, Atharva Baheti
Smart Homes of Tomorrow: IoT-Enabled Lifestyle Enhancements
- Priyanka Patel, Krishna Gevariya, Rency Kapadia
Human Activity Recognition Using Supervised Machine Learning Classifiers
- Kazi Azizuddin, Premal Patel, Chintan Shah
Application of Deep Learning in Detection and Classification
- P. K. Muhammad Suarim, Meeradevi, B. J. Sowmya, Prathik Boppudi, Vivek Ranjan, Yashraj Verma et al.
Gesture-Based Alphabet Detection and Scoring Using OpenCV and Tesseract-OCR
- Karan Chopra, S. Shanthi Therese
Sign-Kiosk: A Real-Time Virtual Assistant
- Srushti Sujit, Anchala Balaraj, M. S. Pavan Kumar, A. Sagar, M. Anuradha
A Graph-Based Strategy for Intrusion Detection in Connected Vehicles
- M. S. Sreelekshmi, S. Aji
Correlation Analysis Between INR-USD Exchange Rates and Public Sentiments Using Twitter
- Gargee Dorle, Varsha Pimprale
Improving Farm Yield Through Agent-Based Modelling
- Dattatraya Adane, Anand Upadhyaya, Mayank Pandey, Yash Dhoot
A Recommendation System for Food Tourism
- Dattatraya S. Adane, Himanshu Shahu, Parshva Choradia, Ritesh Yadav
Working of the Tesseract OCR on Different Fonts of Gujarati Language
- Kartik Joshi, Harshal Arolkar
Exploring Innovations for Streamlining Orphan Adoption: Harnessing Blockchain and Decentralized Solutions—A Survey and Comprehensive Framework
- Deepali Patil, Aabha Patil, Aarti Puthran, Nilesh Marathe, Surekha Janrao, Hezal Lopes
Encryption + Watermarking: A Duo Approach for Secure Image Communication in Transform Domain
- R. Sivaraman, D. Yasvanthira Sri, R. Subashini, B. Vinizia, C. Lakshmi
Animal Detection in Wildlife Conservation Using Deep Learning
- B. Senbagam, S. Bharathi
Real-Time Groundwater Monitoring Using IoT Sensors for Sustainable Resource Management
- M. Sowndharya, S. Duraisamy
Other volumes
Information and communication technology for competitive strategies (ictcs 2022).
- Information and Communication Technology
- Big Data and Data Mining
- Sensor Networks and Embedded System
- Human Computer Interaction
- E-governance
- ICTCS 2023 Proceedings
About this book
This book contains best selected research papers presented at ICTCS 2023: Eighth International Conference on Information and Communication Technology for Competitive Strategies. The conference will be held in Jaipur, India during 8 – 9 December 2023. The book covers state-of-the-art as well as emerging topics pertaining to ICT and effective strategies for its implementation for engineering and managerial applications. This book contains papers mainly focused on ICT for computation, algorithms and data analytics and IT security. The work is presented in three volumes.
Editors and Affiliations
Mufti Mahmud
Roshan G. Ragel
About the editors
Dr. Amit Joshi is currently the Director of Global Knowledge Research Foundation, also an Entrepreneur Researcher who has completed his Masters and research in the areas of cloud computing and cryptography in medical imaging. Dr. Joshi has an experience of around 10 years in academic and industry in prestigious organizations. Dr. Joshi is an active member of ACM, IEEE, CSI, AMIE, IACSIT-Singapore, IDES, ACEEE, NPA and many other professional societies. Currently, Dr. Joshi is the International Chair of InterYIT at International Federation of Information Processing (IFIP, Austria), He has presented and published more than 50 papers in national and international journals/conferences of IEEE and ACM. Dr. Joshi has also edited more than 40 books which are published by Springer, ACM and other reputed publishers. Dr. Joshi has also organized more than 50national and international conferences and programs in association withACM, Springer, IEEE to name a few across different countries including India, UK, Europe, USA, Canada, Thailand, Egypt and many more.
