Suggestions or feedback?

MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
Is online privacy possible?

Previous image Next image
Share this news article on:
Related links.
- Information Services & Technology
Related Topics
More mit news.

An expansive approach to making new compounds
Read full story →

Q&A: A graduating student looks back on his MIT experience

Eleven from MIT awarded 2024 Fulbright fellowships

Robotic palm mimics human touch

Trying to make the grade
Janabel Xia: Algorithms, dance rhythms, and the drive to succeed
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram

Photo by Raghu Rai/Magnum
Privacy is power
Don’t just give away your privacy to the likes of google and facebook – protect it, or you disempower us all.
by Carissa Véliz + BIO
Imagine having a master key for your life. A key or password that gives access to the front door to your home, your bedroom, your diary, your computer, your phone, your car, your safe deposit, your health records. Would you go around making copies of that key and giving them out to strangers? Probably not the wisest idea – it would be only a matter of time before someone abused it, right? So why are you willing to give up your personal data to pretty much anyone who asks for it?
Privacy is the key that unlocks the aspects of yourself that are most intimate and personal, that make you most you, and most vulnerable. Your naked body. Your sexual history and fantasies. Your past, present and possible future diseases. Your fears, your losses, your failures. The worst thing you have ever done, said, and thought. Your inadequacies, your mistakes, your traumas. The moment in which you have felt most ashamed. That family relation you wish you didn’t have. Your most drunken night.
When you give that key, your privacy, to someone who loves you, it will allow you to enjoy closeness, and they will use it to benefit you. Part of what it means to be close to someone is sharing what makes you vulnerable, giving them the power to hurt you, and trusting that person never to take advantage of the privileged position granted by intimacy. People who love you might use your date of birth to organise a surprise birthday party for you; they’ll make a note of your tastes to find you the perfect gift; they’ll take into account your darkest fears to keep you safe from the things that scare you. Not everyone will use access to your personal life in your interest, however. Fraudsters might use your date of birth to impersonate you while they commit a crime; companies might use your tastes to lure you into a bad deal; enemies might use your darkest fears to threaten and extort you. People who don’t have your best interest at heart will exploit your data to further their own agenda. Privacy matters because the lack of it gives others power over you.
You might think you have nothing to hide, nothing to fear. You are wrong – unless you are an exhibitionist with masochistic desires of suffering identity theft, discrimination, joblessness, public humiliation and totalitarianism, among other misfortunes. You have plenty to hide, plenty to fear, and the fact that you don’t go around publishing your passwords or giving copies of your home keys to strangers attests to that.
You might think your privacy is safe because you are a nobody – nothing special, interesting or important to see here. Don’t shortchange yourself. If you weren’t that important, businesses and governments wouldn’t be going to so much trouble to spy on you.
You have your attention, your presence of mind – everyone is fighting for it. They want to know more about you so they can know how best to distract you, even if that means luring you away from quality time with your loved ones or basic human needs such as sleep. You have money, even if it is not a lot – companies want you to spend your money on them. Hackers are eager to get hold of sensitive information or images so they can blackmail you. Insurance companies want your money too, as long as you are not too much of a risk, and they need your data to assess that. You can probably work; businesses want to know everything about whom they are hiring – including whether you might be someone who will want to fight for your rights. You have a body – public and private institutions would love to know more about it, perhaps experiment with it, and learn more about other bodies like yours. You have an identity – criminals can use it to commit crimes in your name and let you pay for the bill. You have personal connections. You are a node in a network. You are someone’s offspring, someone’s neighbour, someone’s teacher or lawyer or barber. Through you, they can get to other people. That’s why apps ask you for access to your contacts. You have a voice – all sorts of agents would like to use you as their mouthpiece on social media and beyond. You have a vote – foreign and national forces want you to vote for the candidate that will defend their interests.
As you can see, you are a very important person. You are a source of power.
By now, most people are aware that their data is worth money. But your data is not valuable only because it can be sold. Facebook does not technically sell your data, for instance. Nor does Google. They sell the power to influence you. They sell the power to show you ads, and the power to predict your behaviour. Google and Facebook are not really in the business of data – they are in the business of power. Even more than monetary gain, personal data bestows power on those who collect and analyse it, and that is what makes it so coveted.
T here are two aspects to power. The first aspect is what the German philosopher Rainer Forst in 2014 defined as ‘the capacity of A to motivate B to think or do something that B would otherwise not have thought or done’. The means through which the powerful enact their influence are varied. They include motivational speeches, recommendations, ideological descriptions of the world, seduction and credible threats. Forst argues that brute force or violence is not an exercise of power, for subjected people don’t ‘do’ anything; rather, something is done to them. But clearly brute force is an instance of power. It is counterintuitive to think of someone as powerless who is subjecting us through violence. Think of an army dominating a population, or a thug strangling you. In Economy and Society (1978), the German political economist Max Weber describes this second aspect of power as the ability for people and institutions to ‘carry out [their] own will despite resistance’.
In short, then, powerful people and institutions make us act and think in ways in which we would not act and think were it not for their influence. If they fail to influence us into acting and thinking in the way that they want us to, powerful people and institutions can exercise force upon us – they can do unto us what we will not do ourselves.
There are different types of power: economic, political and so on. But power can be thought of as being like energy: it can take many different forms, and these can change. A wealthy company can often use its money to influence politics through lobbying, for instance, or to shape public opinion through paying for ads.
Power over others’ privacy is the quintessential kind of power in the digital age
That tech giants such as Facebook and Google are powerful is hardly news. But exploring the relationship between privacy and power can help us to better understand how institutions amass, wield and transform power in the digital age, which in turn can give us tools and ideas to resist the kind of domination that survives on violations of the right to privacy. However, to grasp how institutions accumulate and exercise power in the digital age, first we have to look at the relationship between power, knowledge and privacy.
There is a tight connection between knowledge and power. At the very least, knowledge is an instrument of power. The French philosopher Michel Foucault goes even further, and argues that knowledge in itself is a form of power . There is power in knowing. By protecting our privacy, we prevent others from being empowered with knowledge about us that can be used against our interests.
The more that someone knows about us, the more they can anticipate our every move, as well as influence us. One of the most important contributions of Foucault to our understanding of power is the insight that power does not only act upon human beings – it constructs human subjects (even so, we can still resist power and construct ourselves). Power generates certain mentalities, it transforms sensitivities, it brings about ways of being in the world. In that vein, the British political theorist Steven Lukes argues in his book Power (1974) that power can bring about a system that produces wants in people that work against their own interests. People’s desires can themselves be a result of power, and the more invisible the means of power, the more powerful they are. Examples of power shaping preferences today include when tech uses research about how dopamine works to make you addicted to an app, or when you are shown political ads based on personal information that makes a business think you are a particular kind of person (a ‘persuadable’, as the data-research company Cambridge Analytica put it, or someone who might be nudged into not voting, for instance).
The power that comes about as a result of knowing personal details about someone is a very particular kind of power. Like economic power and political power, privacy power is a distinct type of power, but it also allows those who hold it the possibility of transforming it into economic, political and other kinds of power. Power over others’ privacy is the quintessential kind of power in the digital age.
T wo years after it was funded and despite its popularity, Google still hadn’t developed a sustainable business model. In that sense, it was just another unprofitable internet startup. Then, in 2000, Google launched AdWords, thereby starting the data economy. Now called Google Ads, it exploited the data produced by Google’s interactions with its users to sell ads. In less than four years, the company achieved a 3,590 per cent increase in revenue.
That same year, the Federal Trade Commission had recommended to US Congress that online privacy be regulated. However, after the attacks of 11 September 2001 on the Twin Towers in New York, concern about security took precedence over privacy, and plans for regulation were dropped. The digital economy was able to take off and reach the magnitude it enjoys today because governments had an interest in having access to people’s data in order to control them. From the outset, digital surveillance has been sustained through a joint effort between private and public institutions.
The mass collection and analysis of personal data has empowered governments and prying companies. Governments now know more about their citizens than ever before. The Stasi (the security service of the German Democratic Republic), for instance, managed to have files only on about a third of the population, even if it aspired to have complete information on all citizens. Intelligence agencies today hold much more information on all of the population. To take just one important example, a significant proportion of people volunteer private information in social networks. As the US filmmaker Laura Poitras put it in an interview with The Washington Post in 2014: ‘Facebook is a gift to intelligence agencies.’ Among other possibilities, that kind of information gives governments the ability to anticipate protests, and even pre-emptively arrest people who plan to take part. Having the power to know about organised resistance before it happens, and being able to squash it in time, is a tyrant’s dream.
Tech companies’ power is constituted, on the one hand, by having exclusive control of data and, on the other, by the ability to anticipate our every move, which in turn gives them opportunities to influence our behaviour, and sell that influence to others. Companies that earn most of their revenues through advertising have used our data as a moat – a competitive advantage that has made it impossible for alternative businesses to challenge tech titans. Google’s search engine, for example, is as good as it is partly because its algorithm has much more data to learn from than any of its competitors. In addition to keeping the company safe from competitors and allowing it to train its algorithm better, our data also allows tech companies to predict and influence our behaviour. With the amount of data it has access to, Google can know what keeps you up at night, what you desire the most, what you are planning to do next. It then whispers this information to other busybodies who want to target you for ads.
Tech wants you to think that the innovations it brings into the market are inevitable
Companies might also share your data with ‘data brokers’ who will create a file on you based on everything they know about you (or, rather, everything they think they know), and then sell it to pretty much whoever is willing to buy it – insurers, governments, prospective employers, even fraudsters.
Data vultures are incredibly savvy at using both the aspects of power discussed above: they make us give up our data, more or less voluntarily, and they also snatch it away from us, even when we try to resist. Loyalty cards are an example of power making us do certain things that we would otherwise not do. When you are offered a discount for loyalty at your local supermarket, what you are being offered is for that company to conduct surveillance on you, and then influence your behaviour through nudges (discounts that will encourage you to buy certain products). An example of power doing things to us that we don’t want it to do is when Google records your location on your Android smartphone, even when you tell it not to.
Both types of power can also be seen at work at a more general level in the digital age. Tech constantly seduces us into doing things we would not otherwise do, from getting lost down a rabbit hole of videos on YouTube, to playing mindless games, or checking our phone hundreds of times a day. The digital age has brought about new ways of being in the world that don’t always make our lives better. Less visibly, the data economy has also succeeded in normalising certain ways of thinking. Tech companies want you to think that, if you have done nothing wrong, you have no reason to object to their holding your data. They also want you to think that treating your data as a commodity is necessary for digital tech, and that digital tech is progress – even when it might sometimes look worryingly similar to social or political regress. More importantly, tech wants you to think that the innovations it brings into the market are inevitable. That’s what progress looks like, and progress cannot be stopped.
That narrative is complacent and misleading. As the Danish economic geographer Bent Flyvbjerg points out in Rationality and Power (1998), power produces the knowledge, narratives and rationality that are conducive to building the reality it wants. But technology that perpetuates sexist and racist trends and worsens inequality is not progress. Inventions are far from unavoidable. Treating data as a commodity is a way for companies to earn money, and has nothing to do with building good products. Hoarding data is a way of accumulating power. Instead of focusing only on their bottom line, tech companies can and should do better to design the online world in a way that contributes to people’s wellbeing. And we have many reasons to object to institutions collecting and using our data in the way that they do.
Among those reasons is institutions not respecting our autonomy, our right to self-govern. Here is where the harder side of power plays a role. The digital age thus far has been characterised by institutions doing whatever they want with our data, unscrupulously bypassing our consent whenever they think they can get away with it. In the offline world, that kind of behaviour would be called matter-of-factly ‘theft’ or ‘coercion’. That it is not called this in the online world is yet another testament to tech’s power over narratives.
I t’s not all bad news, though. Yes, institutions in the digital age have hoarded privacy power, but we can reclaim the data that sustains it, and we can limit their collecting new data. Foucault argued that, even if power constructs human subjects, we have the possibility to resist power and construct ourselves. The power of big tech looks and feels very solid. But tech’s house of cards is partly built on lies and theft. The data economy can be disrupted. The tech powers that be are nothing without our data. A small piece of regulation, a bit of resistance from citizens, a few businesses starting to offer privacy as a competitive advantage, and it can all evaporate.
No one is more conscious of their vulnerability than tech companies themselves. That is why they are trying to convince us that they do care about privacy after all (despite what their lawyers say in court). That is why they spend millions of dollars on lobbying. If they were so certain about the value of their products for the good of users and society, they would not need to lobby so hard. Tech companies have abused their power, and it is time to resist them.
In the digital age, resistance inspired by the abuse of power has been dubbed a techlash. Abuses of power remind us that power needs to be curtailed for it to be a positive influence in society. Even if you happen to be a tech enthusiast, even if you think that there is nothing wrong with what tech companies and governments are doing with our data, you should still want power to be limited, because you never know who will be in power next. Your new prime minister might be more authoritarian than the old one; the next CEO of the next big tech company might not be as benevolent as those we’ve seen thus far. Tech companies have helped totalitarian regimes in the past, and there is no clear distinction between government and corporate surveillance. Businesses share data with governments, and public institutions share data with companies.
When you expose your privacy, you put us all at risk
Do not give in to the data economy without at least some resistance. Refraining from using tech altogether is unrealistic for most people, but there is much more you can do short of that. Respect other people’s privacy. Don’t expose ordinary citizens online. Don’t film or photograph people without their consent, and certainly don’t share such images online. Try to limit the data you surrender to institutions that don’t have a claim to it. Imagine someone asks for your number in a bar and won’t take a ‘No, thank you’ for an answer. If that person were to continue to harass you for your number, what would you do? Perhaps you would be tempted to give them a fake number. That is the essence of obfuscation, as outlined by the media scholars Finn Bruton and Helen Nissenbaum in the 2015 book of that name. If a clothing company asks for your name to sell you clothes, give them a different name – say, Dr Private Information, so that they get the message. Don’t give these institutions evidence they can use to claim that we are consenting to our data being taken away from us. Make it clear that your consent is not being given freely.
When downloading apps and buying products, choose products that are better for privacy. Use privacy extensions on your browsers. Turn your phone’s wi-fi, Bluetooth and locations services off when you don’t need them. Use the legal tools at your disposal to ask companies for the data they have on you, and ask them to delete that data. Change your settings to protect your privacy. Refrain from using one of those DNA home testing kits – they are not worth it. Forget about ‘smart’ doorbells that violate your privacy and that of others. Write to your representatives sharing your concerns about privacy. Tweet about it. Take opportunities as they come along to inform business, governments and other people that you care about privacy, that what they are doing is not okay.
Don’t make the mistake of thinking you are safe from privacy harms, maybe because you are young, male, white, heterosexual and healthy. You might think that your data can work only for you, and never against you, if you’ve been lucky so far. But you might not be as healthy as you think you are, and you will not be young forever. The democracy you are taking for granted might morph into an authoritarian regime that might not favour the likes of you.
Furthermore, privacy is not only about you. Privacy is both personal and collective. When you expose your privacy, you put us all at risk. Privacy power is necessary for democracy – for people to vote according to their beliefs and without undue pressure, for citizens to protest anonymously without fear of repercussions, for individuals to have freedom to associate, speak their minds, read what they are curious about. If we are going to live in a democracy, the bulk of power needs to be with the people. If most of the power lies with companies, we will have a plutocracy. If most of the power lies with the state, we will have some kind of authoritarianism. Democracy is not a given. It is something we have to fight for every day. And if we stop building the conditions in which it thrives, democracy will be no more. Privacy is important because it gives power to the people. Protect it.

Nations and empires
A United States of Europe
A free and unified Europe was first imagined by Italian radicals in the 19th century. Could we yet see their dream made real?
Fernanda Gallo

Stories and literature
On Jewish revenge
What might a people, subjected to unspeakable historical suffering, think about the ethics of vengeance once in power?
Shachar Pinsker

Building embryos
For 3,000 years, humans have struggled to understand the embryo. Now there is a revolution underway
John Wallingford

Design and fashion
Sitting on the art
Given its intimacy with the body and deep play on form and function, furniture is a ripely ambiguous artform of its own
Emma Crichton Miller

Learning to be happier
In order to help improve my students’ mental health, I offered a course on the science of happiness. It worked – but why?

Consciousness and altered states
How perforated squares of trippy blotter paper allowed outlaw chemists and wizard-alchemists to dose the world with LSD
Hi there! We use cookies to give you the best site experience.
Privacy Preferences Center
We use cookies along with other tools to help the Clario website load faster. Our cookie files never contain personal data. This means information like your location, email, or IP address always remain unknown to us.
Help us improve your website experience by accepting the use of cookies. You can change your privacy settings whenever you like.
Manage consent
All cookies
These cookies are strictly necessary for enabling basic website functionality (including page navigation, form submission, language detection, post commenting), downloading and purchasing software. The website might malfunction without these cookies.
We stand with Ukraine to help keep people safe. Join us
Table of contents
Why is online privacy important?
Concerns around personal privacy on the internet, what is information privacy, how does digital privacy differ from information security, major internet privacy issues, our security tips to protect your privacy online, what online privacy is and why it's important.
Online privacy has become a pressing issue due to the number of data breaches and identity theft instances. It is astonishing how easy it is to learn anything you want about anyone you know. Fortunately, there are ways to protect privacy. The first step — educate yourself. Second — use VPN.
Get it for iOS , Android
The right to be forgotten: data privacy as a human right
Search engines user tracking, social media data harvesting, cookies/online tracking, mobile apps and privacy, identity theft.
Online privacy definition
Online privacy, also known as internet privacy or digital privacy, refers to how much of your personal, financial, and browsing data remains private when you’re online. It has become a growing worry, with browsing history and personal data at increased risk.
To give an example, the number of data breaches publicly reported in the US through September 2021 outstripped the whole last year by 17%.
Many people underestimate the importance of online privacy, but they should be aware of how much information they’re sharing — not just on social networks but just through browsing itself.
So what are those privacy issues that you might come across? And how can you securely share your personal data online? Read on to find it out.
The importance of digital privacy becomes clear once you try to make a mental list of personal things you’re ready to share with complete strangers — and those you’d rather not. For sure, you don’t want your medical records, bank statements, or even certain items from your shopping cart to be widely known. Anyone who watched You saw how easy it was for people to get hold of someone’s personal information like home address, friends’ names, tastes, or favorite places based on what they publicly shared.
Yes, you can make your social media account private and share only specific content with a specific group of people. But how can you really know what social media does with the data you share? And what about your other online traces, like browsing history, purchases, or even your online correspondence?
A poll of American internet users revealed that 81% of respondents believed they had no control over data collected by private companies. Even worse — the number climbed to 84% when people were asked if they could control what data the government collected.
To address similar concerns, the EU adopted the GDPR , or the General Data Protection Regulation. This set of laws, passed in 2016 and implemented in 2018, was intended to protect every EU citizen’s privacy and data.
California’s equivalent CCPA also gives consumers four basic rights to control personal information on the internet, including:
- The right to know what personal information a business collects about them and how it is used and shared
- The right to delete the personal information they shared
- The right to opt-out of the sale of their personal information
- The right to non-discrimination for exercising their CCPA rights
At the same time, some tech companies store customer information dating back to years ago. They’ve been logging every website they visited, all their preferences, shopping habits, political views, and many more. How can you address that?
The right to be forgotten is the right to ask companies to delete and surrender any information they’ve gathered about you. It covers online chatting and third-party discussions. People have fought to remove their names and images from “revenge porn,” including any relevant search engine results. Some have submitted take-down requests for uncomfortable personal stories from their past, for example, petty crime reports or embarrassing viral stories.
Arguably, the right to be forgotten protects those who want to forget about their old mistakes and restore privacy. The opposite camp, incidentally including some tech giants, criticizes this as censorship and rewriting of history.
Information privacy (also known as data privacy) is a branch of data security aimed at proper data handling, including consent, notice, and regulatory obligations. Simply put, it’s an ability to control what details you reveal about yourself on the internet and who can access it.
As a vital component of information sharing, data privacy is an umbrella term for:
- Online privacy
- Financial privacy
- Medical privacy
Data masking, encryption, and authentication are just a few methods used to ensure that information is made available only to the authorized parties.
Online privacy and security are closely related concepts that impact your cyber safety. There are some specific differences between them, though.
Digital privacy refers to the proper usage, handling, processing, and storage of personal information.
Information security is about protecting data against malicious attacks or unauthorized access.
A case in point: if you have a social media account, your password is an aspect of information security. The way social media handles your information is an aspect of digital privacy. As a rule, you consent to security and privacy regulations by clicking “I agree” to the company’s privacy policy and Terms and Conditions. But let’s be honest: when was the last time you carefully read through an app’s privacy policy before accepting it? Still, it’s not the only thing that can give you a headache with digital privacy issues.
Online privacy issues range from the information you don’t mind sharing (say, a public social media account) and annoying privacy trade-offs like targeted ads to public embarrassment or breaches that affect your personal life.
Let’s look at the most controversial, privacy-invading practices.
Search engines log not only things you’ve been looking for. They also track websites that you visit after that. If your search engine provider doubles as a browser, they keep all your browsing history, too.
Search engines can (and do) collect:
- Search history
- IP addresses
- Click-through history
Taken together, this information can be used for “profiling”, or making a customer persona based on the person’s browsing, shopping, and social media preferences. Among other things, customer personas are widely used in personalizing ads. Profiling becomes a serious privacy issue, though, when data-matching algorithms associate someone’s profile with their personally identifiable information, as this might lead to data breaches.
By blocking irritating pop-up ads and keeping trackers at bay, Clario will help you maintain your online privacy while enjoying web browsing.
In recent years, social media privacy hit the spotlight after a string of scandals, including the Cambridge Analytica story when they used data to manipulate voters, cyberbullying, and “doxing” (sharing private information publicly).
On top of that, major social networks have suffered data breaches, leaving millions of users exposed. A recent example is Facebook’s massive data breach that exposed the personal data of 533 million users, including their full names, phone numbers, locations, birth dates, bios, and email addresses.
For the most part, cookies are harmless and even helpful. These pieces of code collect your browsing information and let websites remember your login, preferences, language settings, and other details.
However, cookies might become a concern when it comes to vast amounts of data collected without user consent.
In December 2020, France’s data protection regulator, the Commission Nationale de l’informatique et des libertés (CNIL), ruled that Google and Amazon had to pay 121 million dollars and 35 million euros for breaching Article 82 of the French Data Protection Act. CNIL fined both companies for placing tracking cookies on their user’s computers without prior consent. Google went even further and tracked users who had deactivated ad personalization.
COVID-19 has pushed people to migrate into mobile. The recent App Annie report states that the users’ average time spent with their smartphones topped 4 hours 10 minutes in 2020 — up 20% from 2019. More time spent on mobile means more internet browsing, ads clicking, and, of course, app downloads. As a result, our apps have learned a lot more about us.
But can we be one hundred percent sure what exactly those apps know about us?
Many apps request location details, usernames, phone numbers, or email addresses. Yet, some go further and ask you for risky permissions — information that could cause trouble if it fell into the wrong hands. It could be access to your phone’s microphone/recorder, camera, contacts, or even messages.
A good rule of thumb is to consider whether you trust the app provider to keep this information. If there’s anything you feel uncomfortable about, you can deny access, either when the app asks you for permission or later in the app’s settings.
Identity theft is nothing new. It has been a crime long before the internet. But new technology has opened up fresh avenues for con artists and thieves.
Online identity theft happens when someone accesses your personally identifiable information (PII) to commit fraud. This information might be your driver’s license, bank account details, tax numbers, or anything else that can be used to impersonate you online. In the worst-case scenario, your information might end up for sale on the dark web .
To get this information, bad actors use the following tricks:
- Phishing . Criminals pose as reputable contacts, such as financial institutions, to trick you into surrendering sensitive information or opening malicious attachments
- Malware . Malicious software that can access your device’s operating system and allow hackers to steal your personal information
- Pharming . Hijacking information using a virus without your knowledge, often through a fake site
- Discarded computers and phones. Make sure you thoroughly scrub any device you get rid of before you sell it or give it away
According to the FTC report , the COVID-19 pandemic has been a ripe time for identity thieves, with the number of ID theft cases more than doubling in 2020 compared to 2019.
All those privacy and security issues on the internet might sound scary and can make you feel helpless, but there are simple steps you can take right now to cut the risk of online fraud.
If you worry about how much of your private information is available on the internet, here’s a list of recommendations the Clario team has prepared for you to help you manage and protect your personal information.
1. Secure your devices and use antivirus software
Hackers use various schemes to steal your data. Many of them may not be obvious at first sight. Consider using an up to date, industry-leading antivirus software on your device, whether it’s a mobile or computer. If you're looking for a solution for both, Clario easily combines an antivirus app for Android , iOS, and macOS - all within a single subscription, and even more:
- Anti-tracking tool to prevent websites from collecting your data
- VPN to hide your IP address and online activity
- Anti-spyware tool to stop hackers from spying on you
To maintain your privacy on the internet, please do the following:
- Install Clario
- Get a subscription to create an account
- On the dashboard, click Device
- Hit Start scan and wait for Clario to check your device for malware
- In case Clario detects malicious files, follow the on-screen instructions to protect your data.
Don't forget to encrypt your connection.
- Toggle the Browsing protection switch on
- Click Turn on
- Allow Clario to add VPN Configurations to the settings
- Choose a server location from our extended list
- Enjoy secure browsing!
Voila! Your browsing is now fully protected.
If you are a Chrome user, we would also suggest installing Clario's ad blocker . It’s a web extension that will keep all kinds of advertising, online tracking, and adware at bay. It’s completely free and works with Chrome (you can install it directly from the Chrome Web Store ) and Safari (you’ll need to install it from the Clario app).
2. Use the DNT setting
DNT stands for “do not track,” and you can change DNT settings in your browsers . When you enable it for your browsing — in Chrome, Firefox, or another browser — you tell websites and third-party partners that you do not want to be tracked.
3. Use cookie-blocking browser extensions
These extensions will limit tracking, especially data harvesting by third parties.
4. Opt out of app tracking
You can restrict your apps’ access to your personal information by going to your app or phone settings and opting out of location or other information tracking.
5. Review privacy policies carefully
A common mistake in online browsing is to simply click “agree” to any user agreements and privacy policies without reading them. We strongly recommend looking through any document before clicking “agree” or “accept.”
If you don’t have time to read it (and some user agreements are hundreds of pages long), do at least some research of what kind of information the app or website asks of its users and whether you’re comfortable with that.
6. Browse in incognito mode
Choose incognito mode , or private browsing, when doing things online. Then your online history won’t be stored or remembered.
7. Use a different search engine
If you’re concerned about what your search engine knows about you, it might be a good idea to switch to another engine. DuckDuckGo , for instance, markets itself as a more private and secure alternative to Google.
8. Be wary of what you click online
Don’t click on links to unsafe or bogus websites, or you risk falling victim to a phishing attack and giving up your sensitive data to a scammer. Some phishing threats are masked as ads, so be extra careful with those.
If you follow these recommendations, you’ll know where the danger may hide. This will help you keep your online privacy intact. If there’s anything else you’d like to know about privacy, security, or any online issues, just browse through Clario’s blog and enjoy your digital experience safely.
By Olga Sushko
Privacy and cybersecurity advocate. Mac lover with a passion for copywriting.
Keep reading