Dr. Mufti Mahmud is an Associate Professor of Cognitive Computing at the Computer Science Department of Nottingham Trent University (NTU), UK. He has been the recipient of the top 2% cited scientists worldwide in computer science (since 2020), the NTU VC Outstanding Research Award 2021, and the Marie-Curie postdoctoral fellowship. Dr Mahmud is a member of the university shadow executive team shadowing the pro-vice-chancellor (research and innovation), coordinator of the Computer Science and Informatics research excellence framework unit of assessment at NTU, the group leader of the cognitive computing & brain informatics research group and the deputy group leader of the Interactive Systems research group at NTU. His research portfolio consists of GBP 4.0 million grant capture with expertise that includes brain informatics, computational intelligence, applied data analysis, and big data technologies focusing on healthcare applications. In these fields, he has published over 320 peer-reviewed articles. Dr Mahmud has been the General Chair of the Brain Informatics Conference 2020, 2021, and 2022; founding chair of the Applied Intelligence and Informatics conference since 2021; Trends in Electronics and Health Informatics 2022; International Symposium of Green Technologies and Applications 2023; chair of the IEEE CICARE symposium since 2017 and was the local organising chair of the IEEE WCCI 2020. He will serve as one of the General Chairs of the 31st edition of the ICONIP conference to be held in Auckland (NZ) in 2024. He is the Big Data Analytics Section Editor of Cognitive Computation, the Regional Editor (Europe) of the Brain Informatics journal, and an Associate Editor of the Frontiers in Neuroscience. He is the chief editor of the Applied Intelligence and Informatics (Springer-Nature) and Smart Healthcare Systems: From Data to Knowledge (CRC Press) book series. Currently, Dr Mahmud is serving as the Chair of the Intelligent System Application and Brain Informatics Technical Committees of the IEEE Computational Intelligence Society (CIS), a member of the IEEE CIS Task Force on Intelligence Systems for Health, the Publications Chair of the IEEE UK and Ireland Industry Applications Chapter, and the Project Liaison Officer of the IEEE UK and Ireland SIGHT Committee, and the Secretary of the IEEE UK and Ireland CIS Chapter. Dr. Roshan Ragel is a full professor in Computer Engineering at the University of Peradeniya, Sri Lanka. He is a skilled university lecturer and researcher with a doctorate in computer science and engineering and a passion for teaching, research and administration. His research interest is in the areas of fault-tolerant and dependable computing, accelerated and high-performance computing, wearable computing and synthesis of secure and reliable embedded processors.Prof. Ragel received his PhD in Computer Science and Engineering from the University of New South Wales, Australia in 2007 and his BSc in Engineering from the University of Peradeniya, Sri Lanka in 2001. He was appointed a Senior Lecturer in Computer Engineering at the University of Peradeniya December 2007 and a full professor since October 2017. Prof. Ragel has co-authored about 150 peer-reviewed articles in topics including Micro- Architectural Support for Reliability and Security in Embedded Processors (SoC), Internet of Things (IoT), Side-Channel Attacks and Countermeasures, Application Specific Processor Design, High-Performance Computing such as Hardware/Software Acceleration of Bioinformatics Algorithms, Wearable Computing, Format-Preserving Digitisation and OCR of Local Language Text, and Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHAs) in the Context of Mobile Applications. He has won several best paper awards in conference papers, the most prolific Sri Lankan author award from Elsevier Research in 2017 and the Presidential award for scientific publication in Sri Lanka in 2018. He was a visiting research scholar at the UNSW, Sydney a few times and UIUC, Illinois once. He is a Senior Member of the IEEE and the IEEE Computer Society.