Clario News

Data Protection

Digital Wellness
Are you fully secured online? Get Clario for an all-round protection.
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
How Americans View Data Privacy
1. views of data privacy risks, personal data and digital privacy laws, table of contents.
- Role of social media, tech companies and government regulation
- Americans’ day-to-day experiences with online privacy
- Personal data and information
- Feelings of concern, confusion and a lack of control over one’s data
- Privacy laws and regulation
- Americans largely favor more regulation to protect personal information
- Trust in social media executives
- Children’s online privacy: Concerns and responsibility
- Law enforcement and surveillance
- AI and data collection
- Trust in companies that use AI
- How people approach privacy policies
- How people are protecting their digital privacy
- How Americans handle their passwords
- Data breaches and hacks
- Identifying the most and least knowledgeable, confident and concerned
- Knowledge and privacy choices
- Confidence and privacy choices
- Concern and privacy choices
- The case of privacy policies
- Acknowledgments
- The American Trends Panel survey methodology
- Appendix A: Law enforcement’s use of technology in investigations
- Appendix B: Privacy outcomes by knowledge, confidence and concern
- Appendix C: Confident and independent use of digital devices, by age and education
Online privacy is complex, encompassing debates over law enforcement’s data access, government regulation and what information companies can collect. This chapter examines Americans’ perspectives on these issues and highlights how views vary across different groups, particularly by education and age.
When managing their privacy online, most Americans say they trust themselves to make the right decisions about their personal information (78%), and a majority are skeptical that anything they do will make a difference (61%).
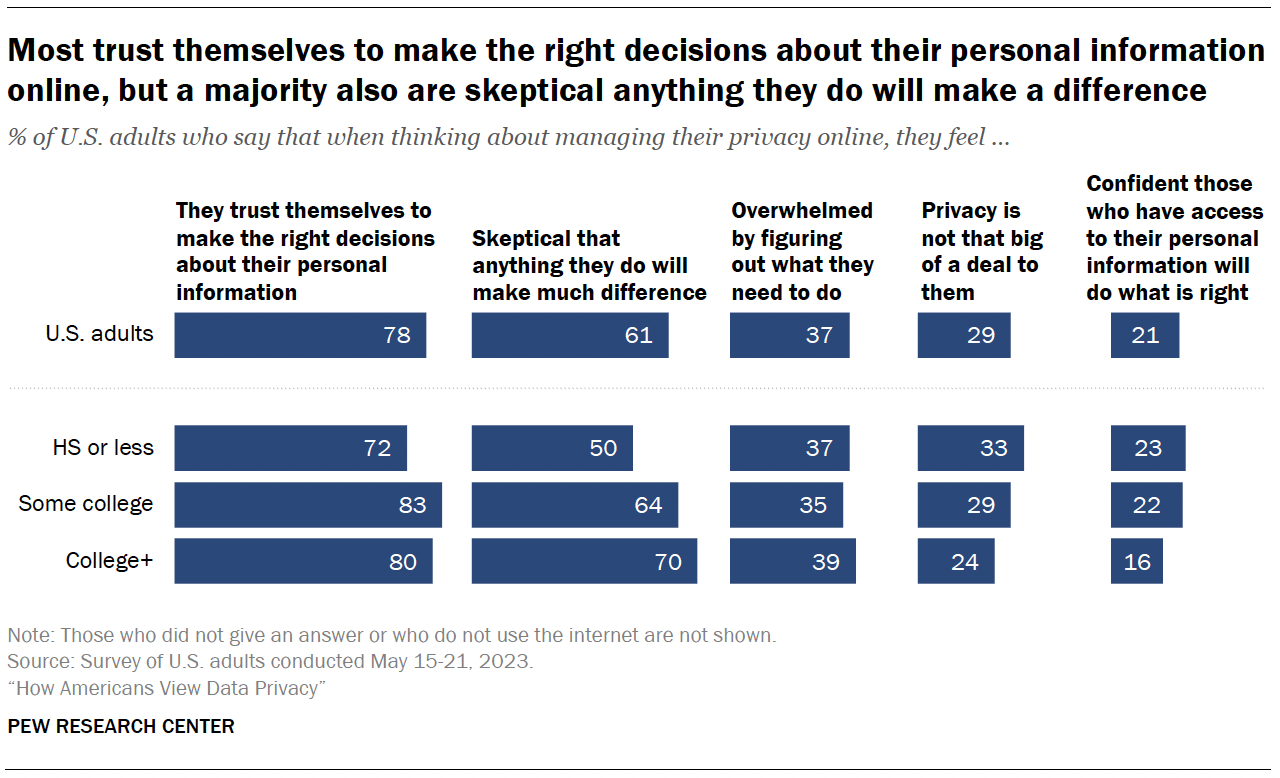
Far fewer mention being overwhelmed by figuring out what they need to do (37%) or say privacy is not that big of a deal to them (29%).
Another 21% are confident that those with access to their personal information will do what is right.
Education differences
- 81% of those with at least some college experience say they trust themselves to make the right decisions about their personal information online, compared with 72% of those with a high school diploma or less.
- 67% of those with at least some college are skeptical that anything they do to manage their online privacy will make a difference, compared with half of those with a high school diploma or less formal education.
On the other hand, those with a high school education or less are more likely than those with some college experience or more to say that privacy isn’t that big of a deal to them and that they are confident that those who have access to their personal information will do the right thing.
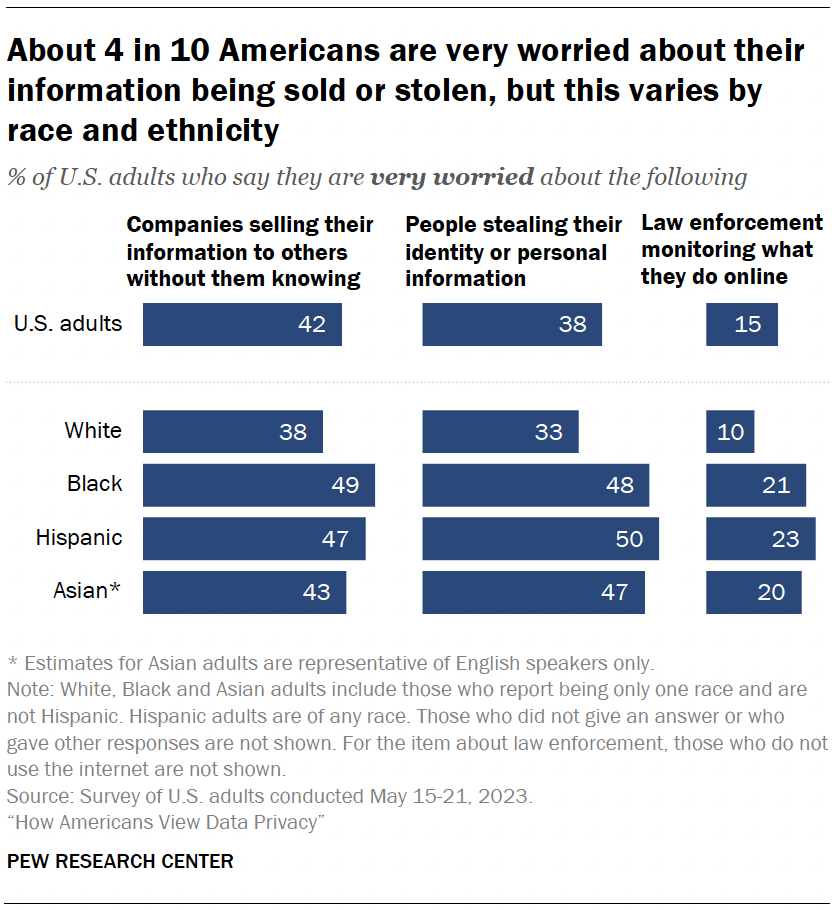
The survey also explores the concerns people have about data collection and security – specifically, how they feel about three scenarios around companies, law enforcement and identity theft.
Roughly four-in-ten Americans say they are very worried about companies selling their information to others without them knowing (42%) or people stealing their identity or personal information (38%). Fewer are apprehensive about law enforcement monitoring what they do online (15%).
Racial and ethnic differences
However, some of these shares are higher among Hispanic, Black or Asian adults: 1
- Roughly half of Hispanic, Black or Asian adults are very worried about people stealing their identity or personal information, compared with a third of White adults.
- About one-in-five of each group are very worried about law enforcement monitoring their online activity; 10% of White adults say this.
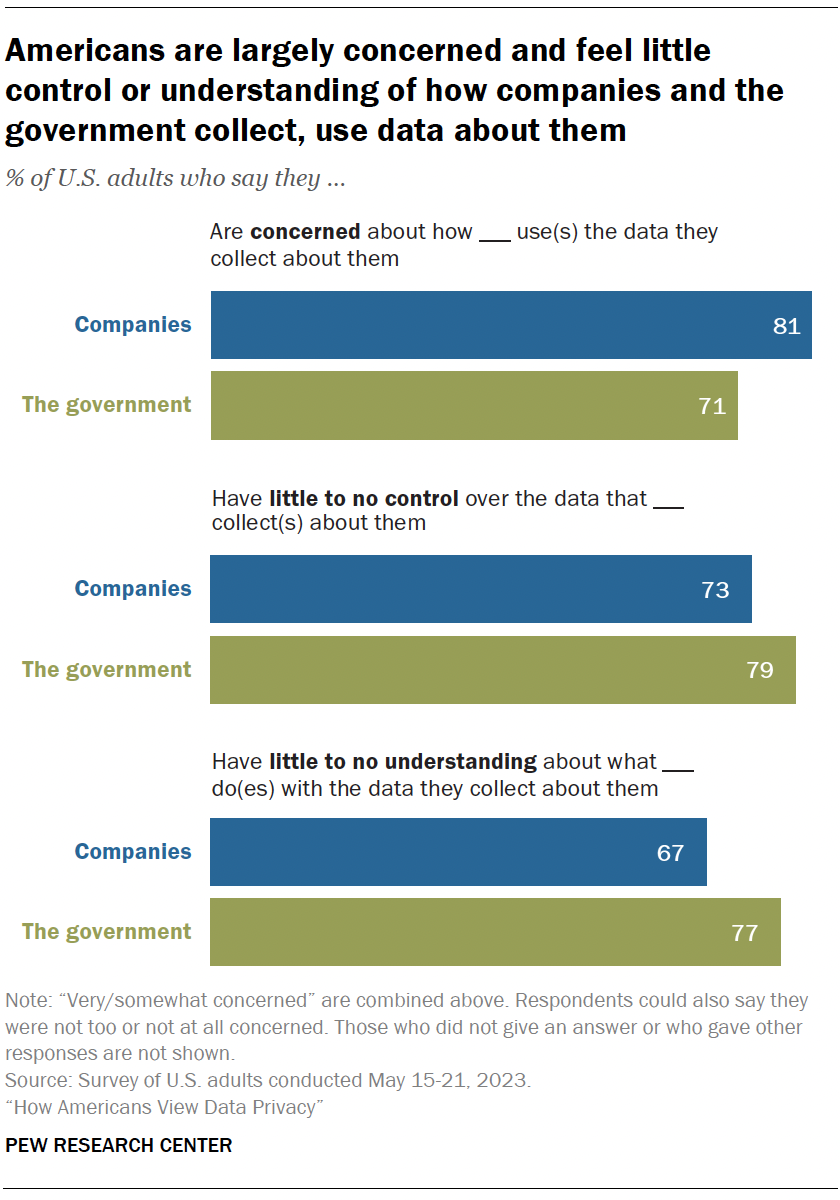
A majority of Americans say they are concerned, lack control and have a limited understanding about how the data collected about them is used. This is true whether it’s the government or companies using their data. Similar sentiments were expressed in 2019, when we last asked about this .
Concern is high: 81% say they feel very or somewhat concerned with how companies use the data they collect about them. Fully 71% say the same regarding the government’s use of data.
People don’t feel in control: Roughly three-quarters or more feel they have very little or no control over the data collected about them by companies (73%) or the government (79%).
Understanding is low: Americans also say they don’t understand what these actors are doing with the data collected about them. Majorities say they have very little or no understanding of this, whether by the government (77%) or companies (67%).
Americans are now less knowledgeable than before about how companies are using their personal data. The share who say they don’t understand this has risen from 59% in 2019 to 67% in 2023.
They have also grown more concerned about how the government uses the data it collects about them, with the share expressing concern up from 64% to 71% over this same period.
While these sentiments have not changed significantly since 2019 among Democrats and those who lean toward the Democratic Party, Republicans and GOP leaners have grown more wary of government data collection. Today, 77% of Republicans say they are concerned about how the government uses data it collects about them, up from 63% four years earlier.
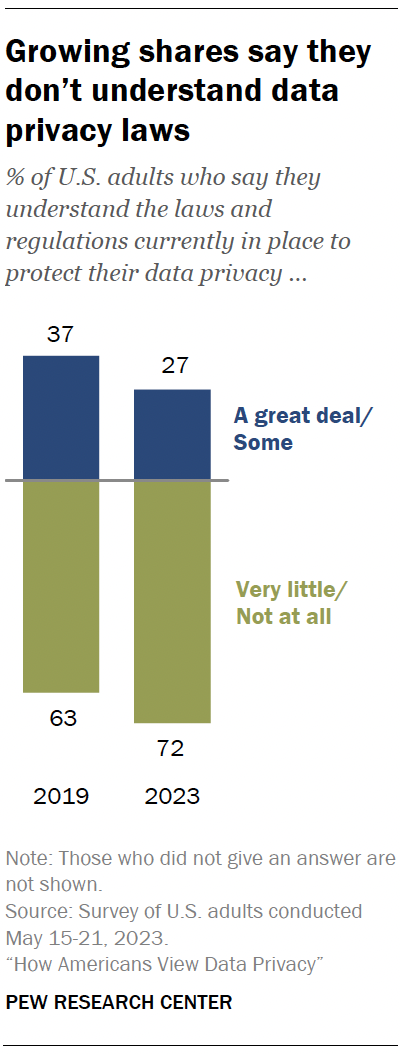
Americans are less knowledgeable about data privacy laws today than in the past.
Today, 72% of Americans say they have little to no understanding about the laws and regulations that are currently in place to protect their data privacy. This is up from 63% in 2019.
By comparison, the shares who say they understand some or a great deal about these laws decreased from 37% in 2019 to 27% in 2023.
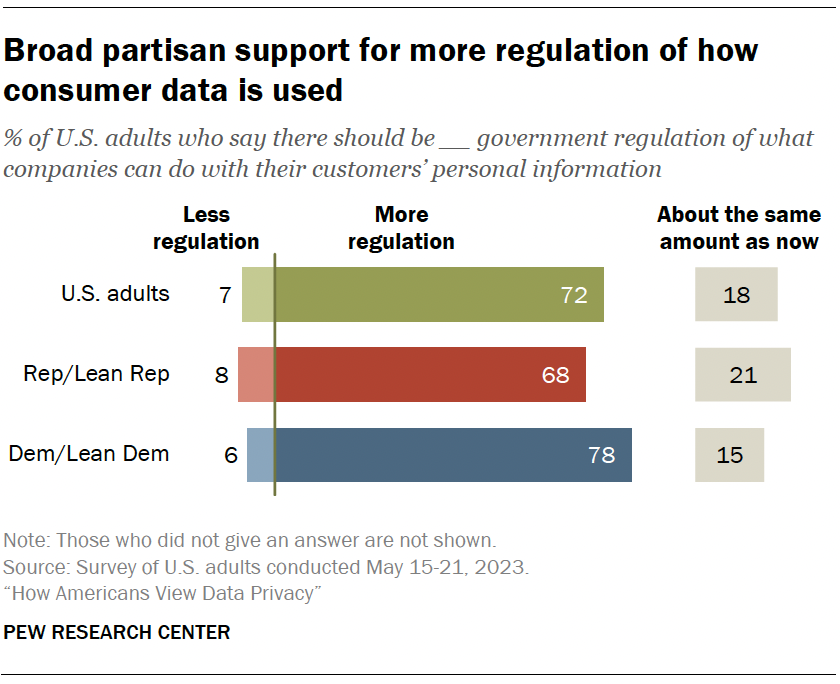
Overall, 72% say there should be more government regulation of what companies can do with their customers’ personal information. Just 7% say there should be less regulation. Another 18% say it should stay about the same.
Views by political affiliation
There is broad partisan support for greater involvement by the government in regulating consumer data.
A majority of Democrats and Republicans say there should be more government regulation for how companies treat users’ personal information (78% vs. 68%).
These findings are largely on par with a 2019 Center survey that showed strong support for increased regulations across parties.
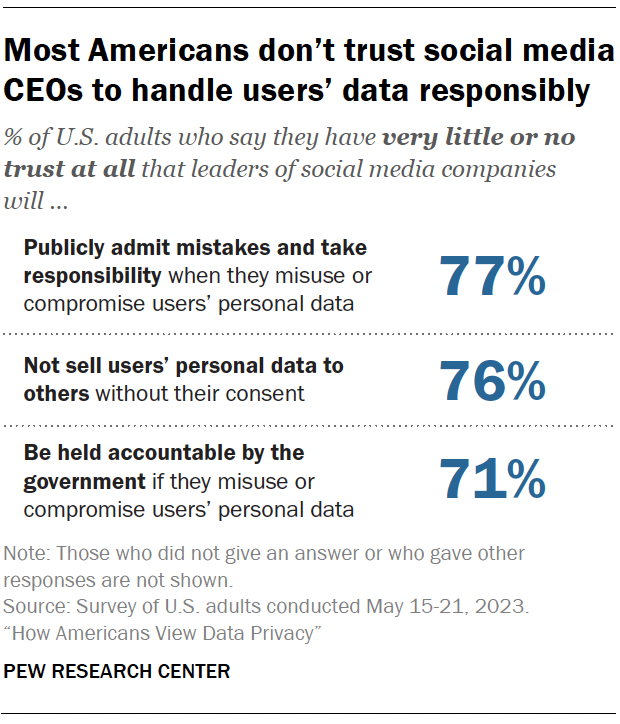
Majorities of Americans say they have little to no trust that leaders of social media companies will publicly admit mistakes regarding consumer data being misused or compromised (77%), that these leaders will not sell users’ personal data to others without their consent (76%), and that leaders would be held accountable by the government if they were to misuse or compromise users’ personal data (71%).
This includes notable shares who have no trust at all in those who are running social media sites. For example, 46% say they have no trust at all in executives of social media companies to not sell users’ data without their consent.
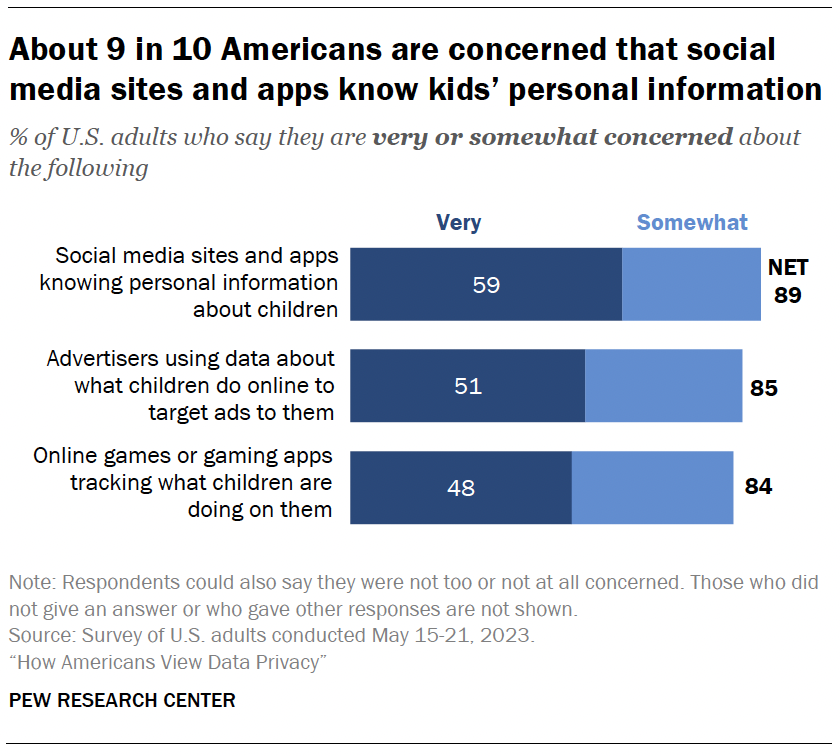
Most Americans say they are concerned about social media sites knowing personal information about children (89%), advertisers using data about what children do online to target ads to them (85%) and online games tracking what children are doing on them (84%).
Concern is widespread, with no statistically significant differences between those with and without children.
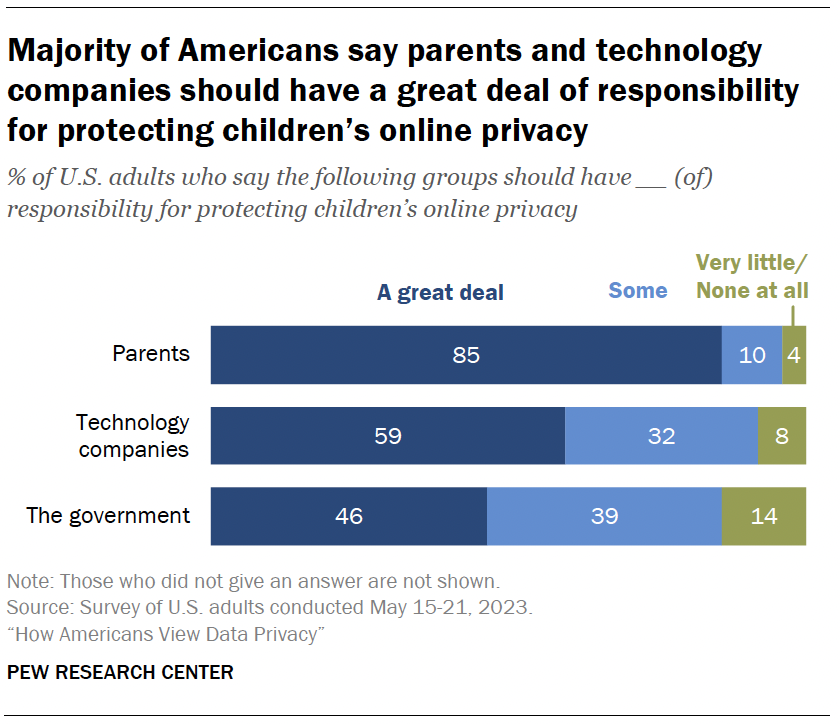
Another key question is who should be responsible for the actual protection of kids’ online privacy.
Fully 85% say parents bear a great deal of responsibility for protecting children’s online privacy. Roughly six-in-ten say the same about technology companies, and an even smaller share believe the government should have a great deal of responsibility.
The survey also measured how acceptable Americans think it is for law enforcement to use surveillance tools during criminal investigations.
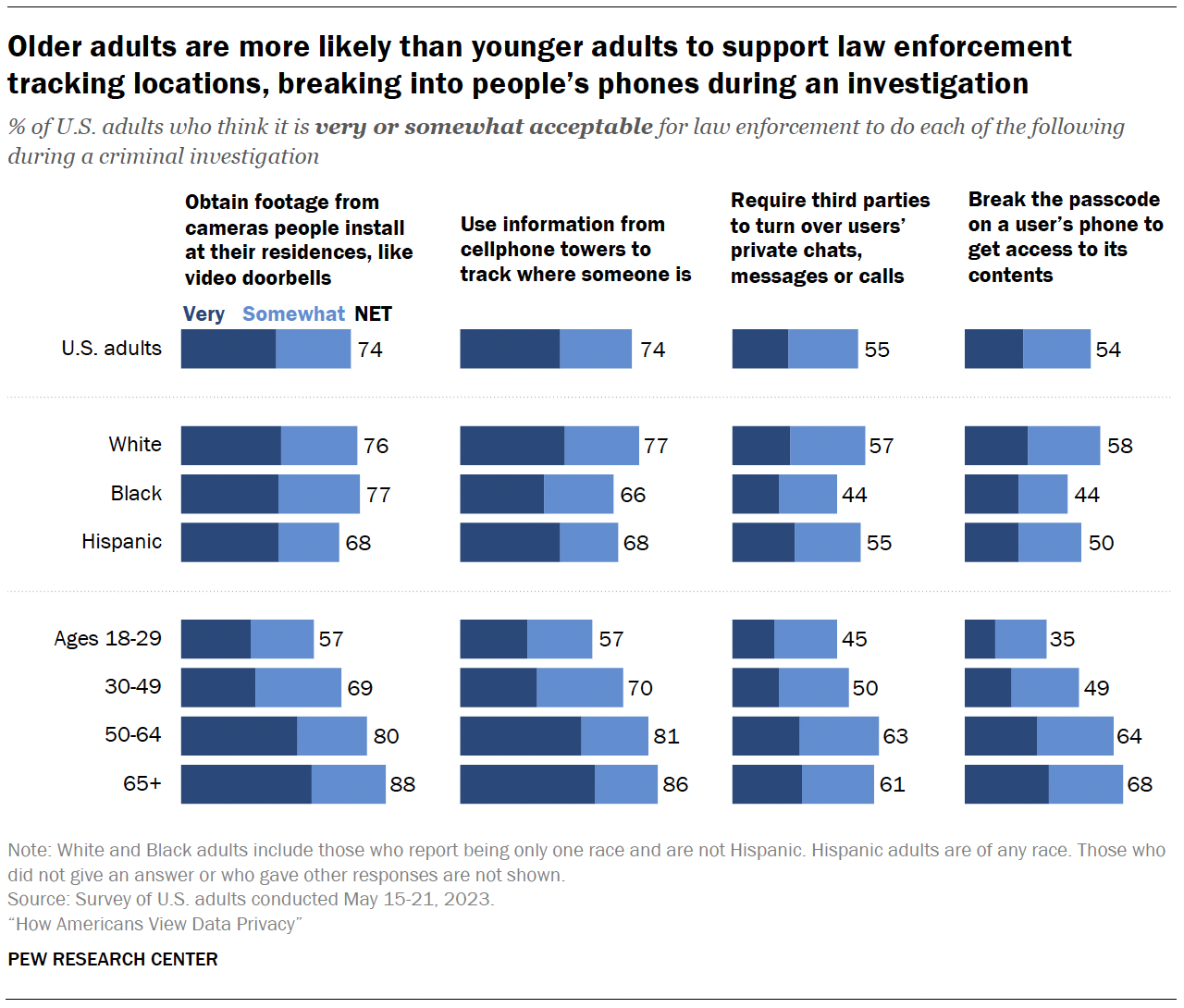
Roughly three-quarters of Americans say it’s very or somewhat acceptable for law enforcement to obtain footage from cameras people install at their residences during a criminal investigation or use information from cellphone towers to track where someone is.
By comparison, smaller shares – though still a slight majority – say it is acceptable to break the passcode on a user’s phone (54%) or require third parties to turn over users’ private chats, messages or calls (55%) during a criminal investigation. 2
About one-in-ten Americans say they aren’t sure how they feel about law enforcement doing each of these things.
Age differences
Older adults are much more likely than younger adults to say it’s at least somewhat acceptable for law enforcement to take each of these actions in criminal investigations.
For example, 88% of those 65 and older say it’s acceptable for law enforcement to obtain footage from cameras people install at their residences, compared with 57% of those ages 18 to 29.
In the case of a criminal investigation:
- White adults are more likely than Hispanic and Black adults to think it’s acceptable for law enforcement to use information from cellphone towers to track people’s locations and to break the passcode on a user’s phone to get access to its contents.
- White and Hispanic adults are more likely than Black adults to say it’s acceptable to require third parties to turn over users’ private chats, messages or calls.
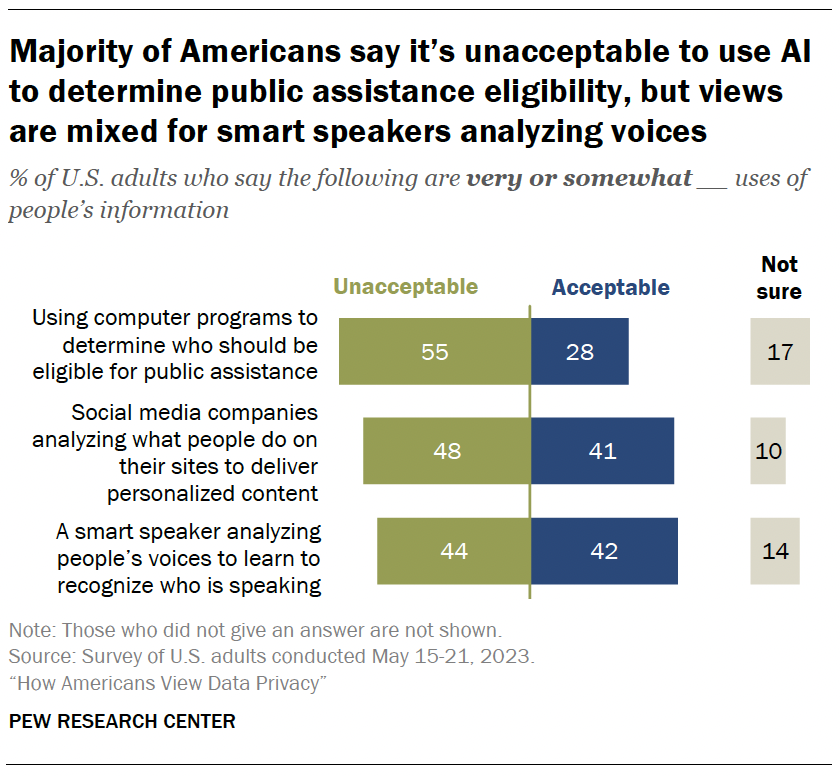
Artificial intelligence (AI) can be used to collect and analyze people’s personal information. Some Americans are wary of companies using AI in this way.
Fully 55% of adults say using computer programs to determine who should be eligible for public assistance is unacceptable. Roughly a quarter say it’s an acceptable use of AI.
Roughly half (48%) think it is unacceptable for social media companies to analyze what people do on their sites to deliver personalized content. Still, 41% are supportive of this.
Views are mixed when it comes to smart speakers analyzing people’s voices to learn who is speaking. Statistically equal shares say it’s unacceptable and acceptable (44% and 42%, respectively).
And some Americans – ranging from 10% to 17% – are uncertain about whether these uses are acceptable or not.
- 49% of adults 50 and older say it’s unacceptable for a smart speaker to analyze people’s voices to learn to recognize who’s speaking. This share drops to four-in-ten among adults under 50.
- Similarly, 56% of those 50 and older say social media companies analyzing what people do on their sites to deliver personalized content is unacceptable. But 41% of those under 50 say the same.
- There are no differences between those under 50 and those 50 and older over whether computer programs should be used to determine eligibility for public assistance.
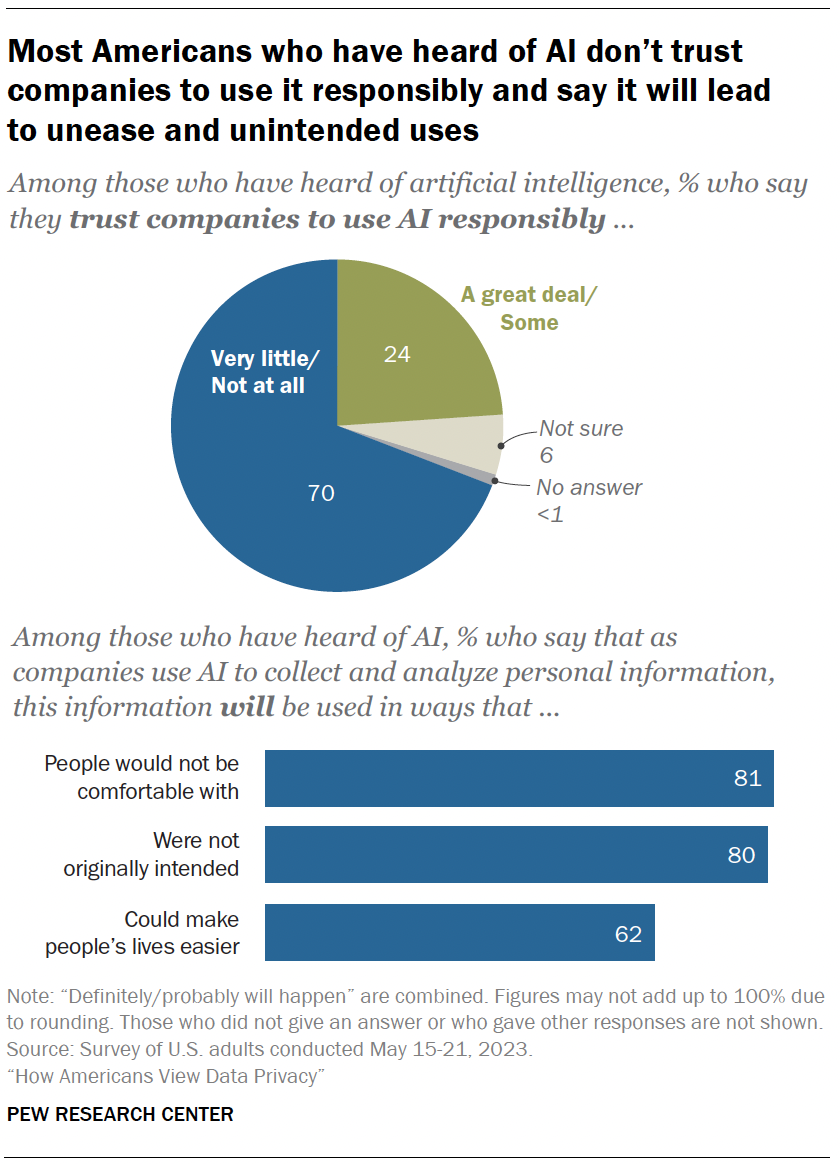
In addition to understanding people’s comfort level with certain uses of AI, the survey also measured the public’s attitudes toward companies that are utilizing AI in their products.
Among those who have heard of AI:
- 70% say they have little to no trust in companies to make responsible decisions about how they use AI in their products.
- Roughly eight-in-ten say the information will be used in ways people are not comfortable with or that were not originally intended.
- Views are more mixed regarding the potential that using AI to analyze personal details could make life easier. A majority of those who have heard of AI say this will happen (62%). Regarding differences by age, adults under 50 are more optimistic than those 50 and older (70% vs. 54%).
- 87% of those with a college degree or higher say companies will use AI to analyze personal details in ways people would not be comfortable with. Some 82% of those with some college experience and 74% with a high school diploma or less say the same.
- 88% of those with a bachelor’s degree or more say companies will use this information in ways that were not originally intended. This share drops to 80% among those with some college experience and 71% among those with a high school diploma or less.
- About three-quarters of those with a college degree or more (74%) say this information will be used in ways that could make people’s lives easier. But this share drops to 60% among those with some college experience and 52% among those with a high school diploma or less.
- This survey includes a total sample size of 364 Asian adults. The sample primarily includes English-speaking Asian adults and, therefore, it may not be representative of the overall Asian adult population. Despite this limitation, it is important to report the views of Asian adults on the topics in this study. As always, Asian adults’ responses are incorporated into the general population figures throughout this report. Asian adults are shown as a separate group when the question was asked of the full sample. Because of the relatively small sample size and a reduction in precision due to weighting, results are not shown separately for Asian adults for questions that were only asked of a random half of respondents (Form 1/Form 2). ↩
- Half of respondents were asked the questions above, and the other half received the same questions with the added context of it being a “criminal investigation where public safety is at risk.” Differences in response were largely modest. See Appendix A for these findings. ↩
Sign up for our weekly newsletter
Fresh data delivery Saturday mornings
Sign up for The Briefing
Weekly updates on the world of news & information
- Artificial Intelligence
- Online Privacy & Security
- Social Media
- Tech Companies
Social Media Fact Sheet
Teens and social media fact sheet, more americans are getting news on tiktok, bucking the trend seen on most other social media sites, life on social media platforms, in users’ own words, charting congress on social media in the 2016 and 2020 elections, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Age & Generations
- Coronavirus (COVID-19)
- Economy & Work
- Family & Relationships
- Gender & LGBTQ
- Immigration & Migration
- International Affairs
- Internet & Technology
- Methodological Research
- News Habits & Media
- Non-U.S. Governments
- Other Topics
- Politics & Policy
- Race & Ethnicity
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Copyright 2024 Pew Research Center
The New York Times
Opinion | the privacy project, the privacy project.
APRIL 10, 2019
The New York Times is launching an ongoing examination of privacy. We’ll dig into the ideas, history and future of how our information navigates the digital ecosystem and what’s at stake.
Companies and governments are gaining new powers to follow people across the internet and around the world, and even to peer into their genomes. The benefits of such advances have been apparent for years; the costs — in anonymity, even autonomy — are now becoming clearer. The boundaries of privacy are in dispute, and its future is in doubt. Citizens, politicians and business leaders are asking if societies are making the wisest tradeoffs. The Times is embarking on this monthslong project to explore the technology and where it’s taking us, and to convene debate about how it can best help realize human potential.
Does Privacy Matter?
What do they know, and how do they know it, what should be done about this, what can i do.
View all Privacy articles
Stuart A. Thompson and Charlie Warzel
One Nation, Tracked
Dec. 19, 2019
Timothy Libert
This Article Is Spying On You
Sept. 18, 2019
Agnes Callard
The Real Cost of Tweeting About My Kids
Nov. 11, 2019
Bianca Vivion Brooks
I Used to Fear Being a Nobody. Then I Left Social Media.
Oct. 1, 2019
From the Newsroom
A Surveillance Net Blankets China’s Cities, Giving Police Vast Powers
Dec. 17, 2019
Mark Bowden
The Worm That Nearly Ate the Internet
June 29, 2019
James Orenstein
I’m a Judge. Here’s How Surveillance Is Challenging Our Legal System.
June 13, 2019
Sahil Chinoy
We Built an ‘Unbelievable’ (but Legal) Facial Recognition Machine
April 16, 2019
Bill Hanvey
Your Car Knows When You Gain Weight
May 20, 2019
As Cameras Track Detroit’s Residents, a Debate Ensues Over Racial Bias
July 8, 2019
Chris Hughes
It’s Time to Break Up Facebook
May 9, 2019
The Editorial Board
Total Surveillance Is Not What America Signed Up For
Dec. 21, 2019
Glenn S. Gerstell
N.S.A. Official: We Need to Prepare for the Future of War
Sept. 13, 2019
Charlie Warzel
Amazon Wants to Surveil Your Dog
Oct. 10, 2019
15 Ways Facebook, Google, Apple and Amazon Are in Government Cross Hairs
Sept. 6, 2019
Patrick Berlinquette
I Used Google Ads for Social Engineering. It Worked.
August 4, 2019
Bekah Wells
The Trauma of Revenge Porn
May 6, 2019
Jack Poulson
I Used to Work for Google. I Am a Conscientious Objector.
April 23, 2019
Roseanna Sommers and Vanessa K. Bohns
Would You Let the Police Search Your Phone?
April 30, 2019
Now Some Families Are Hiring Coaches to Help Them Raise Phone-Free Children
July 6, 2019
Illustrations by Max Guther
More on NYTimes.com
Advertisement
- Skip to main content
- Keyboard shortcuts for audio player