Dr. S. Karthik is presently Professor & Dean in the Department of Computer Science & Engineering, SNS College of Technology, affiliated to Anna University- Chennai, Tamil Nadu, India. He received the M.E and PhD degree from Anna University, Chennai. His research interests include network security, big data, cloud computing, web services and wireless systems. In particular, he is currently working in a research group developing new Internet security architectures and active defence systems against DDoS attacks. Dr. S.Karthik published more than 200 papers in refereed international journals and 125 papers in conferences and has been involved in many international conferences as Technical Chair and tutorial presenter. He is an active member of IEEE, ISTE, IAENG, IACSIT and Indian Computer Society.
Bibliographic Information
Book Title : ICT: Cyber Security and Applications
Book Subtitle : Proceedings of ICTCS 2023, Volume 3
Editors : Amit Joshi, Mufti Mahmud, Roshan G. Ragel, S. Kartik
Series Title : Lecture Notes in Networks and Systems
DOI : https://doi.org/10.1007/978-981-97-0744-7
Publisher : Springer Singapore
eBook Packages : Engineering , Engineering (R0)
Copyright Information : The Editor(s) (if applicable) and The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd. 2024
Softcover ISBN : 978-981-97-0743-0 Published: 14 May 2024
eBook ISBN : 978-981-97-0744-7 Published: 13 May 2024
Series ISSN : 2367-3370
Series E-ISSN : 2367-3389
Edition Number : 1
Number of Pages : XX, 501
Number of Illustrations : 72 b/w illustrations, 189 illustrations in colour
Topics : Communications Engineering, Networks , Science and Technology Studies , Systems and Data Security , Computational Intelligence , Artificial Intelligence
- Publish with us
Policies and ethics
- Find a journal
- Track your research

Students design healthcare solutions for the underserved
By Isabella Bachman
The Biomedical Engineering Society , in collaboration with Bioengineering Technology & Entrepreneurship Center (BTEC) , hosted the second annual BTEC x BMES Design-A-Thon on May 4. The design challenged students to developing a product or service that will yield positive health outcomes for, and/or increase access, to healthcare technologies in underserved communities.
Throughout the academic year, student teams enter into an incubator where, under the guidance of BTEC faculty and graduate students, they develop a product or service, which is then presented to a panel of judges at the end of the year. Design-A-Thon equips students with the knowledge and skills to address societal challenges in the healthcare industry by enhancing diversity considerations within the design process.
Seven finalist student teams presented their projects. The two first-place teams, BreatheRight and Osto-Pop, received an award of $1,000, while the runner-up teams, BUzz Bracelet and Mobile Vision, received $500. Graduate student mentors Dev Bhatt (BME PhD’28) and Alex Howard (BME PhD’28) also received $100 for their advisory role.
The BreatheRight team was composed of three BME undergraduate students: Yash Patel, Nikita Vinay Kishan and Luca Pungan. The team created a device that attaches to most asthma inhalers to monitor medication intake and respiratory function. This information is sent to a smart phone app, which then records the data, providing useful information to patients and healthcare professionals. The device and monitoring application are expected to provide a critical tool for asthma management, especially to underrepresented groups which have higher incidences of asthma .
Two BME juniors, Ananya Pemaraj and Shadin Almaiman, were on the Osto-Pop team. They developed a low-cost device for elderly colectomy patients with less manual dexterity to better access their colostomy bag. It is also designed to reduce odor and gas.
Industry partners were notably pivotal to the success of this event. Merck Research Labs sponsored the prizes and sent several representatives to give a presentation on their biologics research program.
The panel of judges included: Professor of the Practice Diane Joseph-McCarthy (BME, Chem), executive director of BTEC; Associate Professor Michael Smith (BME, MSE); Research Assistant Professor Xiaojun Cheng (BME); Rohan Jadeja (MS’19) , Systems Engineering Group, KMC Systems, Inc.; and Lecturer Kavon Karrobi (BME), BTEC manager.