- LISTEN & FOLLOW
- Apple Podcasts
- Google Podcasts
- Amazon Music
Your support helps make our show possible and unlocks access to our sponsor-free feed.
Your Technology Is Tracking You. Take These Steps For Better Online Privacy

Laurel Wamsley

Before I became a reporter at NPR, I worked for a few years at tech companies.
One of the companies was in the marketing technology business — the industry that's devoted in part to tracking people and merging their information, so they can be advertised to more effectively.
That tracking happens in multiple senses: physical tracking, because we carry our phones everywhere we go. And virtual tracking, of all the places we go online.
The more I understood how my information was being collected, shared and sold, the more I wanted to protect my privacy. But it's still hard to know which of my efforts is actually effective and which is a waste of time.
So I reached out to experts in digital security and privacy to find out what they do to protect their stuff – and what they recommend most to us regular folks.
Here's what they told me.

How Are Apple, Amazon, Facebook, Google Monopolies? House Report Counts The Ways
1. to protect your accounts, practice good security hygiene..
There are some steps that make sense for almost all of us, says Eva Galperin , director of cybersecurity at the Electronic Frontier Foundation. Those include using strong passwords, two-factor authentication, and downloading the latest security updates.
She and other experts make a distinction between privacy and security when it comes to your data. Security generally refers to protecting against someone trying to access your stuff — such as stealing your credit card number or hacking your accounts. Privacy is more often used to talk about keeping your movements from being tracked for purposes of advertising or surveillance.
It turns out that the steps to protect your security are more clear-cut than those for privacy — but we'll come back to that.

TED Radio Hour
Edward snowden: why does online privacy matter.
Use strong passwords or passphrases for your accounts. Longer than a password, passphrases should be strong and unique for each site. Don't use 1234. Bring some randomness and special characters into it. And don't use the same password for different websites: You don't want all your accounts to be compromised just because one gets hacked.
Use a password manager to keep track of your passwords, Galperin says — then all you have to do is remember the passphrase for your password manager.
Turn on two-factor authentication for your important accounts. You've seen this: Usually you're asked to put in your mobile number so that you can receive a text with an additional number you input before you can log in.
That's the most common type of two-factor authentication — but it's not the strongest, Galperin says, because SMS messages can be intercepted by your Internet provider, law enforcement or the government.
If you want to go a step further, Galperin recommends using an application that sends the second factor to an app on your phone, such as Authy or Google Authenticator , as these are harder to intercept. (Full disclosure here: NPR receives funding from Google and Facebook.) You can also use a physical key you carry with you that plugs into your computer's USB port and serves as the second factor.

6 Tips For Making A Career Change, From Someone Who Has Done It
Download the latest security updates.
Those nudges you get from your computer or phone to install the latest security update? You should download those.
"Most applications, when they're compromised, are not compromised by scary zero-day bugs that nobody knows about," Galperin says. "They are compromised by problems that everybody knows exist that have been publicly reported, and that the company has fixed and they have issued a patch in their security update. But if you do not take the security update, you do not get the benefit of the work of the security engineers at that company."

How To Sign Up To Work The Polls On Election Day
2. beware of phishing..
Not all attacks on our security come through malware or hackers invisibly breaking into your account. It's common that we're tricked into handing over our passwords or personal information to bad actors.
These attempts can happen via email, text message or a phone call. And generally they're trying to get your username and password, or perhaps your Social Security number. But there are often signs that these messages aren't legit – spelling or grammar errors, links to websites other than the one it should be linking to, or the email is coming from a weird domain.
If it feels fishy, it might be phishing.

Twitter Expands Warning Labels To Slow Spread of Election Misinformation
3. protect what matters most..
Depending on your situation, you might want to take additional precautions to safeguard your privacy and security.
To figure out what steps people should take to safeguard their stuff, Galperin suggests you make a security plan. The Electronic Frontier Foundation has a guide to doing this, which starts by asking yourself these questions:
- What do I want to protect?
- Whom do I want to protect it from?
- How bad are the consequences if I don't?
- How likely is it to need protecting?
- And how much trouble am I willing to go through to try to protect it?
Resources For Securing Your Data
The Surveillance Self-Defense site from the Electronic Frontier Foundation is a good place to start. Here's its guide to making your own security plan and figuring out what you most want to protect.
From Tactical Tech, here are handy how-to kits for different scenarios, including securing your data , increasing your online privacy and making your phone less addictive .
You can use the answers to those questions to focus your efforts on securing the things that matter most to you.
4. Delete some apps from your phone. Use a browser instead.
Matt Mitchell is a tech fellow at the Ford Foundation, and the founder of CryptoHarlem , an organization that teaches people to protect their privacy, including from surveillance.
Apps can learn a lot about you due to all the different types of data they can access via your phone. Seemingly harmless apps – like say, a flashlight app — could be selling the data they gather from you.
That's why Mitchell recommends "Marie Kondo-ing" your apps: Take a look at your smartphone and delete all the apps you don't really need. For many tasks, you can use a browser on your phone instead of an app.
Privacy-wise, browsers are preferable, because they can't access as much of your information as an app can.
I mentioned to Mitchell that even though I use Facebook and Twitter, I don't have those apps on my phone — partly so that I'll use them less, and partly for privacy reasons. I wanted to know — did I accomplish anything by not having those apps on my phone?
"You've accomplished a lot," he says. He compares it to oil companies turning crude into petrol: Your data can be turned into profit for these companies. "Every time you don't use an app, you're giving them less data, which is less money."
Mitchell says that's true even if you've been on Facebook a long time, and it feels like the company already knows everything about you. He compares it to smoking: It's never too late to cut back or quit — you'll still benefit by giving it less data to harvest.
5. To protect your chats, use an encrypted app for messaging.
If you want the contents of your messages to be secure, it's best to use an app that has end-to-end encryption, such as Signal or WhatsApp. That means you and the recipient can read the message you send — but no one in the middle.
But even though the contents of your messages are protected by encryption in apps such as Signal and WhatsApp, your metadata isn't — and someone could learn a lot about you from your metadata, Galperin warns. She compares it to what you can learn just by looking at the outside of an envelope in the mail: who sent it to whom, when and where it was sent from.
And WhatsApp is owned by Facebook — so when you share your contacts with WhatsApp, Facebook is getting that info, though it can't read the contents of your messages.
If you're on an iPhone, iMessages are encrypted when you're messaging another iOS device — but not when you're messaging an Android phone. Signal offers encrypted messaging on both Android and iPhone.
What about Facebook Messenger? Jen King , director of privacy at Stanford Law School's Center for Internet and Society, advises against using the Messenger app.
The app "has access to far more info on your phone than using Facebook through a browser," she says, recommending something such as WhatsApp or regular SMS texting instead.
And if encryption matters to you, be careful about backing up your chats to the cloud. If you back up your WhatsApp messages to iCloud or Google Drive , for example, they're no longer encrypted.
"That backup is just a database. And that database is easy for someone to open and read," Mitchell says, if they were able to access your cloud account. To keep your messages from prying eyes, turn off cloud backups and delete existing WhatsApp backups from iCloud or Google Drive.

California Rings In The New Year With A New Data Privacy Law
6. turn off ad personalization..
Whenever possible, Mitchell recommends going into your settings and turning off ad personalization, which often gives companies permission to do invasive tracking.
Opting Out Of Ad Personalization On Some Major Platforms
Google and Android
Here's a link to limit ad personalization on Google and Android.
This page shows you how to opt out of ad personalization on Apple. As of this writing, it hasn't been updated for iOS 14. If you have updated to iOS 14, go to Settings > Privacy > Apple Advertising > turn off Personalized Ads.
- On this page , you can go to the ad settings tab and toggle the settings to not allowed.
- This page has steps to disconnect your activity off Facebook that is shared with Facebook, and clear that history.
- On the Off-Facebook activity page , under What You Can Do, you can click on More Options > Manage Future Activity > and toggle it to off. ( This page has those steps.)
This page explains how to opt out of ad personalization.
He also recommends going to myactivity.google.com and deleting everything you can. On the left, there's a tab that says "Delete activity by." Select "All time." On your My Google Activity page, you can turn off Web & App Activity, Location History and YouTube History.
"It will show you every search term and everything you've ever done, every YouTube video you've ever looked at, all that stuff," he says. "It'll say, are you sure you want to delete this? 'Cause if you delete this, it might affect some stuff." Mitchell says: Delete it.
7. It's difficult to protect your privacy online if there aren't laws to protect your privacy online.
Tighter privacy settings only get you so far without laws that protect your privacy, says Ashkan Soltani , the former chief technologist for the Federal Trade Commission and one of the architects of the 2018 California Consumer Privacy Act .
Activist Aims To Strengthen California's Consumer Privacy Act
There are laws around health information and credit and financial information, he explains, and some states have Internet privacy-related laws .
But nationally, the U.S. doesn't have a universal data privacy law safeguarding everyday online privacy.
Soltani says he rarely recommends steps such as using ad blockers or VPNs for most people. They require too much attention and persistence to deliver on privacy, and even then they are limited in their effectiveness.
"The incentives are so high on the other side," Soltani says, "to uniquely identify people and track them that [users] will never have enough motivation and incentive to do it to the degree of this multibillion dollar ad tech industry."
So how do you protect your privacy? Get involved and call your congressperson, he says — tell the policymakers that you care about online privacy.
8. Start small and take it one step at a time.
Faced with this landscape, getting a tighter hold on your digital privacy and security can feel daunting. But Galperin has this sound advice: Just do a little bit at a time.
You don't need to make a list of all of your accounts to integrate into a password manager — you can just do each account as you log into it.
Even just doing the basics — strengthening your passwords, turning on two-factor authentication and watching out for scammers — can make your accounts a lot more secure. Then keep going: There are a lot of other steps you might want to take, depending on your needs.
We're going to be on the Internet for a long time. The more each of us understands how our data are collected and used — and how to keep private what we want to keep private — the better, safer and healthier our digital lives will be.
The podcast portion of this episode was produced by Audrey Nguyen. She also contributed research.
We'd love to hear from you. Leave us a voicemail at 202-216-9823, or email us at [email protected] .
For more Life Kit, subscribe to our newsletter .
- Life Kit: Life Skills
Take 10% OFF— Expires in h m s Use code save10u during checkout.
Chat with us
- Live Chat Talk to a specialist
- Self-service options
- Search FAQs Fast answers, no waiting
- Ultius 101 New client? Click here
- Messenger
International support numbers
For reference only, subject to Terms and Fair Use policies.
- How it Works
Learn more about us
- Future writers
- Explore further
Ultius Blog
Sample essay on online privacy.

Select network
The advent of the Internet age has been characterized by an unprecedented proliferation of communication and availability of information. However, the dark side is that such developments also raise questions pertaining to the ethical value of privacy: either through direct efforts by stakeholders to access confidential information or through simple ignorance on the part of Internet users, the enormous resources of the Internet also imply that the Internet, used improperly, could seriously threaten the right to individual privacy.
The present sample essay will explore some of the issues that have emerged around this subject over recent times. In particular, it will discuss the National Security Administration (NSA), Snowden, Facebook, and the value of transparency. A key theme that will emerge over the course of the exposition is that in general, Americans believe that whereas they have a right to personal privacy, organizations have a duty to respect the value of transparency. This type of document would likely be found in a tech blog or as a writing assignment .
The NSA and Snowden
To start with, then, the NSA has been in the news recently as a result of the emergence of evidence that the organization had been unlawfully spying on the communications of Americans . As the Electronic Frontier Foundation has written:
"Secret government documents, published by the media in 2013, confirm the NSA obtains full copies of everything that is carried along major domestic fiber optic cable networks" (paragraph 4).
Such operations were conducted as part of a surveillance program known as Prism. The British newspaper The Guardian was instrumental in reporting on this issue as it was in the process of emerging. For example, in a news article from 2013, Greenwald and MacAskill have written:
"The Guardian has verified the authenticity of the document, a 41-slide PowerPoint presentation—classified as top secret with no distribution to foreign allies—which was apparently used to train intelligence operatives on the capabilities of the program" (paragraph 3).
In any event, it is by now an indisputable fact that the NSA has in fact been spying on American citizens.
From a historical perspective, the activities of the NSA can be understood as related to the aftermath of the 9/11 terrorist attacks that occurred in 2001. During this time, for example, the Patriot Act was passed, which essentially consisted of provisions that infringed on civil liberties in the name of national security (see Library of Congress). The idea was that in a time of national crisis, individuals should be willing to compromise of some of the individual rights for the sake of the well-being of the broader community as a whole.
This would include the right to private communication, insofar as such privacy would potentially undermine the security of the nation. According to the Electronic Frontier Foundation, it was precisely the provisions of legislation such as the Patriot Act that the NSA has used to justify its activities; and rumors of unlawful spying have been present since at least the year 2005. It was only recently, though, that hard evidence emerged regarding these dubious activities.
The role of Edward Snowden in regards to online privacy
Edward Snowden was the man who was primarily responsible for bringing the domestic surveillance activities of the NSA to the light of the public eye. Not only did the documents leaked by Snowden reveal that the NSA had in fact been engaging in domestic surveillance, it also revealed that it was primarily ordinary Americans who had nothing to do with any kind of investigation who were getting caught by the surveillance. As Gellman, Tate, and Soltani have put it:
"Ordinary Internet users, American and non-American alike, far outnumber legally targeted foreigners in the communications intercepted by the National Security Agency from U.S. digital networks. . . . The daily lives of more than 10,000 account holders who were not targeted are catalogued and recorded nevertheless" (paragraphs 1 and 7).
In other words, the NSA was found to have violated the online privacy of Americans not simply within the context of legitimate investigations but rather as a matter of course, as if the value of individual privacy were no longer even a relevant factor to take into consideration when planning surveillance actions.
Such revelations have made a significant impact on the perceptions of Americans regarding online privacy. For example, Malden, writing on behalf of the Pew Internet Research Project, has delineated some key statistics regarding Americans' perceptions of online privacy; and among other things, it has been found that
"81% feel not very or not at all secure using social media sites when they want to share private information with another trusted person or organization," and "57% feel insecure sending private information via email" (paragraph 7).
Moreover, correlations were found between increased levels of insecurity on the one hand and greater awareness of the NSA's surveillance program on the other. In short, the events surrounding NSA and Snowden have had a strong effect on the popular culture of electronic communication within the United States. A strong majority of people now seem to take it almost for granted that some stakeholder or another is illicitly monitoring their private communications, and that they must take steps in order to protect themselves from such invasions of personal privacy. The general mindset within the nation regarding online privacy is thus marked by a very high level of suspicion and mistrust.
The case of Facebook and online privacy
At this point in the discussion, it may be useful to turn attention to a specific forum for online communication: Facebook. Despite denials from the founder of the company, there would seem to be a significant popular perception that Facebook did in fact collude with the NSA and gave up the personal information of its users to the government. Whether this is or is not true, it is rather revealing about the level of trust that Facebook users have in the integrity of the company. According to Debatin, Lovejoy, Horn, and Hughes, many Facebook users seem to exhibit an ambivalent behavioral trend in which they both report being highly aware of privacy issues and yet nevertheless upload significant amounts of personal information onto their Facebook accounts.
These researchers have addressed this issue from a somewhat anthropological perspective and concluded that the paradox can be explained by how ritualistically integrated social media sites become into users' lives:
"Social network sites deeply penetrate their users' everyday life and, as pervasive technology, tend to become invisible once they are widely adopted, ubiquitous and taken for granted" (Debatin et al. 83).
This significantly reduces users' practical concern for privacy even as they understand the concern in theory.
This also calls attention to a broader point regarding online privacy: the violation of privacy can occur not only because of direct malfeasance on the part of a given stakeholder but also due to ignorance on the part of Internet users. For example, a given Facebook user may upload compromising photographs onto his account without even thinking about the fact that (for example) his boss could access those photographs in a fully legal and legitimate way.
Something similar can be said about other forms of online communication as well: insofar as people are either not aware that they are being watched or do not take adequate action on the implications of this awareness, violations of privacy could occur in a "passive" as opposed to "active" way. That is, Internet users would make their lives essentially open to the public without even realizing they are doing so; and anyone who wanted the users' information could simply take it without even being in violation of the law. In this context, the NSA revelations may have ultimately had at least some positive effect, insofar as they have clearly contributed to Americans becoming more aware of the nature of the dangers at play (see Maden).
Privacy versus transparency
It is worth turning now to a more careful reflection on the ethical principles that are involved when discussing the subject of online privacy. In particular, one perceives something of a double standard that nevertheless is not illegitimate. On the one hand, when the NSA conducts a secret surveillance program against Americans, this is generally interpreted to mean that the NSA fundamentally lacks transparency, which is unacceptable for a governmental organization within a democratic society.
On the other, when Snowden leaks the NSA's "private" information to the public, this is generally interpreted not as an assault against the NSA's privacy but rather as a defense of the privacy of American citizens. Similarly, Facebook cannot demand that its users become "transparent" and thus willing to share private information with the public; rather, it is expected that Facebook will be transparent with its privacy policy and ensure the security of its users' information.
The general principle that emerges here, then, is that organizations are expected to be transparent toward their constituents, but that individual constituents are not therefore obliged to be transparent in turn toward the organization. This proposition would seem to be informed by a fundamentally libertarian political perspective, where libertarianism can be understood in the broadest sense as a
"political philosophy that affirms the rights of individuals to liberty, to acquire, keep, and exchange their holdings, and considers the protection of individual rights the primary role of the state" (Vallentyne and Bas van der Vossen, (paragraph 1).
Essentially, privacy is among the most individualistic of all ethical values; and whenever one insists on the value of privacy, one implicitly also insists on the priority of the individual over the community. Thus, if it is inappropriate for the NSA to spy on its own people, then this is because the NSA was only established by the constituent power of the people in the first place, and its fundamental obligation would thus be to protect the rights of those people (i.e. Americans) and not to violate those rights.
As a caveat, though, it should be noted that the extent to which this logic obtains depends to a certain extent on how much danger one imagines the community as a whole to be in. In general, when the existence of a community is threatened, emergency powers are granted to executives, and individual citizens are expected to compromise on their own rights until the danger has passed. When does this invasion of online privacy contridict the United States Consitution?
The logic here would be that if the community were to be annihilated, then this would cause serious harm to all members of the community. This would explain why it is only an appeal to national security that can even potentially justify activities such as the NSA's Prism surveillance program. In this context, Snowden's revelations may have been especially devastating because they showed that much of the information collected by the NSA had nothing to do with national security, and that the NSA thus had no right to violate its basic obligation regarding transparency.
In summary, this essay has consisted of a discussion of issues regarding online privacy in the modern United States. Subjects addressed have included the NSA and Snowden, the case of Facebook, and the interplay within the ethical values of privacy and transparency. Ultimately, these issues are related to political questions regarding the meaning of democracy, the rights and prerogatives of the individual, and the obligations that organizations have toward their constituents. Understood in this way, issues regarding online privacy merely continue discussions that have historically been in progress for quite a long time.
Does this look like one of your assignments? You can get a custom research paper on this subject from Ultius.
Works Cited
Debatin, Berhard, Jennette P. Lovejoy, Ann-Kathrin Horn, and Brittany N. Hughes. "Facebook and Online Privacy: Attitudes, Behaviors, and Unintended Consequences." Journal of Computer Mediated Communication 15 (2009): 83-108.
Electronic Frontier Foundation. NSA Spying on Americans. 2014. Web. 1 Dec. 2014. <https://www.eff.org/nsa-spying/>.
Gellman, Barton, Julie Tate, and Askan Soltani. "In NSA-Intercepted Data, Those Not Targeted Far Outnumber the Foreigners Who Are." The Washington Post 5 Jul. 2014. Web. 1 Dec. 2014. <http://www.washingtonpost.com/world/national-security/in-nsa-intercepted-data-those-not-targeted-far-outnumber-the-foreigners-who-are/2014/07/05/8139adf8-045a- 11e4-8572-4b1b969b6322_story.html>.
Greenwald, Glenn, and Ewen MacAskill. "NSA Prism Program taps in to user data of Apple, Google and Others." The Guardian 7 Jun. 2013. Web. 1 Dec. 2014.
<http://www.theguardian.com/world/2013/jun/06/us-tech-giants-nsa-data>.
Library of Congress. "H.R.3162: Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT ACT) Act of 2001." THOMAS, 2001. Web. 1 Dec. 2014. < http://thomas.loc.gov/cgi- bin/bdquery/z?d107:H.R.3162:>.
Maden, Mary. "Public Perceptions of Privacy and Security in the Post-Snowden Era." Pew Research Internet Project, 12 Nov. 2014. Web. 1 Dec. 2014. <http://www.pewinternet.org/2014/11/12/public-privacy-perceptions/#ftag=YHFb1d24ec>.
Vallentyne, Peter, and Bas van der Vossen. "Libertarianism." Stanford Encyclopedia of Philosophy. 2014. Web. 1 Dec. 2014. <http://plato.stanford.edu/entries/libertarianism/>.
https://www.ultius.com/ultius-blog/entry/sample-essay-on-online-privacy.html
- Chicago Style
Ultius, Inc. "Sample Essay on Online Privacy." Ultius | Custom Writing and Editing Services. Ultius Blog, 01 Dec. 2014. https://www.ultius.com/ultius-blog/entry/sample-essay-on-online-privacy.html
Copied to clipboard
Click here for more help with MLA citations.
Ultius, Inc. (2014, December 01). Sample Essay on Online Privacy. Retrieved from Ultius | Custom Writing and Editing Services, https://www.ultius.com/ultius-blog/entry/sample-essay-on-online-privacy.html
Click here for more help with APA citations.
Ultius, Inc. "Sample Essay on Online Privacy." Ultius | Custom Writing and Editing Services. December 01, 2014 https://www.ultius.com/ultius-blog/entry/sample-essay-on-online-privacy.html.
Click here for more help with CMS citations.
Click here for more help with Turabian citations.
Ultius is the trusted provider of content solutions and matches customers with highly qualified writers for sample writing, academic editing, and business writing.

Tested Daily
Click to Verify
About The Author
This post was written by Ultius.

- Writer Options
- Custom Writing
- Business Documents
- Support Desk
- +1-800-405-2972
- Submit bug report
- A+ BBB Rating!
Ultius is the trusted provider of content solutions for consumers around the world. Connect with great American writers and get 24/7 support.
© 2024 Ultius, Inc.
- Refund & Cancellation Policy
Free Money For College!
Yeah. You read that right —We're giving away free scholarship money! Our next drawing will be held soon.
Our next winner will receive over $500 in funds. Funds can be used for tuition, books, housing, and/or other school expenses. Apply today for your chance to win!
* We will never share your email with third party advertisers or send you spam.
** By providing my email address, I am consenting to reasonable communications from Ultius regarding the promotion.
Past winner

- Name Samantha M.
- From Pepperdine University '22
- Studies Psychology
- Won $2,000.00
- Award SEED Scholarship
- Awarded Sep. 5, 2018
Thanks for filling that out.
Check your inbox for an email about the scholarship and how to apply.

Essay on Internet Privacy
Students are often asked to write an essay on Internet Privacy in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Internet Privacy
Understanding internet privacy.
Internet privacy is about protecting your personal data online. It’s important because when you use the internet, you share information that others could misuse.
Why is Internet Privacy Important?
Internet privacy is crucial to protect your identity and personal information. Without it, strangers could access your data, leading to potential harm.

How to Maintain Internet Privacy?
You can maintain internet privacy by using strong passwords, enabling privacy settings on social media, and avoiding sharing sensitive information online. Always remember, your online safety is in your hands.
250 Words Essay on Internet Privacy
Introduction to internet privacy.
Internet privacy, often synonymous with online privacy, is a subset of data privacy focusing on the protection of personal information in the digital realm. As the internet becomes increasingly integral to our daily lives, privacy issues have surged to the forefront of societal discourse.
The Importance of Internet Privacy
Internet privacy is crucial for numerous reasons. It safeguards personal data, prevents identity theft, and preserves freedom of speech. In the era of digitalization, a breach in privacy can lead to damaging consequences, ranging from financial loss to emotional distress.
Threats to Internet Privacy
Threats to internet privacy are manifold. They include cybercriminal activities, surveillance by government agencies, data mining by corporations, and even seemingly innocuous social media platforms that collect and utilize user data.
Internet Privacy: A Human Right?
Many argue that internet privacy is a fundamental human right. This perspective highlights the need for stringent laws and policies to protect individuals from intrusive surveillance and unauthorized data collection.
The Role of Individuals in Protecting Privacy
While legislation plays a vital role, individuals must also take proactive steps to safeguard their online privacy. This can include using encrypted communication, regularly updating software, and being mindful of the information shared online.
Internet privacy is a complex and critical issue in the digital age. The collective efforts of individuals, corporations, and governments are necessary to ensure the protection of personal information in the online sphere. As we continue to navigate this interconnected world, the importance of internet privacy will only increase.
500 Words Essay on Internet Privacy
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Internet privacy is crucial for numerous reasons. Primarily, it protects individuals’ identity and personal information from potential cybercriminals. With the rise of the digital economy, people are increasingly sharing their sensitive data online, making them vulnerable to identity theft, cyberstalking, and other forms of cybercrime. Internet privacy also ensures the freedom of speech and thought online, as it allows individuals to express their views without fear of being tracked or monitored.
Despite its importance, internet privacy is under constant threat. Cybercriminals often exploit security breaches to steal sensitive data. Also, many online platforms and services thrive on data collection, often without clear consent from users. Governments, too, may infringe upon internet privacy for surveillance and security purposes.
The Role of Legislation in Internet Privacy
Legislation plays a crucial role in protecting internet privacy. Laws like the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States are examples of attempts to regulate data collection and usage. However, enforcing these laws across borders is challenging, and loopholes often exist that allow for continued privacy infringements.
Individual Responsibility and Internet Privacy
While legislation is important, individual responsibility is equally critical in ensuring internet privacy. Users should be aware of the data they share online and the potential risks involved. They should also use privacy-enhancing tools, such as Virtual Private Networks (VPNs), secure browsers, and encryption, to protect their data.
Conclusion: The Future of Internet Privacy
The future of internet privacy is uncertain. On one hand, advancements in technology, such as blockchain and quantum computing, could potentially enhance data security. On the other hand, the increasing digitization of our lives threatens to erode privacy further. The challenge lies in finding a balance between the benefits of the digital age and the preservation of privacy. As we move forward, the discourse on internet privacy will remain a pivotal aspect of our digital lives.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Uses and Abuses of Internet
- Essay on These Days Exposure to Television and Internet
- Essay on Internet Influence on Kids
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

Home — Essay Samples — Law, Crime & Punishment — Privacy & Security — Internet Privacy
Essays on Internet Privacy
The importance of writing an essay on internet privacy.
Writing an essay on internet privacy is crucial in today's digital age. With the increasing use of the internet for communication, social networking, and online transactions, the issue of privacy has become more important than ever. It is essential to educate people about the potential risks and threats to their privacy online and to advocate for stronger privacy protections.
Internet privacy is a fundamental human right, and writing an essay on this topic can help raise awareness about the importance of protecting personal information online. It can also encourage individuals to take steps to safeguard their privacy and advocate for laws and regulations that protect their rights.
When writing an essay on internet privacy, it is important to research and gather relevant information from credible sources. This may include academic journals, government reports, and reputable news outlets. It is also important to consider different perspectives and arguments on the topic to provide a well-rounded and comprehensive analysis.
Additionally, it is crucial to clearly articulate the potential risks and threats to internet privacy, such as data breaches, online surveillance, and identity theft. Providing real-life examples and case studies can help illustrate the impact of these issues on individuals and society as a whole.
Furthermore, it is essential to offer practical tips and solutions for protecting internet privacy, such as using strong passwords, enabling two-factor authentication, and being cautious about sharing personal information online. By empowering individuals with the knowledge and tools to protect their privacy, the essay can have a positive impact on the reader and the broader community.
Writing an essay on internet privacy is important for raising awareness, advocating for stronger privacy protections, and empowering individuals to safeguard their personal information online. By conducting thorough research, considering different perspectives, and providing practical solutions, the essay can help contribute to a more privacy-conscious and informed society.
- The importance of internet privacy in the digital age
In today's technology-driven world, internet privacy has become a major concern for individuals and businesses alike. With the increasing amount of personal information being shared online, it is important to understand the importance of protecting one's privacy on the internet. This essay will delve into the reasons why internet privacy is important and the potential consequences of not safeguarding one's online information.
- The evolution of internet privacy laws
Over the years, there have been significant developments in internet privacy laws as governments and regulatory bodies have recognized the need to protect individuals' personal information online. This essay will explore the evolution of internet privacy laws, including the landmark legislation and regulations that have been enacted to safeguard online privacy rights.
- The impact of social media on internet privacy
Social media has revolutionized the way we communicate and share information, but it has also raised concerns about internet privacy. This essay will examine the impact of social media on internet privacy, including the risks associated with sharing personal information on social networking platforms and the measures individuals can take to protect their privacy online.
- The role of technology in internet privacy
Advancements in technology have both enhanced and compromised internet privacy. This essay will discuss the role of technology in internet privacy, including the development of encryption tools, the rise of data breaches, and the potential implications of emerging technologies on online privacy rights.
- The ethical considerations of internet privacy
As individuals and businesses navigate the digital landscape, ethical considerations surrounding internet privacy have come to the forefront. This essay will explore the ethical implications of internet privacy, including the ethical responsibilities of organizations to protect user data and the ethical dilemmas individuals face when sharing personal information online.
- The impact of data breaches on internet privacy
Data breaches have become a prevalent threat to internet privacy, as cybercriminals continue to target organizations to access sensitive personal information. This essay will examine the impact of data breaches on internet privacy, including the potential consequences for individuals and businesses and the measures that can be taken to mitigate the risks of data breaches.
- The future of internet privacy
As technology continues to evolve, the future of internet privacy remains uncertain. This essay will speculate on the future of internet privacy, including the potential challenges and opportunities that lie ahead as individuals and organizations strive to protect their online privacy rights.
- The intersection of internet privacy and cybersecurity
Internet privacy and cybersecurity are closely intertwined, as both are essential for protecting personal information online. This essay will explore the intersection of internet privacy and cybersecurity, including the measures that can be taken to safeguard online privacy and the role of cybersecurity in mitigating privacy risks.
- The global perspective on internet privacy
Internet privacy is a universal concern, and different countries have varying approaches to protecting online privacy rights. This essay will provide a global perspective on internet privacy, including the international laws and regulations that govern internet privacy and the challenges of ensuring privacy rights in a global digital landscape.
- The responsibility of individuals in protecting their internet privacy
Ultimately, individuals play a crucial role in protecting their internet privacy. This essay will discuss the responsibility of individuals in safeguarding their online privacy, including the best practices for maintaining internet privacy and the potential consequences of neglecting online privacy protection.
The Internet Makes Children Smarter
Is google making usupid summary, made-to-order essay as fast as you need it.
Each essay is customized to cater to your unique preferences
+ experts online
The Importance of Internet Privacy and Net Neutrality to Internet Users in The Modern Era
Why internet privacy should be protected, the importance of internet privacy, the importance of staying safe on social media, let us write you an essay from scratch.
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Cyber Crime and Internet Privacy
The crucial role of internet privacy for a user, a privacy aspect to the internet of things, identifying threats and vulnerabilities in home internet connection, get a personalized essay in under 3 hours.
Expert-written essays crafted with your exact needs in mind
Human Rights on The Digital Era
Brief history of cyber security, privacy issues in a smart city, the concepts and outcomes of net neutrality, the singaporean government's ideologically conservative view on the internet, enhancing online security: qr code-based authentication for banking, secure online auction system, iot: addressing security challenges and possible solutions, analysis of the benefits of internet censorship, internet censorship as a modern way to protect the youth, internet censorship as the new 'norm', internet censorship: beneficial, but restrictive, personal outlook on the issue of internet censorship, useful alternatives for internet censorship, wikipedia censorship: the advantage for governments authorities, the data protection: how your personal information is used by organisations, businesses or the government, protect your data. then hope for a tech revolution, how technological advancement is going to affect us, should the internet be regulated: exploring possibilites to follow, should the internet be regulated: is it about net neutrality, relevant topics.
- Domestic Violence
- Serial Killer
- War on Drugs
- Animal Cruelty
- Juvenile Delinquency
- Criminal Psychology
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
Online Privacy Essays
Should we protect online privacy or share information openly, online privacy research paper, popular essay topics.
- American Dream
- Artificial Intelligence
- Black Lives Matter
- Bullying Essay
- Career Goals Essay
- Causes of the Civil War
- Child Abusing
- Civil Rights Movement
- Community Service
- Cultural Identity
- Cyber Bullying
- Death Penalty
- Depression Essay
- Domestic Violence
- Freedom of Speech
- Global Warming
- Gun Control
- Human Trafficking
- I Believe Essay
- Immigration
- Importance of Education
- Israel and Palestine Conflict
- Leadership Essay
- Legalizing Marijuanas
- Mental Health
- National Honor Society
- Police Brutality
- Pollution Essay
- Racism Essay
- Romeo and Juliet
- Same Sex Marriages
- Social Media
- The Great Gatsby
- The Yellow Wallpaper
- Time Management
- To Kill a Mockingbird
- Violent Video Games
- What Makes You Unique
- Why I Want to Be a Nurse
- Send us an e-mail

30,000+ students realised their study abroad dream with us. Take the first step today
Here’s your new year gift, one app for all your, study abroad needs, start your journey, track your progress, grow with the community and so much more.