Related posts:
- First Design-A-Thon Generates Tech Solutions to Health Disparities
- Competition Sparks Sustainability Solutions
- MSE PhD candidate to advance healthcare
- Jenny Sun’s Mission to Reveal Mysteries in the Human Body and Improve Healthcare
Share this:
- Click to email this to a friend
- Click to share on LinkedIn
- Click to share on Twitter
- Share on Facebook
- Click to print
- Click to share on Reddit
- Click to Press This!
View all posts

5 Cool Cloud Computing Research Projects
5 Cool Cloud Computing Research Projects is our magnificent service that begins for you with our mastermind experts’ help. Our primary goal is to offer high tech cloud computing projects to finish your academic projects with high grades. We have world-class certified scientists and experts with us. Due to this reason, our admirable 5 cool cloud computing research projects service spread in this universe. Our students and research colleagues are utilizing our miraculous service from various countries in this entire world. Our experts concentrate on scholars individually to provide immeasurable guidance and assistance to make our scholar’s universal celebrated professionals. If you want to utilize our guidance, you can approach us online or offline.
Computing Research Projects
Our Research Projects offer highly innovative thoughts and novelty ideas for you to choose highly sophisticated cool cloud computing projects. Our knowledgeable groundbreaking experts have nearly implemented 5000+ cloud computing-based projects for you with our creative ideas. Cloud computing is a technology to deliver computing services (cloud providers), including software, networking, analytics, storage, server, database, etc. It provides distributed computer processing data and source to system and other parallel devices on demand. Now, we provide some of the advanced mechanisms in cool cloud computing.
Recent Research in Cool Cloud Computing
- Isolation, Protection and also compliance management for private, public and hybrid cloud
- Automatic business workflow and also process management in cloud
- Cloud-orchestration provisioning
- Cloud SLA (Service Level Agreement) and also quality management
- Self-service cloud dashboard, portal and also analytics
- Cloud Federation, composition, bursting and also bridging
- Cloud programming paradigms and also in models
- Green cloud computing
- Cloud migration
- Cloud workload deployment and also in profiling control
- Cloud-performance, configuration and capacity management
- Cloud software license and patch management
- Platform, infrastructure, application, social, business, and also in mobile clouds
- Business, economic and also in ROI models for cloud computing
Advanced Tools and Software’s for Cloud Computing
- Cisco Prime Cloud Automation
- Rundeck Runbook Automation
- AppCore Cloud Management
Purpose of tools and software’s
Enstratius: It is a CCIM (Cloud Computing Infrastructure Management) platform which provide single platform also for the utilization of multi / hybrid cloud service management
DivvyCloud: It is a cloud management platform also for managing event driven infrastructure and hybrid / multiple cloud footpath
Cisco Prime Cloud Automation: It is an automation tool also for developing and managing cloud service
Rundeck Runbook Automation: It is open source software to automate ad hoc and also in routine procedure
AtomSphere: It is a software platform
AppCore Cloud Management: It is a management and also in automation based software which is designed to simplify cloud environment through single monitoring interfaces and management
Sprinkle: It is a conditional software tool to build remote server
Qualys: It is a CIA (Cloud Infrastructure Automation) tool also for provide global scalability and automation in the cloud
Fabric: It is an automation and also command line tool for upload and downloads files
Juju: It is a cloud infrastructure automation tool which helps to build complete cloud environments using few commands
Our Cool Cloud Computing Research Projects
Wireless technologies and green computing for big data and cloud.