Verification Code
An OTP has been sent to your registered mobile no. Please verify

Thanks for your comment !
Our team will review it before it's shown to our readers.

Speech on Internet Privacy

- Updated on
- Jul 2, 2021

It is rightly said that today’s era is a digital era. We may not realize it now, but the internet has become a new necessity in our lives. It has witnessed a boom like never before. In today’s time, the internet is as important to us as food, water, air is. Having said that, internet or internet privacy does have a dark side about which we must be aware of. Internet users must be well-versed in the methods for safeguarding their data on the internet. In this blog, we have brought to you a speech on internet privacy that you can refer to for your English homework, assignments, and exams.
Table of contents
What is internet privacy, speech on internet privacy: sample 1 (200-300 words), speech on internet privacy: sample 2 (400-500 words), relatable links.
Must Read: Essay on Internet: Advantages and Disadvantages
Before actually skipping onto the speech on internet privacy, let us first discuss what is meant by internet privacy. The amount of privacy protection an individual has while connected to the Internet is defined as online privacy or internet privacy. It discusses the level of internet security accessible for personal and financial information, conversations, and preferences. Internet users frequently try to enhance their online privacy by using anti-virus software, creating strong passwords, disabling tracking, evaluating site security, and selecting for tougher privacy settings. Online privacy threats vary from phishing schemes to viruses, and issues with website security can lead to identity theft. Internet privacy is a complicated topic that encompasses how your personal information is utilized, gathered, shared, and kept on your own devices and when connected to the Internet. Personal information about your habits, purchasing, and location can be gathered and shared with third parties via your phone, GPS, and other devices. Users of the internet and mobile devices have the right to know how their information will be used and to examine online privacy policies.
Also Read: Cyber Security Courses: A Detailed Guide and Top 10 Cybersecurity Skills for Beginners
Good morning everyone! I am Aryaman and today I stand before you to present an insightful and informative speech on Internet Privacy. Privacy, whether offline or online, is definitely our right, which should be demanded and expected no matter what the cost, but one might wonder why there is so much concern centered around internet privacy. Most of our lives have become virtual in the pandemic era, and all activities that were previously done offline are now done online. Be it our bank details, legal discussions with CA , or our professional work-related details, there is no guarantee that privacy on the internet is guarded.
In the year 1997, the Consumer Internet Privacy Protection Act was passed by the government as per which the consumer information shared on the internet should be safeguarded at any cost, but still, it is a matter of utmost concern and importance because the internet offers various communication tools which are frequently used and there too, the information being shared can be tracked by someone who knows how to do it and also technology has grown at a steadfast level that even our old messages that are deleted can be easily retrieved because of availability of countless apps. Certain websites use cookies that record data while we sign up or log in and, even if we are anonymous, it is relatively easy in this technologically advanced era to know our true identity, personal details, and Internet Service Provider details as well.
As a result, whatever web-based email services we use, such as Yahoo, Hotmail, or Gmail, we must be familiar with the privacy policies of those services before signing up or logging in to protect our privacy, and we must not hesitate to take action against heinous cybercrimes if we become aware of any kind of cyber abuse.
Also Read: Safer Internet Day 2021
Good morning everyone! I am Aryaman and today I stand before you to present an insightful and informative speech on Internet Privacy. We can define internet privacy as safeguarding our personal, financial, and other important information when we are online. However, after decoding the definition, one must ask, “Is internet privacy a reality or a myth?”Let us further explore this problem and crack the code. Due to the pandemic, most of our lives have now taken a virtual turn and most of our tasks, be it our work meetings, binge-watching our favorite web series, chatting with friends, online business transactions, and banking transactions, are all done online.
In real life, we only disclose information that we believe is not confidential, but in the online world, simple information such as email IDs and passwords can be traced by a skilled individual, and technology has advanced to the point where the internet and mobile phones are available to children, making them just as vulnerable as adults. After understanding the gravity of the situation, we must explore the ways in which we can ensure our online privacy. To begin with, there are a plethora of software applications that ensure online privacy, such as anti-viruses and anti-malware, and it is critical that these software applications are updated to their most recent version to avoid any sort of privacy problem. Second of all, internet history must be cleared on a regular basis. Online investments and banking transactions must be done through reliable sources only. Thirdly, online shopping must be done on reliable websites only which have credibility and authenticity, and we must avoid giving our information to those websites which don’t seem to be genuine and authentic. Also, we must keep a strong password for our email IDs and for other accounts as well.
We must be well-versed in Internet privacy laws, and if we encounter any type of online privacy issue, we must report it immediately so that the problem does not worsen. After attaining a crystal clear understanding of internet privacy, we must continually educate ourselves about this problem and be aware and prevent ourselves from having any sort of online privacy problem. In the end, I would like to say my heartiest thanks to the audience for listening to my speech on internet privacy with patience.
- Speech on Indian Education System
- Speech on Importance of English
- Generation Gap Speech for Students
- Sample Essay & Speech on Fear for ASL
- Speech on Co-Education For School Students
How did you all find the speech? Do let us know your thoughts on the same in the comments section. Also, feel free to reach our experts at Leverage Edu , to seek guidance at every step of your study abroad education journey.
Team Leverage Edu
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Contact no. *

Leaving already?
8 Universities with higher ROI than IITs and IIMs
Grab this one-time opportunity to download this ebook
Connect With Us
30,000+ students realised their study abroad dream with us. take the first step today..

Resend OTP in

Need help with?
Study abroad.
UK, Canada, US & More
IELTS, GRE, GMAT & More
Scholarship, Loans & Forex
Country Preference
New Zealand
Which English test are you planning to take?
Which academic test are you planning to take.
Not Sure yet
When are you planning to take the exam?
Already booked my exam slot
Within 2 Months
Want to learn about the test
Which Degree do you wish to pursue?
When do you want to start studying abroad.
September 2024
January 2025
What is your budget to study abroad?

How would you describe this article ?
Please rate this article
We would like to hear more.
Along with Stanford news and stories, show me:
- Student information
- Faculty/Staff information
We want to provide announcements, events, leadership messages and resources that are relevant to you. Your selection is stored in a browser cookie which you can remove at any time using “Clear all personalization” below.
If you are hoping to improve how your private personal data is seen or used, the good news is, there’s not much for you to do. That’s also, unfortunately, the bad news.
“Regrettably, there is only so much individuals can do to protect their data,” said Jennifer King , privacy and data policy fellow at the Stanford University Institute for Human-Centered Artificial Intelligence (Stanford HAI) . “It’s one of the biggest reasons why so many people in the privacy space advocate for a federal-level law. We have a patchwork of state laws to address consumer data privacy issues, but we don’t have a federal law.”
King shares ways individuals can help advocate for federal data protections, along with other tips for safeguarding your data:
Don’t think you have ‘nothing to hide’
A lot of folks think data privacy isn’t that important because they have “nothing to hide.” But the concern shouldn’t be whether data is showing you doing anything wrong or secret. The concern is the extent to which companies aggregate that data and use that to make inferences about your habits or behaviors.
Smart cars are an excellent example. They are collecting a tremendous amount of data. And we already see instances where people are facing discrimination from insurance companies because of the way these systems make judgments about your driving habits. You could say “bad drivers should pay more” but you should always be skeptical about how these systems make judgments. For example, what if the car didn’t differentiate between me and my teenager who is learning to drive?
Choose cookies and browsers wisely
We are often tracked through browsers and that’s a difficult place to cut down on data leakage. Even in contexts where you would assume that you’re dealing with first-party sites that wouldn’t sell or share your data, they often are.
The primary way to cut down on that type of data leakage is to reject browser cookies whenever possible or use a browser that tries to avoid cross-site tracking, like DuckDuckGo, Brave, or Mozilla’s Firefox.
The General Data Protection Regulation and ePrivacy Directive are pieces of legislation in Europe (that affect international sites too) that attempt to curb some of the complications surrounding cookies. With those laws, basically, companies aren’t allowed to present cookie options to you in deceptive, confusing ways. In most cases, they’ll allow you to just reject everything. It’s a huge improvement over the past but it is still only a piece of the problem with respect to protecting our data.
The argument I make, made in the white paper that we published with Stanford HAI , was that you should be able to automate these things out of your life through some kind of global preference. [More on that in the next point.]
Get familiar with Global Privacy Control
Some browsers respect a signal called Global Privacy Control, which is a setting that allows people to enact a Do Not Track signal across all their browsing in one step. Some browsers don’t offer this yet, though. In California, there’s a proposed state bill to mandate that all browsers respect Global Privacy Control.
We also passed a recent law here in California , which provides a one-stop operation for consumers to request that all registered data brokers delete their data. That moves us in the right direction, too, but we still end up with the problem where people have to know about these things and take action themselves.
Turn off your location data when you don’t need it
One of the most concerning data vulnerabilities on a mobile device is location data. I advise people to turn off GPS location when they’re not using it. (And I even sometimes struggle with this because it’s often a five- or six-step process on some phones.)
Location data is particularly sensitive because of the pattern it creates when it’s aggregated over time. A lot of people make the “nothing to hide” argument here, again. But, for example, it could track you going to medical appointments for you or your family, and those could be used to imply sensitive or inaccurate conclusions.
Location data is probably also the origin of situations where you start getting real-time ads based on a verbal conversation that you had. If you share your location with certain apps, they know when you are near one of your friends (who also has location turned on) using the same app, and the app can make inferences about your shared interests or track real-time behavior, like a search. And then you may both see ads – often in seconds – based on those assumptions. The fact that an ad may target something you didn’t even search or click on is further proof of how detailed and responsive these aggregate data profiles can be.
Don’t depend on Incognito Mode
Incognito Mode does not do what you think it does. It’s about keeping your browsing session anonymized between users of the same computer. It does not allow you to browse anonymously without any tracking. Your browser still knows what you’re doing in Incognito Mode. There was actually a recent lawsuit around the confusion that companies have created through developing those modes.
If you’re on a public computer at a library, Incognito Mode is a good thing to use, but it is not at all protecting you from any of the companies observing what you’re doing.
Cover your cameras
Covering your camera is a pretty low-threshold action to take to make sure that nobody’s running malware on your machine and recording without your knowledge. Although it’s not common, people do get targeted right for hacking attempts. I do know of somebody, personally, who had been targeted for a ransomware scheme. It happens.
Make your voice heard
If people care about the privacy of their data, they should tell their Congress members that they want to be protected from companies exploiting our data.
Politicians know data is valuable. That’s at least part of the motivation around trying to ban TikTok, in addition to concerns about national security. But many of us in the privacy space feel like we’re passing up the opportunity to address this at the right level, more broadly. There’s even a bill that was introduced last congressional session, that couldn’t get to the floor, that would do this.
California is one of the dozen or so states with a consumer privacy act (the CCPA), and voters passed Prop. 24 in 2020 to expand the law. Our new state privacy agency is still working on implementing Prop. 24, and one of the components the California Privacy Protection Agency board is figuring out right now – which is open for public comment – is around automated decision-making technology, which includes artificial intelligence. One of the things that the legislation is looking to do is give people a way to opt out if a technology is using AI for a consequential decision, like hiring or housing applications. Whether that ends up being good or bad I think depends on the context. But people should know that these decisions are happening right now if they want to weigh in.
Internet Issues: Teens, Social Media and Privacy Essay
Introduction, potential threats, influence factors, works cited.
The Internet can easily be viewed as a single greatest factor that shapes the contemporary world. Since its emergence and popularization two decades ago it has changed the way humans handle information and improved on every single aspect of our lives related to it including education, media, trade, culture, and social interactions (Pew Research Center). The growing online presence also created an unprecedented visibility opportunities, which immediately raised privacy concerns. With the increasing number of controversies surrounding the safety of personal information, the Internet has been termed by some “the final blow to privacy.” However, I argue that while it certainly changed the way we perceive safety of information, the situation may be far less grim than portrayed by sensationalist media.
It is hard to argue that the Internet opened up numerous vulnerable spots in our personal spaces. It has become extremely easy to post a silly photograph and end up being bullied by the entire country. The recent history of the Web is abundant with the cases such as the Dog Poo Girl – a woman from Korea whose photograph was published online as an attempt to persuade her to clean after her dog in the subway. Initially intended as a righteous act, the disclosure quickly got out of control and reached threatening proportions (“Dog Poo Girl”). On some occasions, such events led to tragic outcomes. In fact, Facebook is named as a reason behind the divorce in one case out of three (Chatel). Numerous examples exist where the information published online cost people their jobs (Price). To further complicate the matter, the very premise of safe online communication seems to be threatened by the recent developments in the legal sphere (Wagner). There is little doubt that privacy as we know it is under real threat.
At this point, it is worth pointing out the “as we know it” part of the allegation. I argue that it is our understanding of privacy that provides the solution and that the Internet is the biggest factor that influences it. From my personal experience, I can say that several years ago, when social network resources were gaining popularity, users (especially young ones) were absolutely reckless in setting up their accounts. Any friendship request could be confirmed instantly, and privacy policy was something utterly boring and hardly necessary. In comparison, today the majority of youth know how to configure the essential privacy settings and how to spot a suspicious link (Madden et al.).
While the former example could be interpreted by some as an illustration of the potential threat created by the Web to the inexperienced users, I suggest that it actually illustrates our pre-Internet understanding of information safety. In other words, by facing the controversial cases like that of the Dog Poo Girl, we learn to acknowledge responsibilities for sensitive information (both ours and that of others) and make conscious decisions instead of happily agreeing to everything. Essentially, prior to the emergence of the Internet, we had little opportunity to manage our information in a way that presented a feasible threat and, because of that, had only a vague idea of the concept of privacy.
Considering the information above, it would be tempting to say that the Internet taught us to handle the very threat it created. I do not think this is the case. Rather it presented the problem on the level that is easy to grasp and illustrative enough to communicate the importance of privacy to people. Safety of information has always been crucial – the Web just made it relevant and approachable enough to become a universal issue. I consider it a good thing, and while there is no doubt that it creates risks, we certainly are capable of handling them.
Chatel, Amanda. “ The Real Reason Facebook Causes One-Third of Divorces .” YourTango . 2014. Web.
“ Dog Poo Girl .” Know Your Meme , n.d. Web.
Madden, Mary, et al. “ Teens, Social Media, and Privacy .” Pew Research Center , 2013. Web.
Pew Research Center. “Internet Seen as Positive Influence on Education but Negative on Morality in Emerging and Developing Nations.” Pew Research Center . 2015.
Price, Lydia. “20 Tales of Employees Who were Fired Because of Social Media Posts.” People . 2016.
Wagner, Meg. “Congress Votes to Repeal Internet Privacy Protections.” WNEP . 2017.
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2020, September 13). Internet Issues: Teens, Social Media and Privacy. https://ivypanda.com/essays/internet-issues-teens-social-media-and-privacy/
"Internet Issues: Teens, Social Media and Privacy." IvyPanda , 13 Sept. 2020, ivypanda.com/essays/internet-issues-teens-social-media-and-privacy/.
IvyPanda . (2020) 'Internet Issues: Teens, Social Media and Privacy'. 13 September.
IvyPanda . 2020. "Internet Issues: Teens, Social Media and Privacy." September 13, 2020. https://ivypanda.com/essays/internet-issues-teens-social-media-and-privacy/.
1. IvyPanda . "Internet Issues: Teens, Social Media and Privacy." September 13, 2020. https://ivypanda.com/essays/internet-issues-teens-social-media-and-privacy/.
Bibliography
IvyPanda . "Internet Issues: Teens, Social Media and Privacy." September 13, 2020. https://ivypanda.com/essays/internet-issues-teens-social-media-and-privacy/.
- People's Irresponsibility Towards Dogs
- Dogs, Their History, and Bonding with Human
- Understanding Teen Depression
- Internet Monopolies: Everybody Wants to Rule the World
- Wireless Networks' Historical Development
- Electronic Nature of Information Systems
- Mobile Internet and Its Economics
- Recommender Systems of Internet
Featured Article
Two Santa Cruz students uncover security bug that could let millions do their laundry for free
Csc serviceworks provides laundry machines to thousands of residential homes and universities, but the company ignored requests to fix a security bug..