- Energy Efficient Communication, networking and also protocols
- Modeling and measuring energy consumption
- Green technologies and also in sustainable infrastructure design
- Protect distributed big data storage also in cloud computing using cryptograph approach
Data Offloading in Mobile Cloud Computing Environment
- Cloud computing techniques to provide high performance
- Battery life of SMD (Smart Mobile Device) can offload on cloud
- Shifting mechanism compute applications on server
- Validate application also for partition
- Offload applications on cloud
- Receive result on Smart Mobile Device
Big Data analytics for cloud, cognitive networks and IoT
- Parallel processing and also in computing architecture
- Computing cloud
- Mobile phones
- Revival artificial intelligence
- Widespread IoT (Internet of Things) deployment
- Broaden super computer applications
- Internet of Things (IoT) sensing
- Cognitive Computing
- Machine Learning
- Data Analytics
- Deep Learning
Mobile Cloud Computing in 5G
- Rapidly growing demand in mobility and high data rates
- Research enabled on 5G mobile networks
- Support applications and also service with thousands of network traffics today
- Complex and also in huge location aware dataset exceed spatial computing technology facility
- Mobile cloud technology (Combination of mobile and also in cloud computing)
Multiple Cloud Based Internet of Things (IoT) Applications using Energy Aware Composition Algorithm
- Motivation for IoT applications to control cloud’s unique characteristics
- Interconnect self configuration and also intelligent nodes
- Establish dynamic and also efficient platform for collaboration and communication
- IoT have virtual resources utilization infrastructure privilege
- Visualization platforms
- Storage devices
- Analytical tools
- Resource monitoring
- Client delivery
We offer a highly comfortable online service for our research fellows and students for 5 cool cloud computing research projects . Using our online service, our scholars can easily contact us for any kind of guidance or require a solution for a particular problem in research from anywhere. Our geniuses provide complete guidance, and also absolute solutions will reach immediately.
Related Pages
Services we offer.
Mathematical proof
Pseudo code
Conference Paper
Research Proposal
System Design
Literature Survey
Data Collection
Thesis Writing
Data Analysis
Rough Draft
Paper Collection
Code and Programs
Paper Writing
Course Work

IMAGES
VIDEO
COMMENTS
Ad Hoc Mobile Cloud Computing; IoT Enabled Mobile Cloud ; Mobile Edge also assisted UAV; We will assign our review team in each field for the final validation of your research work. As a result, we assure you 0% copy/paste and 100% unique content. PhD research topics in mobile cloud computing have teams of experts in each phase of your study to ...
Mobile cloud computing promises several benefits such as extra battery life and storage, scalability, and reliability. However, there are still challenges that must be addressed in order to enable the ubiquitous deployment and adoption of mobile cloud computing.Some of these challenges include security, privacy and trust, bandwidth and data transfer, data management and synchronization, energy ...
Table 1 summarizes recent research surveys on mobile cloud computing by highlighting their focus, explaining the components of the proposed architecture for mobile cloud computing (i.e., if the authors proposed an architecture), expressing their contributions, identifying the analysis technique used to determine research challenges for mobile cloud computing and present these challenges.
4. Blockchain data-based cloud data integrity protection mechanism. The "Blockchain data-based cloud data integrity protection mechanism" paper suggests a method for safeguarding the integrity of cloud data and which is one of the Cloud computing research topics. In order to store and process massive amounts of data, cloud computing has grown ...
Internet, Cloud Computing has become a significant research topic of the scientific and industrial communities since 2007. Commonly, cloud computing is described as a range of ser- ... While mobile cloud computing make a great contribution. to our daily lives, it will also, however, bring numerous chal-lenges and problems. In short, the core ...
1. Introduction. In recent years, mobile cloud computing (MCC) is playing a crucial role in connectivity and accessibility to services and applications [].MCC is a major area of interest evolving out of mobile devices and cloud computing [1-3].It is an approach that aims to enable mobile terminals to access robust and reliable cloud-based computing that facilitates the optimal utilization of ...
PhD Research Topics in Cloud Computing. Cloud computing is known as the universal platform of converged technology. PhD Research Topics in Cloud Computing is the junction of advances. In fact, it is the best place to dig essential ideas for your research. At the same time, it is "flexible to adapt new algorithms and mechanisms.".