A pair of university students say they found and reported earlier this year a security flaw allowing anyone to avoid paying for laundry provided by over a million internet-connected laundry machines in residences and college campuses around the world.
Months later, the vulnerability remains open after CSC ServiceWorks repeatedly ignored requests to fix the flaw.
UC Santa Cruz students Alexander Sherbrooke and Iakov Taranenko told TechCrunch that the vulnerability they discovered allows anyone to remotely send commands to laundry machines run by CSC and operate laundry cycles for free.
Sherbrooke said he was sitting on the floor of his basement laundry room in the early hours one January morning with his laptop in hand and “suddenly having an ‘oh s—’ moment.” From his laptop, Sherbrooke ran a script of code with instructions telling the machine in front of him to start a cycle despite having $0 in his laundry account. The machine immediately woke up with a loud beep and flashed “PUSH START” on its display, indicating the machine was ready to wash a free load of laundry.
In another case, the students added an ostensible balance of several million dollars into one of their laundry accounts, which reflected in their CSC Go mobile app as though it were an entirely normal amount of money for a student to spend on laundry.
CSC ServiceWorks is a large laundry service company, touting a network of over a million laundry machines installed in hotels, university campuses, and residences across the United States, Canada and Europe.
Since CSC ServiceWorks does not have a dedicated security page for reporting security vulnerabilities, Sherbrooke and Taranenko sent the company several messages through its online contact form in January but heard nothing back from the company. A phone call to the company landed them nowhere either, they said.
The students also sent their findings to the CERT Coordination Center at Carnegie Mellon University, which helps security researchers disclose flaws to affected vendors and provide fixes and guidance to the public.
The students are now revealing more about their findings after waiting longer than the customary three months that security researchers typically grant vendors to fix flaws before going public. The pair first disclosed their research in a presentation at their university cybersecurity club earlier in May.
It’s unclear who, if anyone, is responsible for cybersecurity at CSC, and representatives for CSC did not respond to TechCrunch’s requests for comment.
The student researchers said the vulnerability is in the API used by CSC’s mobile app, CSC Go . An API allows apps and devices to communicate with each other over the internet. In this case, the customer opens the CSC Go app to top up their account with funds, pay, and begin a laundry load on a nearby machine.
Sherbrooke and Taranenko discovered that CSC’s servers can be tricked into accepting commands that modify their account balances because any security checks are done by the app on the user’s device and are automatically trusted by CSC’s servers. This allows them to pay for laundry without actually putting real funds in their accounts.
By analyzing the network traffic while logged in and using the CSC Go app, Sherbrooke and Taranenko found they could circumvent the app’s security checks and send commands directly to CSC’s servers, which are not available through the app itself.
Technology vendors like CSC are ultimately responsible for making sure their servers are performing the proper security checks; otherwise it’s akin to having a bank vault protected by a guard who doesn’t bother to check who is allowed in.
The researchers said potentially anyone can create a CSC Go user account and send commands using the API because the servers are also not checking if new users owned their email addresses. The researchers tested this by creating a new CSC account with a made-up email address.
With direct access to the API and referencing CSC’s own published list of commands for communicating with its servers , the researchers said it is possible to remotely locate and interact with “every laundry machine on the CSC ServiceWorks connected network.”
Practically speaking, free laundry has an obvious upside. But the researchers stressed the potential dangers of having heavy-duty appliances connected to the internet and vulnerable to attacks. Sherbrooke and Taranenko said they were unaware if sending commands through the API can bypass the safety restrictions that modern laundry machines come with to prevent overheating and fires. The researchers said someone would have to physically push the laundry machine’s start button to begin a cycle; until then, the settings on the front of the laundry machine cannot be changed unless someone resets the machine.
CSC quietly wiped out the researchers’ account balance of several million dollars after they reported their findings, but the researchers said the bug remains unfixed and it’s still possible for users to “freely” give themselves any amount of money.
Taranenko said he was disappointed that CSC did not acknowledge their vulnerability.
“I just don’t get how a company that large makes those types of mistakes, then has no way of contacting them,” he said. “Worst-case scenario, people can easily load up their wallets and the company loses a ton of money. Why not spend a bare minimum of having a single monitored security email inbox for this type of situation?”
But the researchers are undeterred by the lack of response from CSC.
“Since we’re doing this in good faith, I don’t mind spending a few hours waiting on hold to call their help desk if it would help a company with its security issues,” said Taranenko, adding that it was “fun to get to do this type of security research in the real world and not just in simulated competitions.”
How a simple security bug became a university campus ‘master key’
More TechCrunch
Get the industry’s biggest tech news, techcrunch daily news.
Every weekday and Sunday, you can get the best of TechCrunch’s coverage.
Startups Weekly
Startups are the core of TechCrunch, so get our best coverage delivered weekly.
TechCrunch Fintech
The latest Fintech news and analysis, delivered every Sunday.
TechCrunch Mobility
TechCrunch Mobility is your destination for transportation news and insight.
EU Council gives final nod to set up risk-based regulations for AI
It’s a wrap: European Union lawmakers have given the final approval to set up the bloc’s flagship, risk-based regulations for artificial intelligence.

Vitesse, a payments and treasury management platform for insurers, raises $93M to fuel US expansion
London-based fintech Vitesse has closed a $93 million Series C round of funding led by investment giant KKR.

Zen Educate raises $37M and acquires Aquinas Education as it tries to address the teacher shortage
Zen Educate, an online marketplace that connects schools with teachers, has raised $37 million in a Series B round of funding. The raise comes amid a growing teacher shortage crisis…

Scarlett Johansson says that OpenAI approached her to use her voice
“When I heard the released demo, I was shocked, angered and in disbelief that Mr. Altman would pursue a voice that sounded so eerily similar to mine.”

Aurora and Volvo unveil self-driving truck designed for a driverless future
A new self-driving truck — manufactured by Volvo and loaded with autonomous vehicle tech developed by Aurora Innovation — could be on public highways as early as this summer. The…

ETF Partners raises €284M for climate startups that will be effective quickly — not 20 years down the road
The European venture capital firm raised its fourth fund as fund as climate tech “comes of age.”

Microsoft wants to make Windows an AI operating system, launches Copilot+ PCs
Copilot, Microsoft’s brand of generative AI, will soon be far more deeply integrated into the Windows 11 experience.

TechCrunch Space: Star(side)liner
Hello and welcome back to TechCrunch Space. For those who haven’t heard, the first crewed launch of Boeing’s Starliner capsule has been pushed back yet again to no earlier than…
These 81 robotics companies are hiring
When I attended Automate in Chicago a few weeks back, multiple people thanked me for TechCrunch’s semi-regular robotics job report. It’s always edifying to get that feedback in person. While…

VinFast crash that killed family of four now under federal investigation
The top vehicle safety regulator in the U.S. has launched a formal probe into an April crash involving the all-electric VinFast VF8 SUV that claimed the lives of a family…

NYC-Dublin real-time video portal reopens with some fixes to prevent inappropriate behavior
When putting a video portal in a public park in the middle of New York City, some inappropriate behavior will likely occur. The Portal, the vision of Lithuanian artist and…

Contour Venture Partners, an early investor in Datadog and Movable Ink, lowers the target for its fifth fund
Longtime New York-based seed investor, Contour Venture Partners, is making progress on its latest flagship fund after lowering its target. The firm closed on $42 million, raised from 64 backers,…

Meta’s Oversight Board takes its first Threads case
Meta’s Oversight Board has now extended its scope to include the company’s newest platform, Instagram Threads, and has begun hearing cases from Threads.

SeekOut, a recruiting startup last valued at $1.2 billion, lays off 30% of its workforce
The company says it’s refocusing and prioritizing fewer initiatives that will have the biggest impact on customers and add value to the business.

UK’s autonomous vehicle legislation becomes law, paving the way for first driverless cars by 2026
The U.K.’s self-proclaimed “world-leading” regulations for self-driving cars are now official, after the Automated Vehicles (AV) Act received royal assent — the final rubber stamp any legislation must go through…

ChatGPT: Everything you need to know about the AI-powered chatbot
ChatGPT, OpenAI’s text-generating AI chatbot, has taken the world by storm. What started as a tool to hyper-charge productivity through writing essays and code with short text prompts has evolved…

Fintech lender SoLo Funds is being sued again by the government over its lending practices
SoLo Funds CEO Travis Holoway: “Regulators seem driven by press releases when they should be motivated by true consumer protection and empowering equitable solutions.”

Rollup wants to be the hardware engineer’s workhorse
Hard tech startups generate a lot of buzz, but there’s a growing cohort of companies building digital tools squarely focused on making hard tech development faster, more efficient and —…

Disrupt Audience Choice vote closes Friday
TechCrunch Disrupt 2024 is not just about groundbreaking innovations, insightful panels, and visionary speakers — it’s also about listening to YOU, the audience, and what you feel is top of…

Google is launching a new Android feature to drive users back into their installed apps
Google says the new SDK would help Google expand on its core mission of connecting the right audience to the right content at the right time.

Jolla debuts privacy-focused AI hardware
Jolla has taken the official wraps off the first version of its personal server-based AI assistant in the making. The reborn startup is building a privacy-focused AI device — aka…

ChatGPT’s mobile app revenue saw its biggest spike yet following GPT-4o launch
The ChatGPT mobile app’s net revenue first jumped 22% on the day of the GPT-4o launch and continued to grow in the following days.

Bumble buys community building app Geneva to expand further into friendships
Dating app maker Bumble has acquired Geneva, an online platform built around forming real-world groups and clubs. The company said that the deal is designed to help it expand its…

CyberArk snaps up Venafi for $1.54B to ramp up in machine-to-machine security
CyberArk — one of the army of larger security companies founded out of Israel — is acquiring Venafi, a specialist in machine identity, for $1.54 billion.

OpenseedVC, which backs operators in Africa and Europe starting their companies, reaches first close of $10M fund
Founder-market fit is one of the most crucial factors in a startup’s success, and operators (someone involved in the day-to-day operations of a startup) turned founders have an almost unfair advantage…

Pine Labs gets Singapore court approval to shift base to India
A Singapore High Court has effectively approved Pine Labs’ request to shift its operations to India.

UK opens office in San Francisco to tackle AI risk
The AI Safety Institute, a U.K. body that aims to assess and address risks in AI platforms, has said it will open a second location in San Francisco.

Why companies are turning to internal hackathons
Companies are always looking for an edge, and searching for ways to encourage their employees to innovate. One way to do that is by running an internal hackathon around a…

I’m rooting for Melinda French Gates to fix tech’s broken ‘brilliant jerk’ culture
Women in tech still face a shocking level of mistreatment at work. Melinda French Gates is one of the few working to change that.

Blue Origin successfully launches its first crewed mission since 2022
Blue Origin has successfully completed its NS-25 mission, resuming crewed flights for the first time in nearly two years. The mission brought six tourist crew members to the edge of…


IMAGES
VIDEO
COMMENTS
Over 30 years ago, Mason (Citation 1986) voiced ethical concerns over the protection of informational privacy, or "the ability of the individual to personally control information about one's self" (Stone et al., Citation 1983), calling it one of the four ethical issues of the information age.Since the 1980s, scholars have remained concerned about informational privacy, especially given ...
Get custom essay. Ultimately, the importance of internet privacy extends beyond individual convenience; it is a fundamental right that underpins our freedom, security, and individuality in the digital age. By recognizing the significance of internet privacy and taking meaningful steps to protect it, we can ensure that the digital landscape ...
Anonymity on the Internet is possible, but it isn't guaranteed. To do it right, a person needs to know what pieces of information are used to track a user. Cookies, IP addresses, and media access control (MAC) addresses are some of the bits of information to mask, because they can point back to a real person.
Power over others' privacy is the quintessential kind of power in the digital age. T wo years after it was funded and despite its popularity, Google still hadn't developed a sustainable business model. In that sense, it was just another unprofitable internet startup. Then, in 2000, Google launched AdWords, thereby starting the data economy.
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data ...
Online privacy definition. Online privacy, also known as internet privacy or digital privacy, refers to how much of your personal, financial, and browsing data remains private when you're online. It has become a growing worry, with browsing history and personal data at increased risk.
1. Views of data privacy risks, personal data and digital privacy laws. Online privacy is complex, encompassing debates over law enforcement's data access, government regulation and what information companies can collect. This chapter examines Americans' perspectives on these issues and highlights how views vary across different groups ...
Levels of privacy. Internet and digital privacy are viewed differently from traditional expectations of privacy. Internet privacy is primarily concerned with protecting user information. Law Professor Jerry Kang explains that the term privacy expresses space, decision, and information. In terms of space, individuals have an expectation that their physical spaces (e.g. homes, cars) not be intruded.
Companies and governments are gaining new powers to follow people across the internet and around the world, and even to peer into their genomes. The benefits of such advances have been apparent ...
Online privacy is based on personal information that should not be allowed to settle in the hands of third parties. This information is critical, and the internet user or the person in charge of keeping such information in an organization should always ensure no one gets access. When users are asked to provide personal information while using ...
The user should have knowledge of how his or her information is being collected, the purpose of collection and how the party is going to use the information.
Get involved and call your congressperson, he says — tell the policymakers that you care about online privacy. 8. Start small and take it one step at a time. Faced with this landscape, getting a ...
The present paper has evaluated several methodologies through which users can guarantee privacy on the internet. Some of the methodologies discussed include employing strong passwords, making use of antivirus software, using secure systems, safe Internet browsing, avoiding fake websites and avoiding phishing sites.
People can protect their online privacy by limiting the information that they share, and by adopting privacy protective measures (Baruh et al., 2017; Büchi et al., 2017). A meta-analysis of several studies concerning online privacy showed that these two behaviors do not seem to be related (Baruh et al., 2017).
Conclusion. In summary, this essay has consisted of a discussion of issues regarding online privacy in the modern United States. Subjects addressed have included the NSA and Snowden, the case of Facebook, and the interplay within the ethical values of privacy and transparency. Ultimately, these issues are related to political questions ...
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Internet privacy is a universal concern, and different countries have varying approaches to protecting online privacy rights. This essay will provide a global perspective on internet privacy, including the international laws and regulations that govern internet privacy and the challenges of ensuring privacy rights in a global digital landscape.
The internet age has fueled unprecedented levels of personal information sharing, sparking debates regarding online privacy. While some argue staunchly that protecting privacy is vital, others insist embracing openness by sharing data enables progress.
Internet privacy is a complicated topic that encompasses how your personal information is utilized, gathered, shared, and kept on your own devices and when connected to the Internet. Personal information about your habits, purchasing, and location can be gathered and shared with third parties via your phone, GPS, and other devices.
Purism is a company that offers the Librem line of Linux-based laptops built with privacy and security in mind. As with Apple, however, it comes at a cost. The Librem laptop starts at around ...
Internet privacy is the security of a user's personal data that is stored or published on the internet. The internet is an important part of every individual's daily life. In today's society, the internet is used by many different people for many reasons. It can be used for research, communication, and purchasing items.
The Internet has become a great tool that is used almost by every person in the world. It changed the way how people live. With surfing the web, people share data about themselves.
7 ways to keep your data safe (er) Our data protection problem requires a federal-level solution, says Jennifer King. But there are some things you can do to safeguard your privacy online. If you ...
This first AI in Focus report presents research findings about the utility of social media-style video as a supplement to text-based privacy notices. A meaningful consent process online requires that a digital service provider communicate information about services to consumers.
The growing online presence also created an unprecedented visibility opportunities, which immediately raised privacy concerns. With the increasing number of controversies surrounding the safety of personal information, the Internet has been termed by some "the final blow to privacy.". However, I argue that while it certainly changed the way ...
Internet Connection: Bluebook is designed to work with an intermittent connection to the internet. An internet connection is required to start the test and to submit answers at the end of the test. You will receive instructions from your proctor on test day if there is an outage. Modules: Each section of the SAT is made up of 2 modules.
ChatGPT, OpenAI's text-generating AI chatbot, has taken the world by storm. What started as a tool to hyper-charge productivity through writing essays and code with short text prompts has evolved…
If you use the Internet Explorer browser, choose Save Target As. If you use Firefox, Chrome or Safari, choose Save Link As . After you have downloaded the MP3 file, double-click on the file name to play it.