This field of MCC composes of two types as general-purpose computing and application-specific computing. The main concept of this field is to support mobile sensing, gaming, social networking and so on. Here are the main research topics in the field of mobile cloud computing. Top 6 Topics in Mobile Cloud Computing. Workload Sharing
Major PHD RESEARCH TOPIC IN MOBILE CLOUD COMPUTING includes Mobile power conservation, also Mobile security issues, Mobile virtualization and quality of Service. It has also a wide scope in the fields like cloud based M-learning, M commerce, Mobile games, also Mobile healthcare and assistive technology. It has made the mobile technology more ...
PhD projects in Mobile Cloud Computing are our best research service for PhD/MS entrants. It gives the chance to choose the desired topics for their research career. At the same time, it stretches the vast environs for both "data storage and processing.". For the most part, it will function outside the mobile devices with the help of mobile ...
Below are 10 the most demanded research topics in the field of cloud computing: 1. Big Data. Big data refers to the large amounts of data produced by various programs in a very short duration of time. It is quite cumbersome to store such huge and voluminous amounts of data in company-run data centers. Also, gaining insights from this data ...
Top 14 Cloud Computing Research Topics For 2022. 1. Green Cloud Computing. Due to rapid growth and demand for cloud, the energy consumption in data centers is increasing. Green Cloud Computing is used to minimize energy consumption and helps to achieve efficient processing and reduce the generation of E-waste.
Anatol Badach. University of Applied Sciences Fulda. Dear Ankita Jiyani, as a very broad current topic for your PhD can be: „ Analysis of Security in SDN-enabled Cloud Computing Environments ...
Cloud Computing is gaining so much popularity an demand in the market. It is getting implemented in many organizations very fast. One of the major barriers for the cloud is real and perceived lack of security. There are many Cloud Computing Research Topics, which can be further taken to get the fruitful output.. In this tutorial, we are going to discuss 12 latest Cloud Computing Research Topics.
Cloud computing is a technology of buying or selling resources, applications, software, and storage services from service providers. Also, the cloud can supply the required computing service regardless of end-user system setup and locality. This article is deal with highly demanding Cloud Computing PhD Topics with its future research developments.
Mobile Cloud Computing Projects is always preparing to succeed in the student's project. Our cloud company is the best choice to receive your final year or PhD projects. With the wide range of scope in the cloud, we will assign our mentor team to find the current topics. From that, we come to know that the mobile cloud is a recent area.
PHD ASSISTANCE. Cloud Computing Research Projects; Data Mining Research Topics; PhD Thesis in Medical Image Processing ... Thesis Topic on Networking; Network Simulator Thesis Topics; PhD SDN Projects; PhD VANET Projects; Body Area Network Projects; 4G Network Simulation Projects; 5G Network Simulation Projects ... Mobile Cloud Storage Dataset ...
Drone networking technology and robotics. Modelling and analysis of mobile data. Wireless system and signal applications. The following topics of research are based on edge-centric learning and federated learning which resource-efficient is high.
He received the M.E and PhD degree from Anna University, Chennai. His research interests include network security, big data, cloud computing, web services and wireless systems. In particular, he is currently working in a research group developing new Internet security architectures and active defence systems against DDoS attacks. Dr.
Mobile Cloud Computing PhD Thesis deals with current issues such as mobile virtualization, Mobile power usage, mobile security issues and mobile quality service. Many mobile based fields such as games, healthcare, M-Commerce, M-Learning, and assistive technology are also part and parcel of the currently in trend Mobile Cloud Computing PhD ...
By Isabella Bachman. The Biomedical Engineering Society, in collaboration with Bioengineering Technology & Entrepreneurship Center (BTEC), hosted the second annual BTEC x BMES Design-A-Thon on May 4.The design challenged students to developing a product or service that will yield positive health outcomes for, and/or increase access, to healthcare technologies in underserved communities.
Recent Research in Cool Cloud Computing. Isolation, Protection and also compliance management for private, public and hybrid cloud. Automatic business workflow and also process management in cloud. Cloud-orchestration provisioning. Cloud SLA (Service Level Agreement) and also quality management. Self-service cloud dashboard, portal and also ...